Configuring Read-only Admin Access with RADIUS Running on Win2008 and Cisco ACS 5.2
Resolution
Overview
The Palo Alto Networks device has a built-in device reader role that has only read rights to the firewall. The superreader role gives administrators read-only access to the current device. This document describe how to configure the superreader role for RADIUS servers running on Microsoft Windows 2008 and Cisco ACS 5.2. The principle is the same for any predefined or custom role on the Palo Alto Networks device.
Roles are configured on the Palo Alto Networks device using Radius Vendor Specific Attributes (VSA).
Note: The RADIUS servers need to be up and running prior to following the steps in this document.
Steps
Windows Server 2008 Radius
- On the Palo Alto Networks device, go to Device > Server Profile > RADIUS and configure the RADIUS Server Profile using the IP address, port, and the shared secret for the RADIUS server.
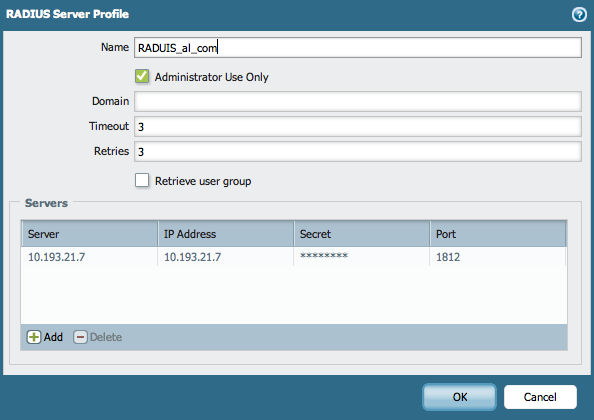
- Go to Device > Authentication Profile and create an Authentication Profile using RADIUS Server Profile.
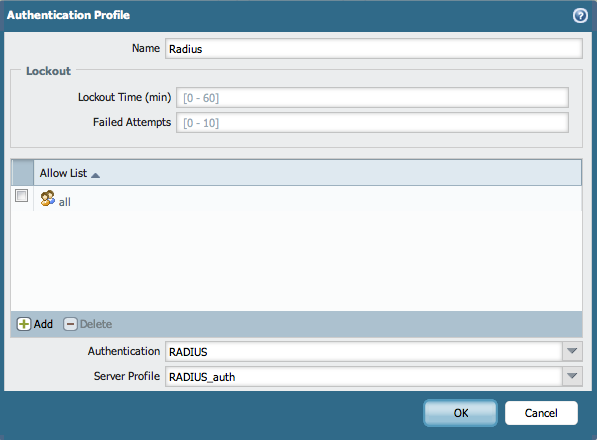
- Go to Device > Setup > Authentication Settings and choose the RADIUS Authentication Profile that was created in Step 1 (shown above):
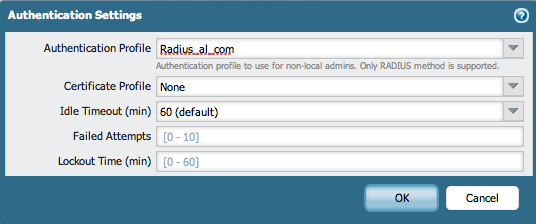
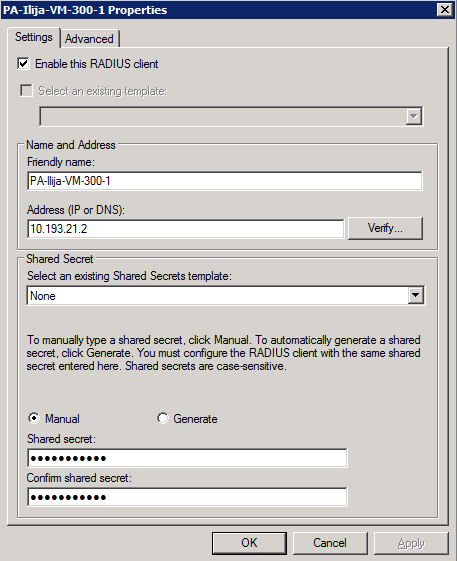
- On the Windows Server, add the firewall as a client.
Under NPS > RADIUS Clients and Servers > RADIUS Clients, create the client profile using the IP address of the firewall and a shared secret that will be used for the firewall:
- On the Windows Server, configure the Palo Alto Networks RADIUS VSA settings.
Under NPS > Polices > Network Policies, create a specific policy that will be used by the firewall:
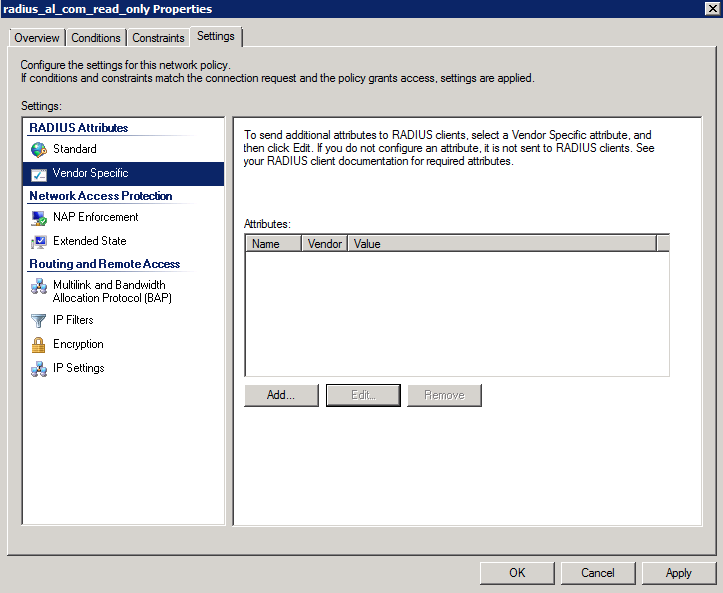
- Add the Vendor-Specific Attributes for the Palo Alto Networks firewall. Use 25461 as a Vendor code.
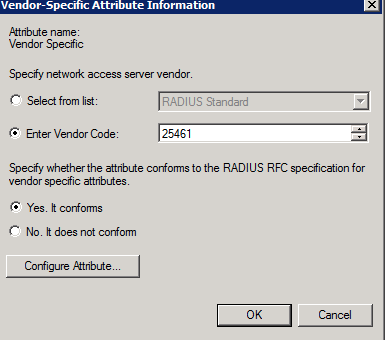
- In Configure Attribute, configure the “superreader” value that will give only read-only access to the users that are assigned to the group of users that will have that role:
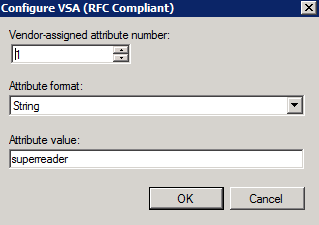
- The setup should look similar to the following:
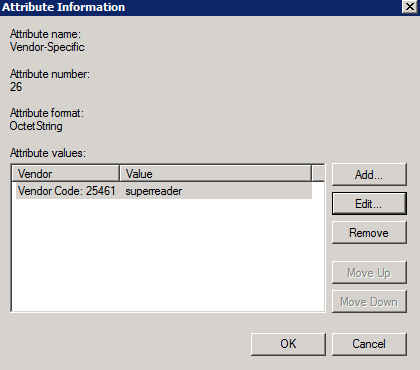
- On the Windows Server, configure the group of domain users to which will have the read-only admin role. Under NPS > Polices > Network Policies, select the appropriate group in the Conditions tab of the policy:
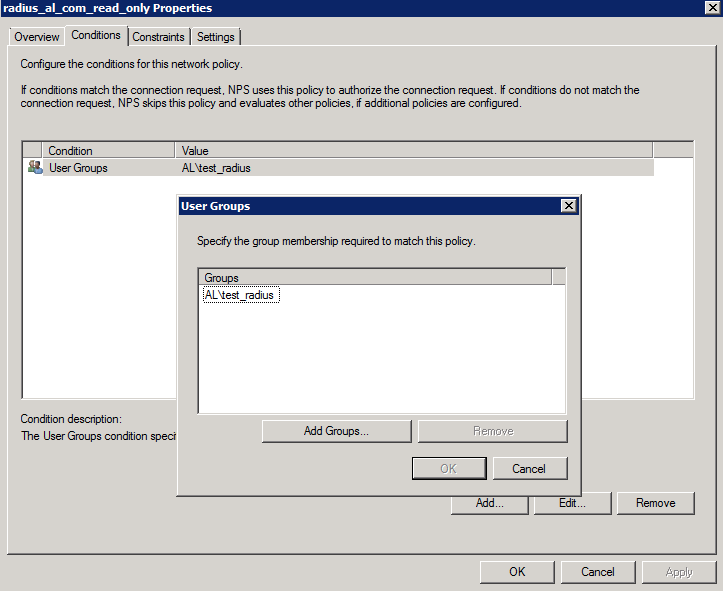
- Test the login with the user that is part of the group
- After login, the user should have the read-only access to the firewall. No changes are allowed for this user (every window should be read-only and every action should be greyed out), as shown below:
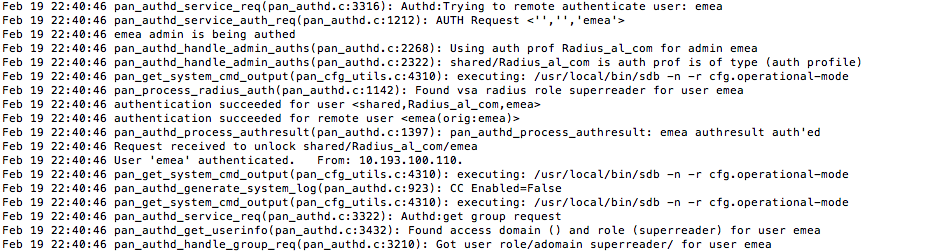
- The connection can be verified in the audit logs on the firewall. The role that is given to the logged in user should be "superreader"
- If any problems with logging are detected, search for errors in the “authd.log” on the firewall by using the following command:
> tail follow yes mp-log authd.log
Cisco ACS 5.2
- Follow Steps 1, 2 and 3 of the Windows 2008 configuration above, using the appropriate settings for the ACS server (IP address, port and shared secret).
- On the ACS, under RADIUS VSA create the PaloAlto VSA using the Vendor ID: 25461.
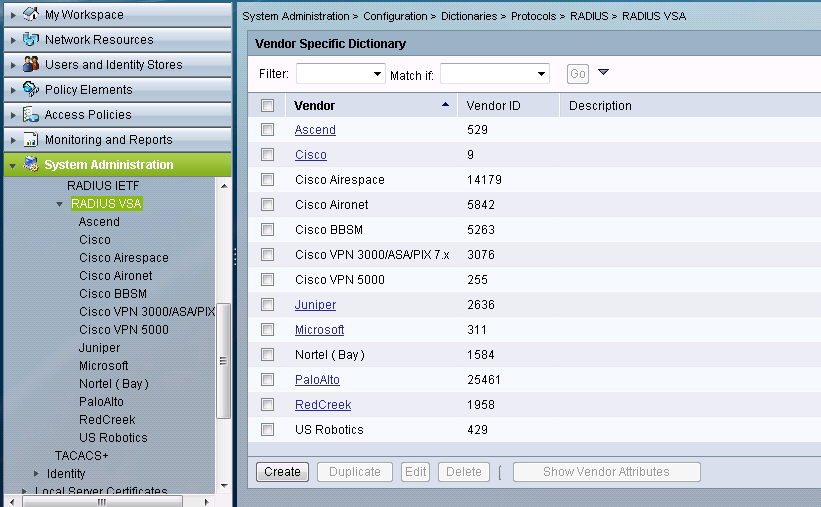
- After that, select the Palo Alto VSA and create the RADIUS Dictionaries using the Attributes and the IDs. Keep in mind that all the dictionaries have been created, but only the PaloAlto-Admin-Role (with the ID=1) is used to assign the read-only value to the admin account.
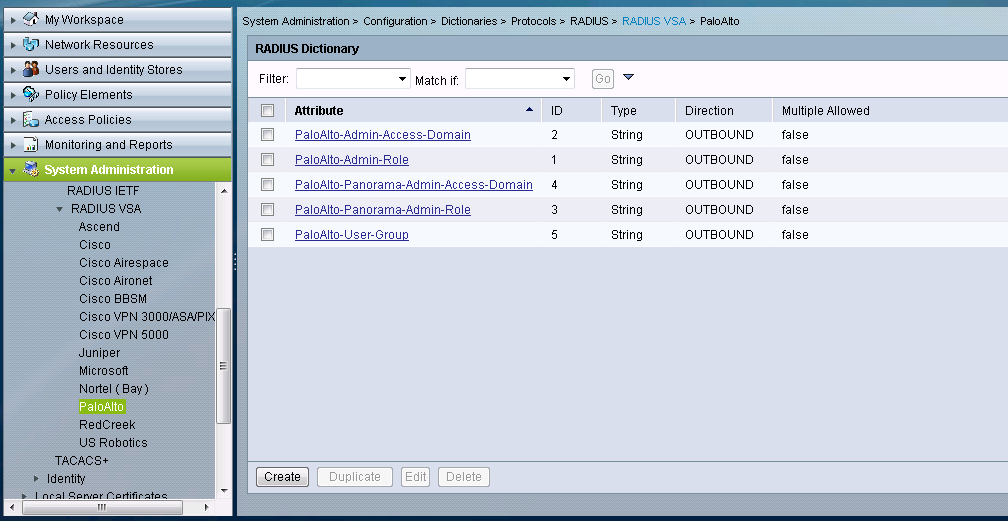
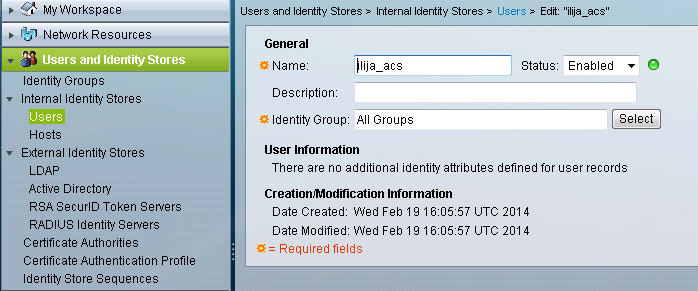
- Under Users on the Users and Identity Stores section of the GUI, create the user that will be used to login to the firewall.
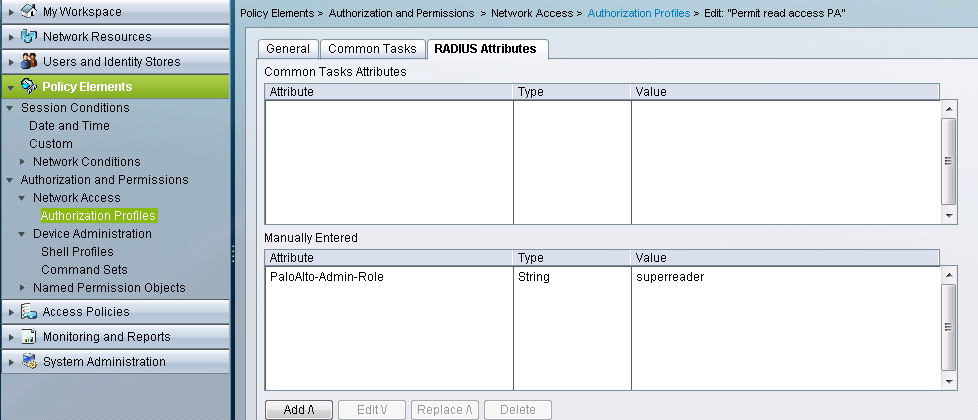
- Under Policy Elements, create an Authorization Profile for the “superreader” role which will use the PaloAlto-Admin-Role Dictionary.
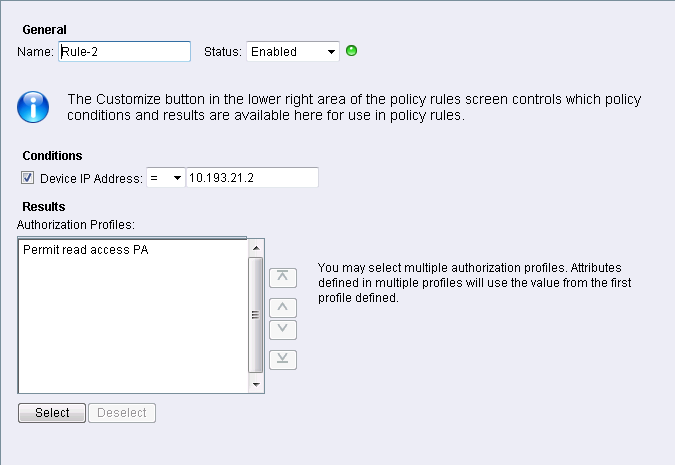
- In the Authorization part, under Access Policies, create a rule that will allow the access to the firewall’s IP address using the Permit read access PA Authorization Profile that was have created before.
- Test the login with the user that is part of the group.
- After login, the user should have the read-only access to the firewall. No changes are allowed for this user.
- The connection can be verified in the audit logs on the firewall.
- If any problems with logging are detected, search for errors in the “authd.log” on the firewall using the following command:
> tail follow yes mp-log authd.log
See Also
Radius Vendor Specific Attributes (VSA) - For configuring admin roles with RADIUS running on Win 2003 or Cisco ACS 4.0.
owner: ialeksov