- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Migrating Checkpoint R80 [UPDATED on December 2020]
- LIVEcommunity
- Tools
- Expedition
- Expedition Articles
- Migrating Checkpoint R80 [UPDATED on December 2020]
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2018 08:44 AM - edited 12-11-2020 01:39 AM
With the new version of Checkpoint Smartcenter R80, the way to obtain the rules has changed.
Exporting Configuration
To export the configuration from a Checkpoint R80 we are gonna need to download a tool from the Checkpoint's Github. We want to be sure we download latest version of the tool since the one it comes installed in your SmartCenter usually is old and may contain bugs.
So first open your preferred web browser and go to:
https://github.com/CheckPointSW/ShowPolicyPackage/releases
Check the latest, at the moment of updating this post latest version was 2.0.6, so in order to download it we have to click on the file named: web_api_show_package-jar-with-dependencies.jar
https://github.com/CheckPointSW/ShowPolicyPackage/releases/download/V2.0.6/web_api_show_package-jar-with-dependencies.jar
After download the file you have to UPLOAD it to your SmartCenter Server where Checkpoint R80 management is running.
Use your SCP preferred tool to do it.
Please read the README.md file shown in https://github.com/CheckPointSW/ShowPolicyPackage to understand how to run the downloaded file properly, pay special attention to the Examples
Before you run the command verify the Checkpoint API is running otherwise this tool will fail to execute. Please read this if you don' t know how to enable/verify if your API is UP and Running
Now you can RUN the tool from CLI as EXPERT
java -jar web_api_show_package-jar-with-dependencies.jar -v
The output from that command will let you know what Packages are available to export
Last command we have to run is the following where PACKAGE_NAME is the name you have chosen from the previous command and in case you are in a MULTI-DOMAIN environment specify the DOMAIN_NAME too (-d is OPTIONAL):
java -jar web_api_show_package-jar-with-dependencies.jar -k <PACKAGE NAME> -d <DOMAIN NAME>
This will create a new tgz file which you will use as is to import into Expedition Importation page.
Exporting Routing and interfaces
From the Firewall CLI, you can run the following:
netstat -nr > routes.txt
With all this information, we can go to Expedition, Create a new Project, enter the Project, and go to IMPORT > CHECKPOINT > VERSION R80.
- Assign a name to your configuration such as "MyInternetGW"
- Select the tgz file and attache it to the proper input
- Select the routes.txt for the routes
- Click UPLOAD
References: Checkpoint Website article about the show package tool
Hello,
I can not migrate sub policies in the security policies. Is there a fix for this?
Regards,
This isn't working, keep getting the following error:
Running:
SMS01-CKPT> mgmt_cli show access-rulebase name "Test-Policy Security" details-level "full" use-object-dictionary true --format json > Test-Policy.json
Keep getting:
MGMT9000 {
"code" : "generic_err_invalid_parameter_name",
"message" : "Unrecognized parameter [>]"
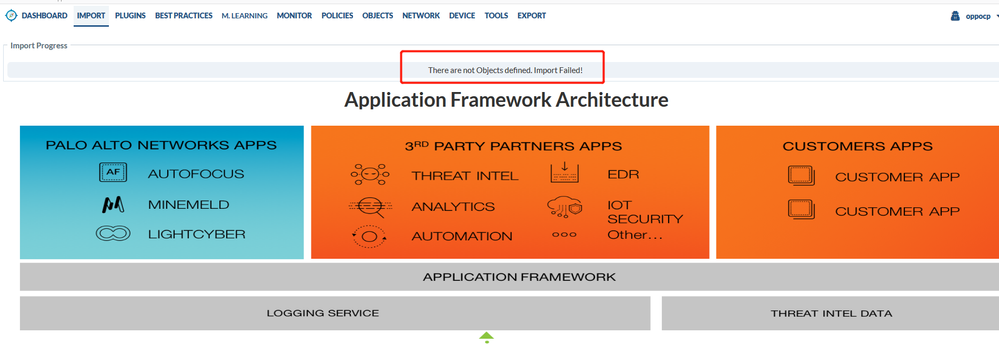
I ran the command in expert mode and the file generated correctly, however I have tried to import into the Expedition tool and each time it states There are not Objects defined. Import Failed!
THis is being completed on a SMS R80.10 VM
Completed all the config associated with that link How to Upload conf files with no luck. I have attempted to complete this instructions in this thread EXACTLY as perscribed with the most progress being the Import progress status flapping between Initializing and Reading Config.... of which it continues this back and forth for quite sometime.
Next I attempted this option outlined in this thread
Issue Getting Checkpoint R80 config to load
No luck there.
I only have 162 rules, no NAT rules, but a bunch of objects since this is an SMS with multiple policies.
Any ideas?
RESOLVED: The issue was with the .json files and piping the output to a seperate file. The commands above are correct, however the output files were adding the following "Username" at the TOP of the file:
Username:
{
"uid" : "1cxxxx6-3bff-4xxxxxx8-7xxxxxxxxx",
"name" : "blah-blah",
"rulebase" : [ ],
"total" : 111
}
This appears to be an issue/bug within the R80.10 code when doing outputs to a file as this "Username" is coming from the prompt before launching the api call.
Once this "Username:" line was removed from the json file, the import worked as expected.
I have confirmed there is a limitation on the Checkpoints of 500 rules when exporting through the API. With our environment, I had to break it up into groups of 200 due to time out and RAM issues.
I have yet to get the zip file with the orders.txt file to work as perscribed above. I am on the latest version of the expedition tool and when I upload it, it will transistion from initilizing to reading config files, but stalls from there.
Anyone else ran into issues like this or did something change with the new version?
Just want to ask you one question that suppose security and NAT policies count around 1500 rules then what is the best way to export policy in one file. Otherwise. I have to export the security policy in 400 rules count like below and zip it one folder.
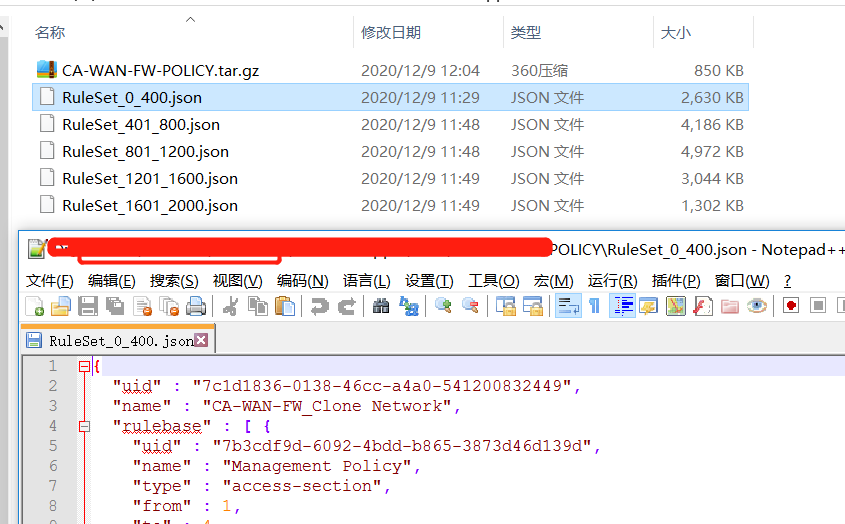
mgmt_cli show access-rulebase offset 0 limit 400 name "Internet Security" details-level "full" use-object-dictionary true --format json > RuleSet_0_400.json
mgmt_cli show access-rulebase offset 401 limit 800 name "Internet Security" details-level "full" use-object-dictionary true --format json > RuleSet_401_800.json
mgmt_cli show access-rulebase offset 801 limit 1200 name "Internet Security" details-level "full" use-object-dictionary true --format json > RuleSet_801_1200.json
mgmt_cli show access-rulebase offset 1201 limit 1500 name "Internet Security" details-level "full" use-object-dictionary true --format json > RuleSet_1201_1500.json
It is my understanding that the limitations are 500 for any of the rule sets according to Checkpoint. NAT and Security are treated as 2 SEPERATE groups. For example if you have 1000 security rules and 200 NATs; you will need 2 seperate security rules files of 500 each and 1 NAT rule file.
This being said I have yet to get the zip file proceedure to work and actually had to export out my security policies in seperate files as perscribed, but then manually merge the files into 1 .json file using notepad++.
Won't lie, it would be great if the zip proceedure worked
Hi all,
There are a few misconceptions of what each command does in your procedure, first of all "limit" is the number of results after the specified offset, for instance you set offset to 0 and limit to 400 you get rules 1 to 400.
Now the next set of rules you should consider offset 400 instead of 401, if 0=1 then 400=401 in the offset counting.
Also it's a pain to always have to request the customer for username and password and the command you wrote "hides" username request, my suggestion to update and works like a charm, do has you like:
Step1
#mgmt_cli login (when asked the customer should type his username and password here)
Step2
Copy output of the result login to a file, for the sake of my example I used id.txt
This id lets you reuse the logged in session id, with an idle timeout of 10 minutes, more then enough to run all queries, even for quite big rulebases like in my test scenario 2569 rules (don't ask...)
Step 3 run your instructions with slit differences...limit as I explained should be set to 400, you are right 400 is good number, although it allows up to 500, in rulebase it normally crashes the api or it times out, so:
Also it's good idea to set limit and the default value is 50 so you don't want to think you have it all, but the end file will tell you a tip.
Myscript:
mgmt_cli show access-rulebase offset 0 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
mgmt_cli show access-rulebase offset 400 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
mgmt_cli show access-rulebase offset 800 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
mgmt_cli show access-rulebase offset 1200 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
mgmt_cli show access-rulebase offset 1600 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
mgmt_cli show access-rulebase offset 2000 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
mgmt_cli show access-rulebase offset 2400 limit 400 name "ASecurityPolicy Security" details-level "full" use-object-dictionary true --format json -s id.txt > RuleSet_`date +%y%m%d%H%M%S`.json
tail each result:
[Expert@gw-83919d:0]# tail RuleSet_181123160805.json
"from" : 1,
"to" : 400,
"total" : 2569
}
[Expert@gw-83919d:0]# tail RuleSet_181123161507.json
"from" : 401,
"to" : 800,
"total" : 2569
}
[Expert@gw-83919d:0]# tail RuleSet_181123180927.json
"from" : 801,
"to" : 1200,
"total" : 2569
}
[Expert@gw-83919d:0]# tail RuleSet_181123181125.json
"from" : 1201,
"to" : 1600,
"total" : 2569
}
[Expert@gw-83919d:0]# tail RuleSet_181123181317.json
"from" : 1601,
"to" : 2000,
"total" : 2569
}
[Expert@gw-83919d:0]# tail RuleSet_181123181509.json
"from" : 2001,
"to" : 2400,
"total" : 2569
}
[Expert@gw-83919d:0]# tail RuleSet_181123181635.json
"from" : 2401,
"to" : 2569,
"total" : 2569
}
NOTE: See "total" in the end of file? 2569 is the total number of rules, so has a tip you will know if you have reached "to" the last rule when "total" and "to" matches.
The rest is just fine.
Hope this helps,
Regards
Hello All.
I am trying to run below command on checkpoint management center for security policy contains around 1500 security policies. So I am runing the below command to fecth the policy in 400 offset limit however i have not received output in the file and size 1KB size.
mgmt_cli show access-rulebase offset 0 limit 400 name "Internet Security" details-level "full" use-object-dictionary true -u username --format -json > RuleSet_0_400.json.
When I opend the 1 KB size file. The content shows timeout reached.
Hi AR00473455,
Check Point api can expire during your query hence the timeout, reducing the limit might help, but there are other issues to look at.
details-level "full" calls in new queries, like listing "hosts, networks, groups, services tcp/udp/other, and again service-groups, etc" unfortunately there are also limits to this new queries, and in some cases only running rule by rule will do, or even worse big rule can even crash the api, I noticed that a rule with a big list of hosts will crash the api, grouping them in a group however helps it get fixed, but other issues show up, like unexported objects within the show rulebase command, producing UID network objects with 1.1.1.1, I do have to say it's a nice trick from Albert's team at PaloAlto, but never the less this needs to get fixed by exporting smaller and smaller data through the api and compile this for Expedition.
Best regards, I hope reducing the limit like Albert says works for you, it's not working for me with some rules anyway, but I hope I'll get it fixed using the api and will share it here once I figure it out.
Regards,
Carlos Santos
Hi Albert/Carlos,
It worked,. Started to get output when I set limit to 100 so each file contains 100 rules. The same limit applied for NAT rules as well.
However I would like to know that how to combine all files into one file to process on Expedition tool . As I have done the same way what mentioned in the above article but not worked.
After we created all the json files we will need to create a new file and we will name it "order" to put inside the filenames in the order they need to be read, like in this example:
Edit "order" file
NATRuleSet_0_500.json
NATRuleSet_501_600.json
After that we have to ZIP it, to do it right all these 3 files needs to be under the same folder and from within the folder we can run the command from the CLI:
zip NatRules.zip *
Sorry for not replying, you cannot combine the files, just add them to a the zip, along with "order" file, the content of the order file should be the list of the rules by order top down, that's it.
I wrote a script for exporting policies on our Provider-1 system. It takes 2 variables, one is the CMA IP and the other is the Policy name. It will export the files in chunks of 50 rules and create a zip file containing them all with the order file as well. It will do this for both the access policy and the nat policy. We had performance issues on our MDS for exports so we have it set to 50. The big issue we still run into due to performance is if it fails to properly get the data back. You never get a warning, you just end up with a mostly empty file. So look for any files in your zips that are oddly small.
#!/bin/bash
#
# This script exports the given access and nat policy for the CMA given and
# puts it into the proper format for importing into Expedition
#
#
VERSION=1.0.21
. /etc/profile.d/CP.sh
cd /var/log/tmp
ID="id-$$.txt"
USAGE='Usage: export-policy.sh (CMA IP) (Policy)\t\n '
if [ $# == 0 ] ; then
echo -e $USAGE
exit 1;
fi
CMAIP="$1"
if [ $2 ] ; then
POLICY="$2"
else
echo -e $USAGE
exit 1;
fi
if ! mdsenv $CMAIP >& /dev/null ;
then
if [ ! $CMAIP = "Global" ] ; then
echo "That is not a proper CMA IP"
exit 1
fi
fi
mgmt_cli login -r true -d $CMAIP > $ID
TOP_LIMIT=`mgmt_cli show access-rulebase -d $CMAIP offset 50000 limit 50 name "$POLICY Security" details-level "standard" use-object-dictionary true --format json -s $ID | grep total | awk -F " " '{print $3}'`
OFFSET="0"
FILENAME="0_50"
echo "Total Number of Rules: $TOP_LIMIT"
echo -n "Exporting Rules."
while [ "$OFFSET" -lt "$TOP_LIMIT" ] ;
do
mgmt_cli show access-rulebase -d $CMAIP offset $OFFSET limit 50 name "$POLICY Security" details-level "full" use-object-dictionary true --format json --conn-timeout 3600 -s $ID >> RuleSet_$FILENAME.json
OFFSET=$((OFFSET+50));
FILENAME="$((OFFSET+1))_$((OFFSET+50))"
echo -n ".$OFFSET"
done
echo " "
echo "Packing up files"
ls -rt RuleSet*.json >order
/opt/CPsuite-R80/fw1/Python/bin/python -m zipfile -c $POLICY-Rules.zip order RuleSet*.json >/dev/null 2>&1
rm RuleSet*.json
echo " "
if [ ! $CMAIP = "Global" ] ; then
TOP_LIMIT=`mgmt_cli show nat-rulebase -d $CMAIP offset 50000 limit 50 package $POLICY details-level "standard" use-object-dictionary true --format json -s $ID | grep total | awk -F " " '{print $3}'`
OFFSET="0"
FILENAME="0_500"
echo "Total Number of NAT Rules: $TOP_LIMIT"
echo -n "Exporting NAT Rules."
while [ "$OFFSET" -lt "$TOP_LIMIT" ] ;
do
mgmt_cli show nat-rulebase -d $CMAIP offset $OFFSET limit 500 package "$POLICY" details-level "full" use-object-dictionary true --format json --conn-timeout 3600 -s $ID >> NATRuleSet_$FILENAME.json
OFFSET=$((OFFSET+500));
FILENAME="$((OFFSET+1))_$((OFFSET+500))"
echo -n ".$OFFSET"
done
echo " "
echo "Packing up files"
ls -rt NATRuleSet*.json >order
/opt/CPsuite-R80/fw1/Python/bin/python -m zipfile -c $POLICY-NatRules.zip order NATRuleSet*.json >/dev/null 2>&1
rm NATRuleSet*.json
echo " "
echo "Output found in $POLICY-Rules.zip and $POLICY-NatRules.zip."
else
echo "Output found in $POLICY-Rules.zip"
fi
echo " "
mgmt_cli logout -s $ID
rm $ID >/dev/null 2>&1
echo "All Done. Don't forget to grab a copy of the routing table from the gateway"
(Updated to fix NAT export/import)
This thread has been helpful, however when I go to import the created zip files into expedition it hangs on "Reading config files" with no error or indication as to what's happening. Any insight into system generated logs or ways to determine what's causing this problem?
Hi ..trying to migrate from R80.10 using Expedition tool version 1.1.35. When I use the 80.10 Beta it says "No Index File Found", if I try the R80 command it stays on Reading config file and does not seem to progress. Any help would be appreciated.Thanks.
Use this link to update the file size limit. I was able to upload Checkpoint 80.10 config both ways using json and R80.10 Beta zip file
Hi All,
I have 1161 security policy on checkpoint
I've exported security policed used following commands, after that I created one archive zip file, I did not exported NAT and interfaces
mgmt_cli show access-rulebase offset 0 limit 400 name "XXX" details-level "full" use-object-dictionary true --format json > RuleSet_0_400.json
mgmt_cli show access-rulebase offset 401 limit 800 name "XXX" details-level "full" use-object-dictionary true --format json > RuleSet_401_800.json
mgmt_cli show access-rulebase offset 801 limit 1161 name "XXX" details-level "full" use-object-dictionary true --format json > RuleSet_801_1161.json
I created new project on the Expedition Tool and upload created file, after that I see below, there is a information "reading config file"
and nothing else has been going on for 2 hours. Can you assist me ?
Thanks
Pawel
Hi Pawel,
The expedition tool has a 2 MB file size limit, you will have to increase that limit by following the procedure mentioned in the link below to upload bigger files.
Hi All,
One important thing, I've changed root password due I don't have DHCP server and I had to set static IP address and in logs /var/log/syslog I see that root account can't connect to database.
Somebody know where Expedition tool store more details logs?
Hi,
Could you contact us to fwmigrate to arrange a session to help you get the connection back?
I am trying to run the java -jar web_api_show_package-jar-with-dependencies.jar -k <PACKAGE NAME> -d <DOMAIN NAME> command, replacing the packagename and domain name but I got the following error:
Script stopped running due to severe error!
Result file location: show_package-2020-07-28_09-58-28.tar.gz
Hello @anh2lua
I believe we have an email thread going on where we asked you to perform some tasks to continue trouble-shooting. Please follow up on that email sent you. The support will be much better if you can continue to reply to our emails.
Thank you.
Hello all
I just discovered expedition, what a great tool !
Just got a problem using it with Checkpoint R80 and trying to retrieve a whole configuration.
It seems like I get policies and nat rules as expected, but not all the objects.
How did you do the job on your side ?
Details on my experience below :
As an example, I imported a rule containing an object group named MY_GROUP, containing MEMBER1 to MEMBER8.
All objects are present in the export as uid.
I can see that in Expedition, I only got one member.
Digging in the json file, I can see that the member I got is the one provided in the object dictionnary.
I tested for this group to get the whole group config using "mgmt_cli show group name MY_GROUP details-level full --format json" and to import it in the initial file. It worked.
So Checkpoint did not provide the whole dictionnary using my commands.
mgmt_cli show access-rulebase offset 0 limit 800 name "CheckPoint_GS Security" details-level "full" use-object-dictionary true --format json
mgmt_cli show nat-rulebase offset 0 limit 800 package "CheckPoint_GS" details-level "full" use-object-dictionary true --format json
Any idea could help, thanks in advance 🙂
With all this information, we can go to Expedition, Create a new Project, enter the Project, and go to IMPORT > CHECKPOINT > VERSION R80.
- Assign a name to your configuration such as "MyInternetGW"
- Select the Rules.zip for Security Rules
- Click UPLOAD
but the expedition display there are not objects defind, How to solve the problem ? any body have some suggerst ?
expedition(version 1.0.105)
参考 Gun-Slinger replay
RESOLVED: The issue was with the .json files and piping the output to a seperate file. The commands above are correct, however the output files were adding the following "Username" at the TOP of the file:
but have new question,i have 2000 rules,export have four jasion file,
i remove username field on each file, then i direct compress this four files again,
but when i import the compress file ,the expedit dispaly no object define again?
if i import the RuleSet_0_400.jason file,that is ok.
I have no experience working with Checkpoint firewalls. I am working on migrating Checkpoint to Palo and, got the tgz and routes.txt with the help of current admin. When I try to import the config, the import progress shows the error "NO INDEX FILE FOUND". How can I fix this? Thanks in advance.
HI @Sly_Cooper , could you please try unzip the checkpoint tgz file and see if there are index.html and index.json inside ? That's what the Expedition is looking for. Also , please make sure you are running the latest version v1.1.90. If you still encounter an issue, feel free to open a TAC case and attach the checkpoint config in it, if you do have case open , pelase send email to fwmigrate@paloaltonetworks.com to inform us about the case# . Thank you!
@lychiang - Somehow the last export from Checkpoint worked and the tgz had all required files. I was able to import the config in the Expedition tool. Thank you!
Hi everyone.
I'm getting the same message "No Index File Found" once I import the tzg file. I did the php.ini file size mod.
@VijiSridhar were you able to solve it uploading json files?
Kindly let me know.
@AdrianPerez Please follow the instructions below for exporting checkpoint config:
Hello @lychiang,
I tried to run that command java -jar web_api_show_package-jar-with-dependencies.jar -v but I've got command not found.
I ran it in Expert mode on the checkpoint device.
Regards,
Adrian
Hi @AdrianPerez , the tool is supported by Checkpoint , please refer to the checkpoint site https://github.com/CheckPointSW/ShowPolicyPackage/. the main page listed the instructions, below are the examples:
Running the tool on a Security Management server:java -jar web_api_show_package-jar-with-dependencies.jar
• Running the tool on a Security Management server for a specific policy package:java -jar web_api_show_package-jar-with-dependencies.jar -k <PACKAGE NAME>
• Running the tool on a Multi-Domain Server for a specific domain and a specific policy package:java -jar web_api_show_package-jar-with-dependencies.jar -k <PACKAGE NAME> -d <DOMAIN NAME>
• Running the tool on a side server to list the policy packages from the Security Management server running on 198.51.100.5:java -jar web_api_show_package-jar-with-dependencies.jar -m 198.51.100.5 -v
Hello guys,
First, thanks for your support.
I used this way to export CheckPoint configuration and everything working in Expedition except one thing. I cannot see Hit Counts in Expedition, even though I used -c parameter during the configuration export from CheckPoint. When I extract tgz configuration archive I can found hits in json or html files. So hits are exported from CheckPoint but they are not imported in Expedition.
CheckPoint version is R80.40
Expedition is 1.1.95
Anyone have the same issue?
Thanks in advance.
- 104852 Views
- 62 comments
- 3 Likes
- Expedition 1.2.84 Hotfix Information in Expedition Release Notes
- Expedition 1.2.80 Hotfix Information in Expedition Release Notes
- From Checkpoint to Palo Alto - FW Migration in Expedition Discussions
- Migrate User-ID based rules from CheckPoint in Expedition Discussions
- Checkpoint to Palo - Expedition Migration in Expedition Discussions
-
address to ip address
1 -
addressgroups
1 -
Administrator's Guide
1 -
App-ID
1 -
attach device
1 -
Authentication
1 -
Best Practice Assessment
1 -
Best Practices
1 -
BPA
1 -
caveats
1 -
checkpoint R80
1 -
connection
1 -
CVE-2021-44790
1 -
Dashboard
1 -
database
1 -
devices
1 -
dns
1 -
documentation
1 -
edit
1 -
expedition
31 -
export
1 -
Filtering
1 -
filters
1 -
Gaia
1 -
Google Chrome
1 -
How to
1 -
import
3 -
installer
1 -
Iron Skillet
1 -
IronSkillet
1 -
LDAP
1 -
Logs
1 -
machine learning
2 -
migrate
1 -
Migration
2 -
Migration Tool
3 -
Objects & Security Profiles
1 -
one member
1 -
optimization
3 -
panreadorders
1 -
permissions
1 -
php
1 -
policies
1 -
policy
1 -
predefined filters
1 -
project
1 -
queue
1 -
rbac
1 -
roles
1 -
Rule
1 -
search and replace
1 -
settings
2 -
sharing
1 -
srx
1 -
task manager
2 -
Tools
1 -
Ubuntu 16.04 LTS
1 -
Ubuntu 20.04
1 -
users
1 -
Zones
1
- Previous
- Next