- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Enhanced Security Measures in Place: To ensure a safer experience, we’ve implemented additional, temporary security measures for all users.
Unlock your full community experience!
Upgrading VM Series Firewalls Behind Load Balancer in AWS
- LIVEcommunity
- Articles
- General Articles
- Upgrading VM Series Firewalls Behind Load Balancer in AWS
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-28-2023 09:49 PM - edited 09-28-2023 10:28 PM
Have you ever encountered discussions about planning a VM series upgrade or wondered about the fate of existing connections during a firewall upgrade? How can firewalls be upgraded with minimal impact and downtime? This article aims to address these queries and provide guidelines for an upgrade process.
Modern businesses employ the Gateway Load Balancer framework to incorporate security insertion. You have the ability to customize health check preferences for specific target groups. By default, general settings are in place unless changed during the initial creation of the target group or in subsequent adjustments. The Gateway Load Balancer actively monitors the well-being of targets within active Availability Zones and routes requests to those healthy targets.
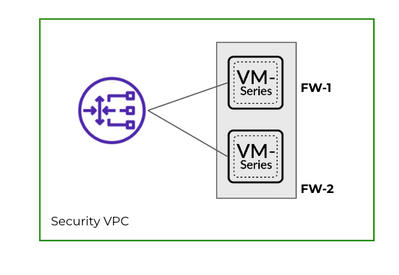
For the purpose of this article, let us consider a topology where we have 2 VM Series firewalls: FW-1, FW-2 as part of a target group, deployed behind a GWLB . Both these firewalls show as healthy in the target group.
To upgrade the firewalls, You can take into consideration below factors to ensure minimal downtime.
1. De-Register FW-2 from the Target Groups (Check if the firewall is part of multiple ALB target-groups and de-register it from all). When you deregister a target, it is taken out of your target group. The Gateway Load Balancer ceases to direct traffic to a target immediately upon de-registration. The target enters the draining state. The GWLB waits for the de-registration delay timer (attribute of Target Group) to change the state of a de-registering target from draining to unused. The default value is 300 seconds (5 min). It can be modified in the target group settings. The range is 0-3600 seconds.
During this time of de-registration delay timer any new connections would not be forwarded to it by GWLB.
Existing connections get specified seconds to complete. Post the delay timer, existing connections will be forcefully terminated as well. Hence if there are any remaining sessions they will experience disconnection.
2. After waiting for the de-registration delay timer, FW-2 should stop receiving any traffic. and now we can upgrade the VM series and reboot. There is no downtime since the FW-1 will handle all the connections.
3. Once the FW-2 is back, register it in the target group. This Firewall should show up as healthy in the Health Check of. FW-2 is ready to accept the connections at this stage.
4. The new connections can now be forwarded to FW-2 by GWLB.
We can now repeat the same steps from step 1-3 and deregister FW-1 from GWLB so that it enters the de-registration delay timer. We will upgrade the firewall, reboot and add it back to the target group to start processing traffic.
There is very minimal downtime experienced if the upgrade is carried out in this manner. You can follow these guidelines for multiple firewalls. It is always recommended to take backup of configuration before performing any maintenance activity.
Note: For more information on how to rebalance existing flows in case the target is in de-registration / unhealthy state, please refer to the AWS article: Introducing AWS Gateway Load Balancer Target Failover for Existing Flows
- 5388 Views
- 1 comments
- 1 Likes
- Support FAQ: How to Handle High Data Plane CPU Issues in Support FAQ
- Using XFF Headers with VM-Series on GCP in General Articles
- Get Started with VM-Series with AWS Gateway Load Balancer - A PoC Playbook Guide in General Articles
- Keeping Your Google Cloud VPC Networks Highly Resilient and Secured in General Articles
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
2 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Collector Group
1 -
Commit Process
1 -
Community News
1 -
Configuration
9 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
5 -
COVID-19
1 -
CPSP
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
2 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
Events
1 -
expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
2 -
Focused Services Proactive Insights
1 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
Github
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
1 -
Log Collector Design
1 -
Log Forwarding
1 -
Log4Shell
1 -
Logging
2 -
login
1 -
Logs
3 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
microsoft
2 -
Microsoft 365
1 -
minemeld
25 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NetSec
1 -
NetSec Newsletter
1 -
Network Security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
newsletter
2 -
Next Generation Firewall
2 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
4 -
NGFW
25 -
NGFW Configuration
10 -
NGFW Newsletter
1 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
17 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
Panorama
8 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
Prisma Access
5 -
Prisma SD-WAN
1 -
proactive insights
1 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
7 -
Site-to-Site VPN
1 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
Tags
2 -
Terraform
2 -
TGW
3 -
threat log
1 -
Threat Prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
troubleshooting
5 -
tunnel
2 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
Upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
6 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
4 -
Vulnerability Protection
1 -
Webinar
1 -
WildFire
3 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next