- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Destination NAT with different subnet of Outside interface.
- LIVEcommunity
- Discussions
- General Topics
- Re: Destination NAT with different subnet of Outside interface.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Destination NAT with different subnet of Outside interface.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2014 11:39 PM
Hello,
Outside interface of Palo Alto firewall is configured with aaa.bbb.ccc.ddd /30 subnet.
I have some servers in DMZ those need to be accessed via internet with IP address(es)/subnet ZZZ.XXX.YYY.VVV/24.
I have configured Destination Nat( including Security Policy) for these servers with the IP addresses as mentioned above.
Please let me know how this can work? Do we need to add static route on upstream router for new subnet?
Regards,
- Labels:
-
Configuration
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2014 12:39 AM
so you mean zzz.xxx.yyy.vvv/24 is public ip subnet also ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2014 12:44 AM
Yes, zzz.xxx.yyy.vvv/24 is public subnet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2014 01:11 AM
ok so when accessing this /24 subnet from internet that traffic should come to aaa.bbb.ccc.ddd /30's interface(upstream should route that traffic)
you can add this /24 subnet to the outside interface as second.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2014 03:15 AM
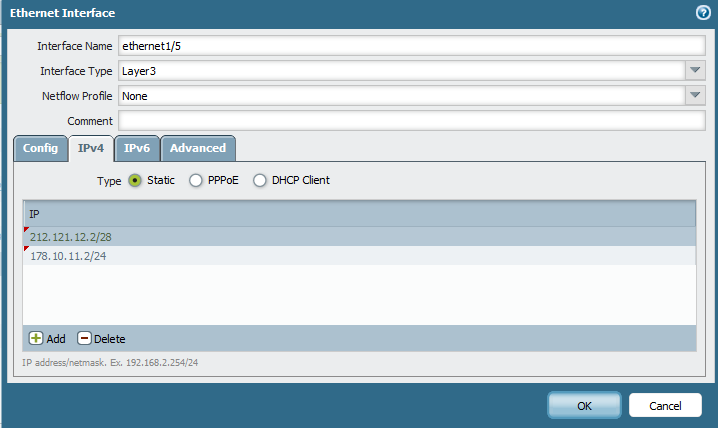
panos, would please let me know how we can add secondary IP address to Outside interface of FW?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2014 01:00 AM
panos, I have configured upstream router with static routes for secondary subnet towards outside interface of PA FW.
Apart from this Destination Nat is configured with Security Policies to allow the traffic.
Would you please let us know how to troubleshoot? still the servers are not accessible from internet form secondary subnet.
Regards,
Parvez
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2014 01:44 AM
you may use packet capture to troubleshoot while accessing from outside to that secondary subnet
so that we'll see if traffic comes(and we drop) or not
if not so problem is related to upstream
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2014 03:04 AM
be careful about the rule
you have to create the rule from internet to DMZ base on the ZZZ.XXX.YYY.VVV/24 ip and not on the NAT ip.
if you have a rule like deny all at the bottom of the rule list, you will see if a deny action is present in the traffic log.
regard's
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2014 04:47 AM
Keep that in mind :
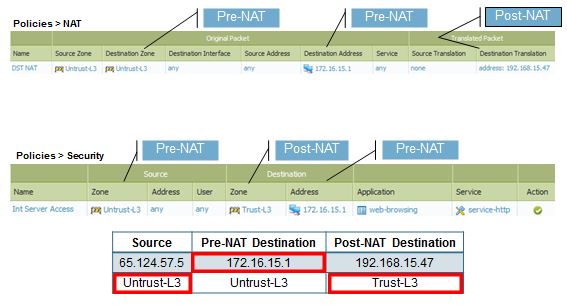
Hope help
V.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2014 04:54 AM
Gregoux, If I will put deny all at the bottom, Do we need to allow separate rules outside to outside, DMZ to DMZ and Inside to inside for all traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2014 04:58 AM
Thanks a lot. I created the rules as mentioned in this snapshot.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2014 04:43 AM
Thanks a lot . The migration was successful.
- 9079 Views
- 13 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Best practices for Palo Alto security policy when destination IP/FQDN is dynamic or unknown in Next-Generation Firewall Discussions
- About PAN-303627 in Next-Generation Firewall Discussions
- Question on PA-440 Failover in General Topics
- IPSEC VPN for the FW MGMT in Next-Generation Firewall Discussions
- Push Cortex XDR datasets/logs to dedicated syslog server in Cortex XDR Discussions