- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
XML API - Get thret ID and CVE (version 8.0)
- LIVEcommunity
- Community Legacy Content
- Automation / API
- Automation/API Discussions
- XML API - Get thret ID and CVE (version 8.0)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
XML API - Get thret ID and CVE (version 8.0)
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-13-2017 12:26 AM
Hello.
Working with firewalls on version 7 with a query to the following path: xpath=/config/predefined/threats/vulnerability I was able to get an XML with CVE of every threat, but on version 8 XML doen't contain associated CVE.
Are any other path to get threat ID/CVE from the API?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-14-2017 09:47 AM
Hello,
I confirmed this on my firewalls, PAN-OS 7.1 shows threat metadata and PAN-OS 8.0 only has the threat name. Looking into it and will let you know. Thanks for your patience.
Thanks,
-Brian
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-14-2017 12:20 PM - edited 07-14-2017 12:20 PM
This has been opened as issue PAN-81194. We'll investigate and if it turns out to be a bug we will push a fix into a future 8.0.x maintenance release.
Unfortunately, I don't know of a workaround at this time, but will let you know if I come up with anything.
Thanks for your help!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2017 09:56 AM
Looks like this just got fixed today in the PAN-OS 8.0.4 release (PAN-76042). Good work, @btorresgil.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2017 11:42 AM
Glad to help, and thanks for your patience.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-23-2017 03:53 AM
Hello again.
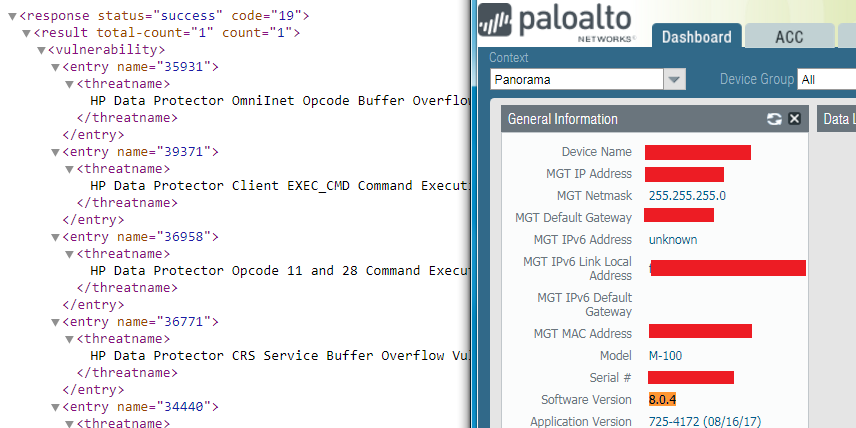
On version 8.0.4 I continue having the same problem:
How can I solve it?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2017 08:41 PM - edited 09-18-2017 08:54 PM
PAN-OS 8.0 depletes CVE information from old XPATH
For 8.0.4 onward, please use new XPATH in op command.
type=op&cmd=<show><predefined><xpath>/predefined/threats/vulnerability</xpath>
Example of working output
<response status="success"><result><vulnerability>
<entry name="35931" p="yes">
<threatname>HP Data Protector OmniInet Opcode Buffer Overflow Vulnerability</threatname>
<cve xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<member>CVE-2011-1865</member>
</cve>
<category>overflow</category>
<severity>high</severity>
<affected-host>
<server>yes</server>
</affected-host>
<default-action>alert</default-action>
</entry>
....
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2019 11:36 AM
The example above is close, not sure if some of it got stripped out. This works for me on latest versions V8 and higher.
https[:]//IPADDRESS/api/?key=YOURKEY&type=op&cmd=<show><predefined><xpath>/predefined/threats/vulnerability</xpath></predefined></show>
- 8827 Views
- 7 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Panorama Nat Policy group - nat_rule_group not working in Automation/API Discussions
- issues with concurrent api call in Automation/API Discussions
- Ansible PFX Cert Upload not adding key in Automation/API Discussions
- panos remove address object script messes up the device group setup. in Automation/API Discussions
- API Call to gather Vsys Stats in Automation/API Discussions