
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
The content you are looking for has been archived. View related content below.
Have you ever noticed the option to disable new applications with Palo Alto Networks' scheduled content updates? Imagine enabling this feature ... why would you do this, what could possibly be a use case to use this feature?
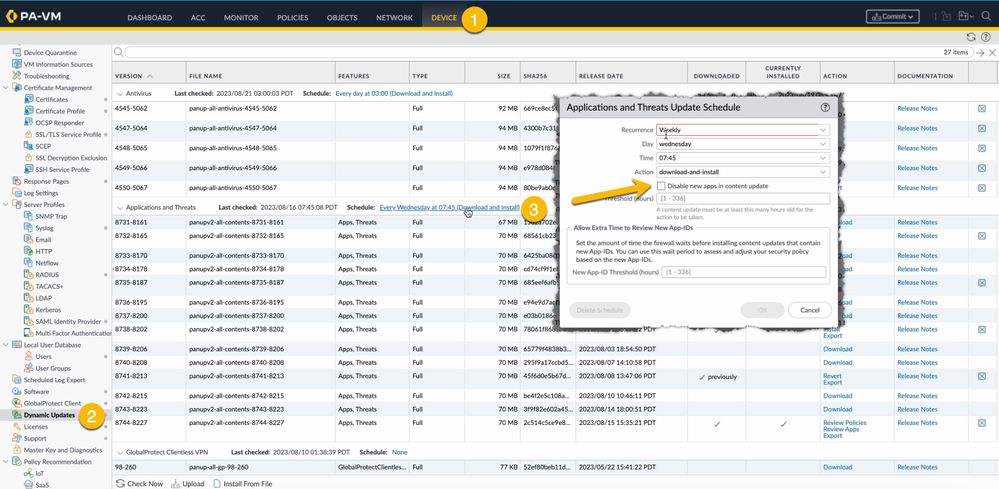
If you have never seen this option before it's likely because it's a small checkbox that can easily go unnoticed within the settings of the Applications and Threats Dynamic Updates Schedule under Device > Dynamic Updates > Applications and Threats Schedule.
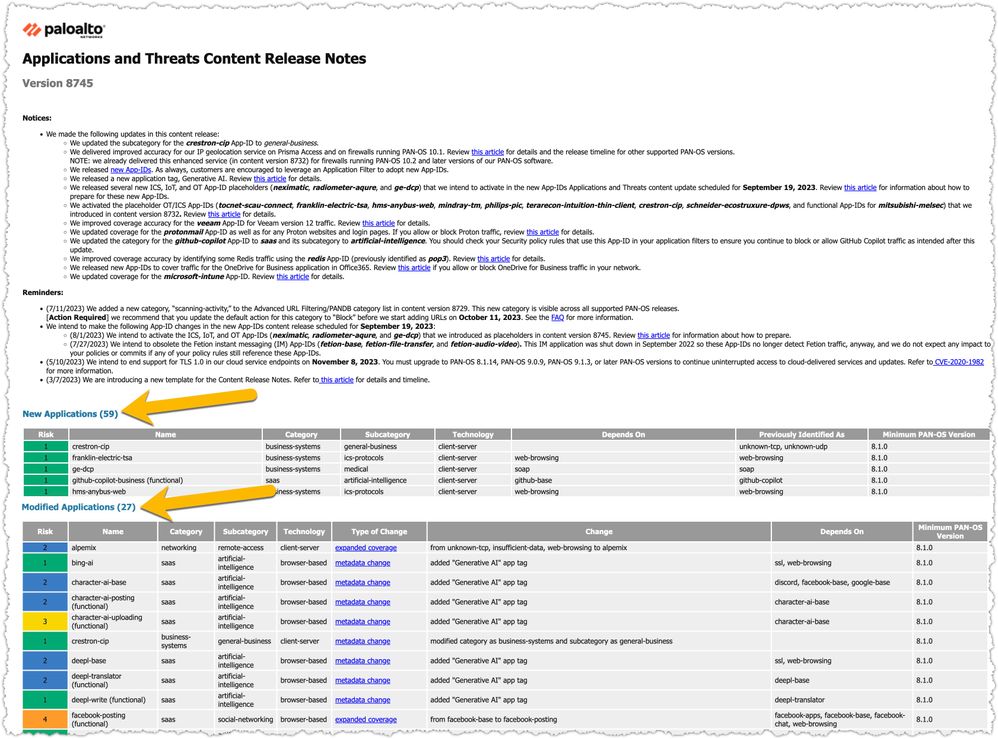
Check out these release notes – they spill the beans on a bunch of new applications making their debut in this content update in addition to having a bunch of existing applications being modified.
Check the disable option in the Dynamic Updates Schedule settings, and any new applications included in this content package will be disabled. Just a heads up, though - all the existing applications getting a makeover with this update, won't be affected by this switcheroo.
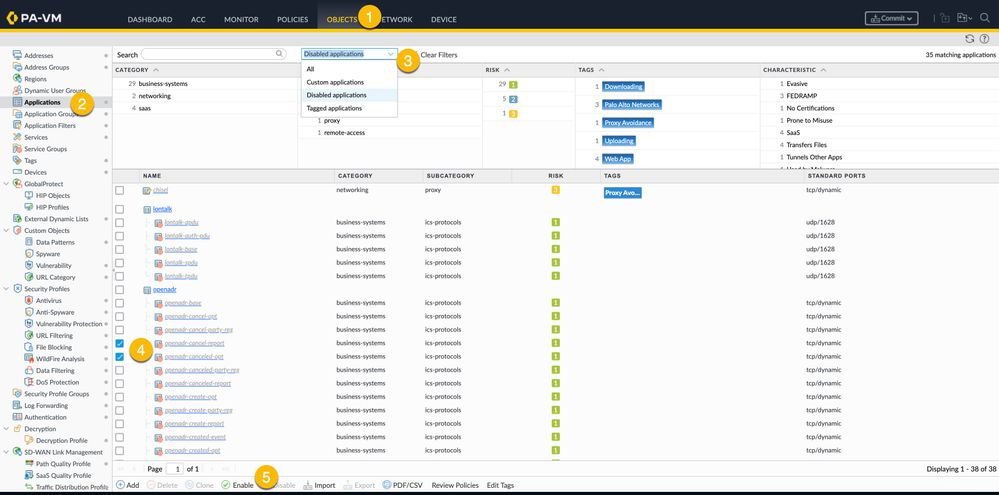
Curious about which applications are currently disabled ? Navigate to the Applications section on the Objects tab, and you can narrow down the display to show you only the applications that have been disabled. Want to get them back in action? Just check the box beside each application and hit 'Enable' at the bottom of the applications pane. Easy-peasy!
So why in the world would you want to put applications on pause? In most scenarios, it might not cross your mind, but in some cases it could be beneficial. Picture this: you get to take a closer look at the applications ready to join the application database without them jumping right into the dataplane action. You can still stick to your threats database schedule while having a say in when those applications make their grand entrance.
Imagine an new application that was previously identified as something more generic, like "web-browsing", in a very restrictive security policy that only permits known applications. Now, this new kid on the block won't have a security policy and if the admin doesn't step in, review, and set up the right security policies, this new app may get dropped by the default policy.
Imagine a security policy set up using application filters. Normally new applications get added to application filters immediately and policy applied according to the rulebase upon installation of the content package. Disabling new applications gives the admin the opportunity to review which applications will be added to the application filters and what the impact will be to the organization.
There could be regulatory requirements as well. In some environments, introducing new applications might be subject to a thorough review process to verify if an application is desirable or required to be identified (I'm looking at financial or military where strict control is of the utmost importance).
Feel free to share your questions, comments and ideas in the section below.
Thank you for taking time to read this blog.
Don't forget to hit the Like (thumbs up) button and to Subscribe to the LIVEcommunity Blog area.
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 8 Likes | |
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 16 | |
| 8 | |
| 3 | |
| 2 | |
| 2 |




