How to Configure a Tunnel Where Encapsulated Traffic is Sent to Peer's External IP Address
20133
Created On 09/25/18 17:42 PM - Last Modified 06/12/23 20:26 PM
Resolution
Overview
This document briefly describes how to build a tunnel in the following network scenario:
PA-LAN <=> PAN-FW <=> Internet <=> <VPN-Peer>
[L3-trust zone] [L3-untrust zone]
The tunnel will encrypt the traffic between PA-LAN and VPN-Peer's public IP address. This scenario raises an issue as the VPN on the Palo Alto Networks firewall is route based, and the following must occur at the same time for the VPN-Peer IP address:
- The IKE and ESP needs to be forwarded to the Internet gateway
- The client's traffic (protected traffic) needs to be routed to the tunnel interface
Details
For this example, the PA-LAN is 192.168.181.0/24 and the public IP address for the VPN-Peer is 10.193.17.21. PA-LAN will access the service on 10.193.17.21.
To resolve the issue, follow the steps below:
- Create a tunnel interface
- Create a normal IKE gateway, as for a site-to-site vpn
- Create a normal IPSEC tunnel, as for a traditional site-to-site vpn
- At this step, a static route would normally be configured to push the traffic to the peer's protected IP address to tunnel interface. Instead, configure a PBF (Policy Based Forwarding) rule:
- Source Zone: l3-trust
- Source Address: PA-LAN (for example 192.168.181.0/24),
- Destination Address: Peer's public IP (for example: 10.193.17.21
- Action: forward
- Egress I/F: tunnel interface (for example tunnel.5)
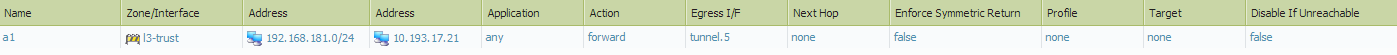
- Set an IP address on the tunnel interface. This IP address is not really used and can be set to any unused IP address in the company (for example 172.17.1.1/32). If it is not set, the following error message will appear during commit:
Error: pbf rule 'a1': No ip/ipv6 address defined on pbf interface tunnel.5. Error: Failed to parse pbf policy - Commit the changes
After the commit operation completes, test the connectivity from one of the hosts in PA-LAN.
owner: rweglarz