- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
BPA Release Notes v3.17
- LIVEcommunity
- Community Legacy Content
- Best Practice Assessment
- Best Practice Assessment Release Notes
- BPA Release Notes v3.17
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
v3.17.0 - Released on 8/13/2019
New Features
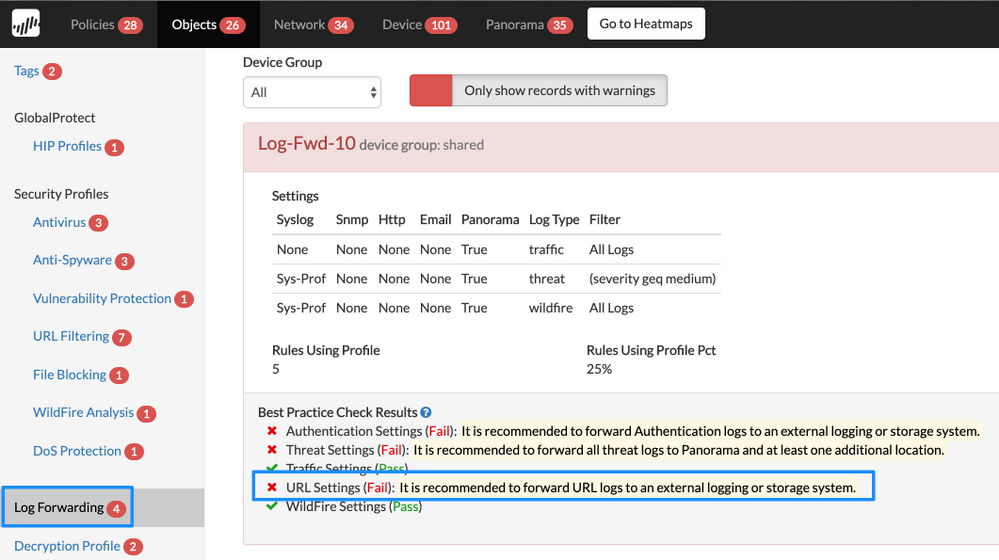
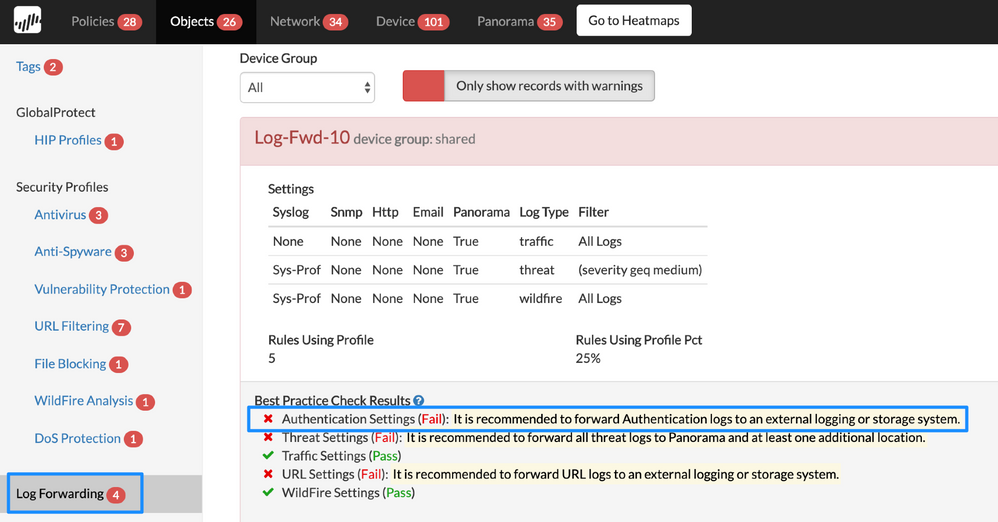
Log Forwarding URL Settings
Details: When you create Log Forwarding profiles, forward URL logs to Panorama or another logging system, such as a syslog, SNMP, email, or HTTP server, so you can ensure URL activity logs are retained for a certain duration for compliance reasons, identifying URL activity that was not expected, and any web traffic pattern of compromised systems.
Log Forwarding Authentication Settings
Details: When you create Log Forwarding profiles, forward Authentication logs to Panorama or another external logging space, such as a syslog, SNMP, email, or HTTP server, so you can ensure any resources accessed through authentication is recorded and saved for compliance, identifying and correcting authentication policies if extra resources are provided than needed and if any future incident handling.
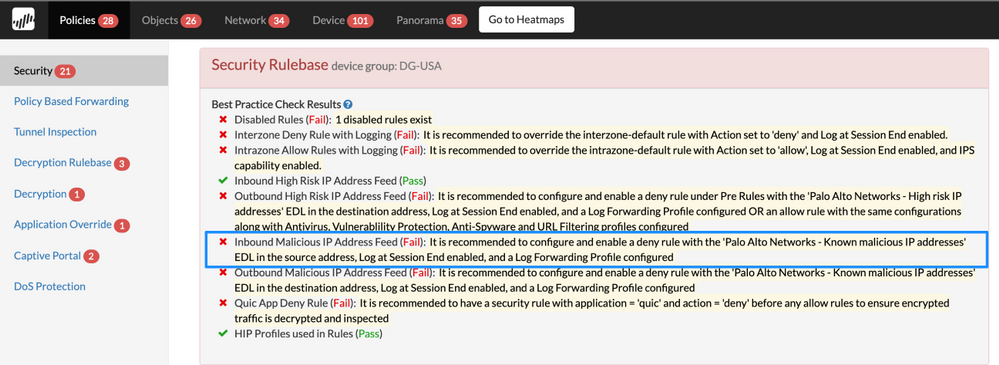
Security Policy Inbound Malicious IP Feed
Details: Before you allow and block traffic by application, it is advisable to block traffic from IP addresses that Palo Alto Networks and trusted third-party sources have proven to be malicious.
The rule will ensure that your network is always protected against the IP addresses from the Palo Alto Networks malicious IP address feeds and other feeds, which are compiled and dynamically updated based on the latest threat intelligence.
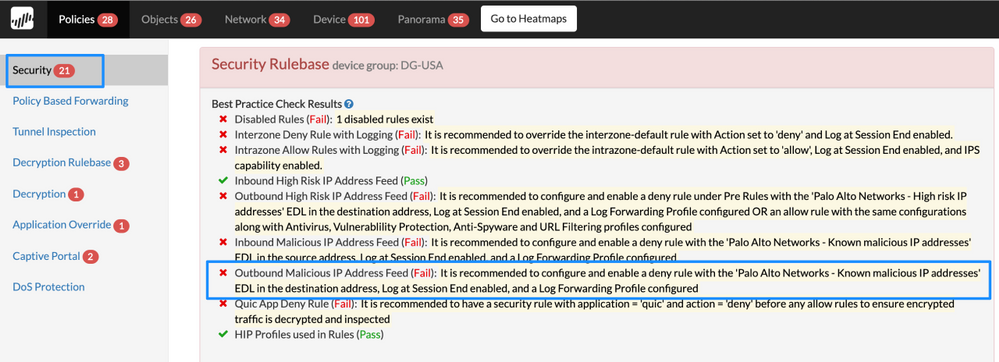
Security Policy Outbound Malicious IP Address Feed
Details: Before you allow and block traffic by application, it is advisable to block traffic from IP addresses that Palo Alto Networks and trusted third-party sources have proven to be malicious.
The security rule will ensure that your network is always protected against the IP addresses from the Palo Alto Networks malicious IP address feeds and other feeds, which are compiled and dynamically updated based on the latest threat intelligence. Ensure the security rule is logging at session end and log forwarding profile is applied to track activity.
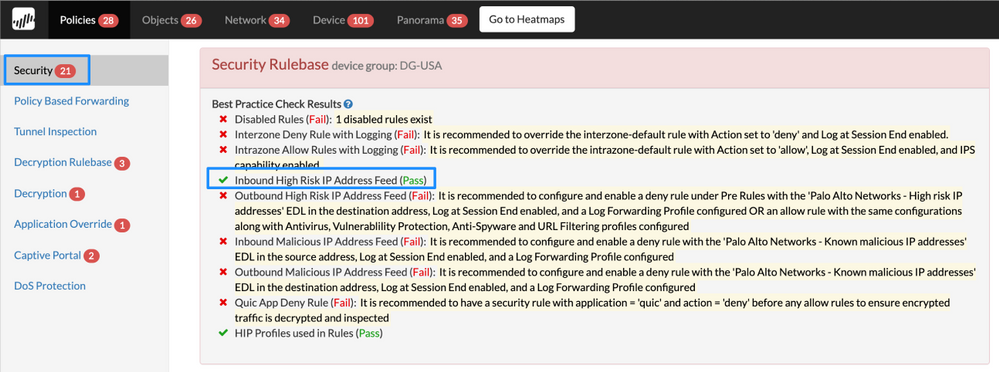
Security Policy Inbound High Risk IP Address Feed
Details: Before you allow and block traffic by application, it is advisable to block traffic from IP addresses that Palo Alto Networks and trusted third-party sources have proven to be High risk in nature.
The security rule will ensure that your network is always protected against the IP addresses from the Palo Alto Networks malicious IP address feeds and other feeds, which are compiled and dynamically updated based on the latest threat intelligence. Ensure the security rule is logging at session end and log forwarding profile is applied to track activity.
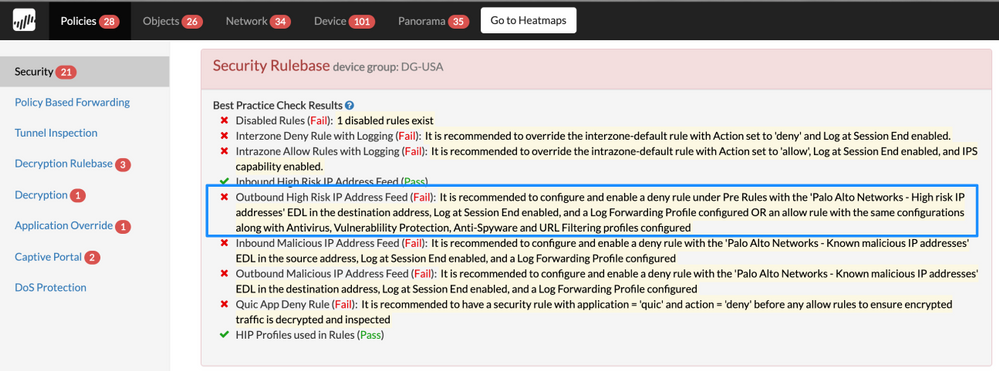
Security Policy Outbound High Risk IP Address Feed
Details: Before you allow and block traffic by application, it is advisable to block traffic from IP addresses that Palo Alto Networks and trusted third-party sources have proven to be high risk in nature.
The security rule will ensure that your network is always protected against the IP addresses from the Palo Alto Networks malicious IP address feeds and other feeds, which are compiled and dynamically updated based on the latest threat intelligence. Ensure the security rule is logging at session end and log forwarding profile is applied to track activity.
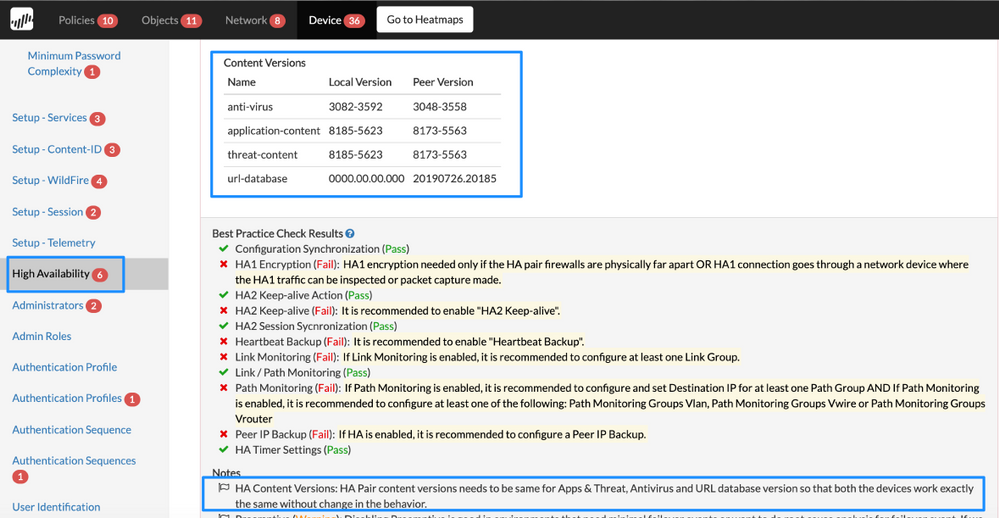
HA Content Versions
Details: This check ensures both the pairs in High Availability (HA) setup are the latest content versions. The content versions checked are Apps and Threat, Antivirus, and URL database.
Both pairs in HA will work at optimal levels if the content versions are the same between the devices. The firewall will take same action on traffic if the devices have same content version, so the expected behavior is same across.
Enhancements
- Added Industry Average trending for ZPP, Log forwarding, and Credential Phishing prevention
- Added "Rules using Profile" and "Rules using Profile Pct" for Log-forwarding profile, Decryption profile, and DoS protection profiles
- Added logic to resolve Panorama template variables
- Improved logic for check #222 – Content-Based Critical System Logs
Bug Fixes
- Fixed a display issue in the HTML report for Application Tags
- Fixed a calculation bug with the "Rules using Profile Pct" values
v3.17.1 (Hotfix) - Released on 8/16/2019
- Fixed a parsing issue with Decryption Policies and DoS Protection Policies
- best practice assessment
- BPA
- HA Content Versions
- Inbound High Risk IP Address
- Inbound Malicious IP
- Log Forwarding Authentication Settings
- Log Forwarding URL Settings
- new features
- Outbound High Risk IP Address
- Outbound Malicious IP Address
- 3262 Views
- 0 comments
- 0 Likes
- New Ransomware URL Filtering Category (BPA Version 7.3.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.4.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.3.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.2.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.1.2) in Best Practice Assessment Release Notes