- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Authentication via LDAP server
- LIVEcommunity
- Tools
- Expedition
- Expedition Articles
- Authentication via LDAP server
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 06-28-2018 07:30 AM - edited on 09-27-2019 11:13 AM by Retired Member
Expedition offers local user authentication and external user authentication via LDAP and Radius servers.
In this example, we will illustrate how to configure external authentication via a Windows Active Directory server.
Settings in LDAP Server
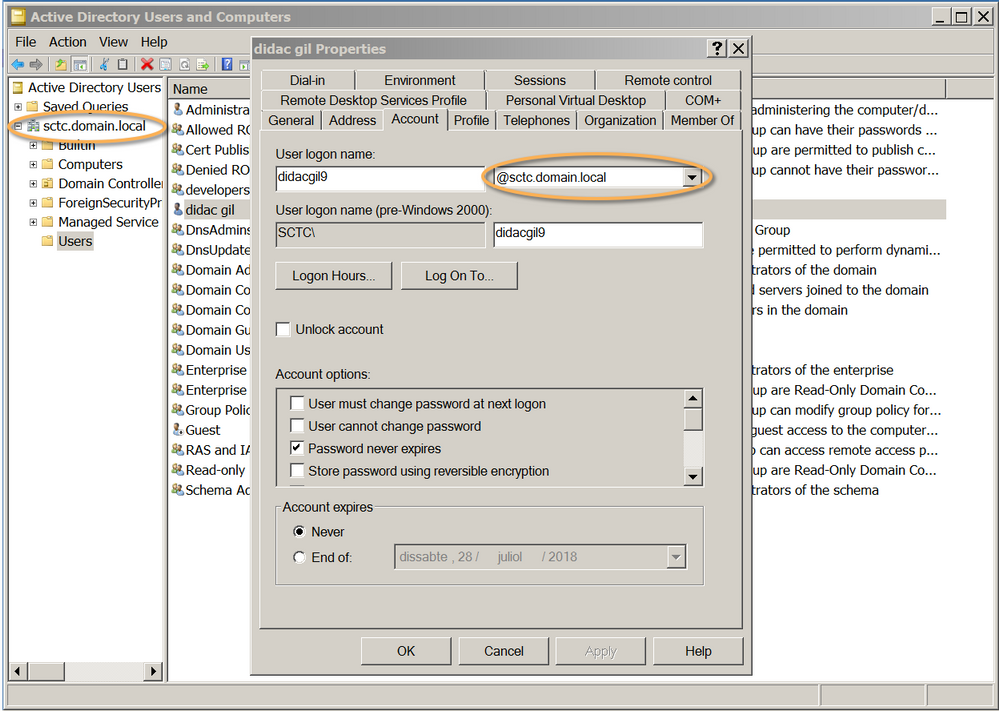
We have created a server under the domain sctc.domain.local, defined a group called "developers" and added a user "didac gil" with logon name "didacgil9".
In the figure, we can notice that users authenticate with the suffix "@sctc.domain.local". We will have to take account of this value for providing the correct settings in Expedition to complete the user authentication.
Defining LDAP Server in Expedition
In Expedition, we will first define the LDAP authentication server. Only Superusers have rights for server registration or modification.
We have two different approaches for user authentication.
Approach 1. User needs to enter full logon name
Define a server providing the desired server's name, the server's address and port, server type (Windows or Linux), Search DN parameters and SSL and/or TLS usage.
In our case, we our server responds at sctc.domain.local port:389 and we have named LDAP_approach1.
The users that will use this server for authentication belong to the developers group, therefore we have provided the following Search DN: "CN=developers,DC=sctc,DC=domain,DC=local". Contact your Active Directory administrator to verify your correct Search DN parameters.

After saving, we will test the server settings clicking on the diagnostics icon. We will be required to enter an existing user's credentials.
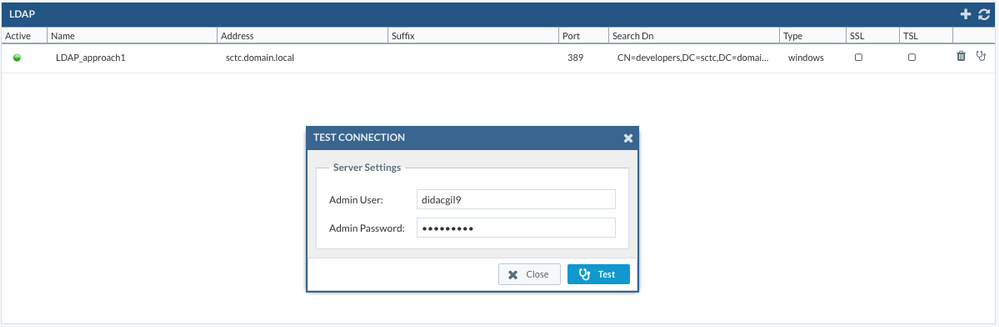
A feedback will be provided with the results of the connection.
Through this approach, users will have to provide their full account name for authentication. In our case, didacgil9@sctc.domain.local will be the user name account required to have a valid authentication.
Approach 2. Server specifies the user suffix
In this case, we will facilitate the user's logon, providing the suffix already in the server settings. This way, a user will only have to write their account name "didacgil9".

Notice that using this approach, all users must share the same suffix in order to be able to validate their credentials.
The LDAP connection is via simple bind connections. We use the user's credentials itself to verify that those credentials are valid.
The credentials are transferred via the request without ofuscation, but the connection is done via HTTPS. However, as pointed out by psuJohn, the request should be moved to a POST request so it is not even stored in the httpd logs.
We will make this change.
When testing the connection, we will provide the user's account and password, and we should be able to get the feedback on the transaction, stating that either all went fine or that there was an error such as not being able to reach the LDAP server or that the provided settings (DN or user credentials) are not valid to authenticate the user.
we have the same problem as gzygadlo
you cannot select the server type and when you try to add the server you get the message:
"The following errors have ocurred:, Enter the server type"
Anyone have success with using TLS/SSL? With Microsofts recent announcement that they will only accept encrypted connections I need to get this switched over.
I have not personally tested this for a long time, but I remember a team that got the TLS/SSL LDAP working. They tested first with a LDAP client to make sure the settings they were using were correct, as they also had issues to make sure all the settings were the correct ones.
Later, they applied the as well in Expedition and they could authenticate.
I just installed 1.1.63.1, and when I try either Radius or LDAP I get an instant error and no network traffic is generated to either server from Expedition:
My Apache2 error.log for a test request:
[Mon Mar 23 20:49:45.977222 2020] [:error] [pid 36392] [client 10.0.10.2:2282] PHP Notice: Undefined variable: app in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Mon Mar 23 20:49:45.977364 2020] [:error] [pid 36392] [client 10.0.10.2:2282] PHP Notice: Trying to get property of non-object in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Mon Mar 23 20:49:45.977416 2020] [:error] [pid 36392] [client 10.0.10.2:2282] PHP Notice: Trying to get property of non-object in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Mon Mar 23 20:49:45.977484 2020] [:error] [pid 36392] [client 10.0.10.2:2282] PHP Fatal error: Uncaught Error: Call to a member function getUser() on null in /var/www/html/bin/Authentication.php:76\nStack trace:\n#0 /var/www/html/bin/authentication/servers/testServers.php(54): require_once()\n#1 /var/www/html/bin/authentication/servers/testServers.php(35): test(Array)\n#2 {main}\n thrown in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
In order to improve the forum experience, let's try to keep the questions focused in a single topic.
Please, try to refresh your session in Expedition and let us know if that resolved the issue.
I rebooted my workstation last night for other reasons, so this was after my first connect to my Expedition server, I had a tail running on the logs: The first was a Radius test, the second an LDAP test. (I saw no traffic generated to either LDAP/RADIUS server)
I am logged in as Admin, if that matters, there are no local users yet.
[Tue Mar 24 15:08:40.241160 2020] [:error] [pid 36885] [client 10.0.10.2:1336] PHP Notice: Undefined variable: app in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:40.241301 2020] [:error] [pid 36885] [client 10.0.10.2:1336] PHP Notice: Trying to get property of non-object in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:40.241352 2020] [:error] [pid 36885] [client 10.0.10.2:1336] PHP Notice: Trying to get property of non-object in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:40.241416 2020] [:error] [pid 36885] [client 10.0.10.2:1336] PHP Fatal error: Uncaught Error: Call to a member function getUser() on null in /var/www/html/bin/Authentication.php:76\nStack trace:\n#0 /var/www/html/bin/authentication/servers/testServers.php(54): require_once()\n#1 /var/www/html/bin/authentication/servers/testServers.php(35): test(Array)\n#2 {main}\n thrown in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:58.418969 2020] [:error] [pid 36388] [client 10.0.10.2:1338] PHP Notice: Undefined variable: app in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:58.419119 2020] [:error] [pid 36388] [client 10.0.10.2:1338] PHP Notice: Trying to get property of non-object in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:58.419176 2020] [:error] [pid 36388] [client 10.0.10.2:1338] PHP Notice: Trying to get property of non-object in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
[Tue Mar 24 15:08:58.419246 2020] [:error] [pid 36388] [client 10.0.10.2:1338] PHP Fatal error: Uncaught Error: Call to a member function getUser() on null in /var/www/html/bin/Authentication.php:76\nStack trace:\n#0 /var/www/html/bin/authentication/servers/testServers.php(54): require_once()\n#1 /var/www/html/bin/authentication/servers/testServers.php(35): test(Array)\n#2 {main}\n thrown in /var/www/html/bin/Authentication.php on line 76, referer: https://expedition.columbia.csc/
Could we do a Zoom session?
Please contact me to fwmigrate@paloaltonetworks.com.
I would like to debug in your settings to find out the cause.
Hello,
Thanks for sharing your How To, but I need to secure my connection of my Expedition Tool and our LDAP servers.
The security ask to use LDAP with SSL, but I have an error.
Someone Have the same issue or just me ?
Best regards,
- 31029 Views
- 13 comments
- 2 Likes
- Expedition Tool - default user for WebGUI is incorrect in Expedition Discussions
- RADIUS not authenticating on new Expedition servers in Expedition Discussions
- Expedition - LDAP connection issue in Expedition Discussions
- How to address CVE-2022-37026 vulnerability in Expedition in Expedition Articles
- Add Device Authentication Failure in Expedition Discussions
-
address to ip address
1 -
addressgroups
1 -
Administrator's Guide
1 -
App-ID
1 -
attach device
1 -
Authentication
1 -
Best Practice Assessment
1 -
Best Practices
1 -
BPA
1 -
caveats
1 -
checkpoint R80
1 -
connection
1 -
CVE-2021-44790
1 -
Dashboard
1 -
database
1 -
devices
1 -
dns
1 -
documentation
1 -
edit
1 -
expedition
31 -
export
1 -
Filtering
1 -
filters
1 -
Gaia
1 -
Google Chrome
1 -
How to
1 -
import
3 -
installer
1 -
Iron Skillet
1 -
IronSkillet
1 -
LDAP
1 -
Logs
1 -
machine learning
2 -
migrate
1 -
Migration
2 -
Migration Tool
3 -
Objects & Security Profiles
1 -
one member
1 -
optimization
3 -
panreadorders
1 -
permissions
1 -
php
1 -
policies
1 -
policy
1 -
predefined filters
1 -
project
1 -
queue
1 -
rbac
1 -
roles
1 -
Rule
1 -
search and replace
1 -
settings
2 -
sharing
1 -
srx
1 -
task manager
2 -
Tools
1 -
Ubuntu 16.04 LTS
1 -
Ubuntu 20.04
1 -
users
1 -
Zones
1
- Previous
- Next




