
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
The content you are looking for has been archived. View related content below.
Application Override is where the Palo Alto Networks firewall is configured to override the normal Application Identification (App-ID) of specific traffic passing through the firewall. As soon as the Application Override policy takes effect, all further App-ID inspection of the traffic is stopped and the session is identified with the custom application.
Please note that this is different from a traditional "Custom Application" as a Custom Application normally uses a signature and any traffic passing through the firewall would be identified as such, and not need an Application Override.
You might ask why we'd ever need to override the normal application identification process. In some cases, customers build their own custom applications to address specific needs unique to the company. For these applications, we may not have signatures to properly identify the expected behavior and identify the traffic with a known application. In such cases, we recommended creating an application override to allow easier identification and reporting, and to prevent confusion.
Let's look at a typical scenario where you might use an Application Override policy. If you, for example, have a custom application that uses TCP Port 23, but traffic passing through the firewall is identified as temenos-T24, and the misidentification causes confusion about the traffic, then an Application Override can be implemented to correctly identify the traffic.
What You'll Need for Setup:
To configure an Application Override, go to Policies > Application Override in the WebGUI. For setup, you'll need the following:
Special Note about Content and Threat inspection
Application Override to a custom application will force the firewall to bypass Content and Threat inspection for the traffic that is matching the override rule. The exception to this is when you override to a pre-defined application that supports threat inspection.
When you setup a rule in Application Override for a pre-defined application, the firewall has been configured to not do any application identification, but it will continue to do content threat inspection. Since the firewall is forced to apply the application to any session that matches the default ports for the pre-defined application, any application handled by the rules will be assumed to be this pre-defined application. You may not get the results you expect. Palo Alto Networks does not recommend setting up an app-override rule for a pre-defined application
To configure a new Custom Application for Telnet, which uses TCP Port 23:
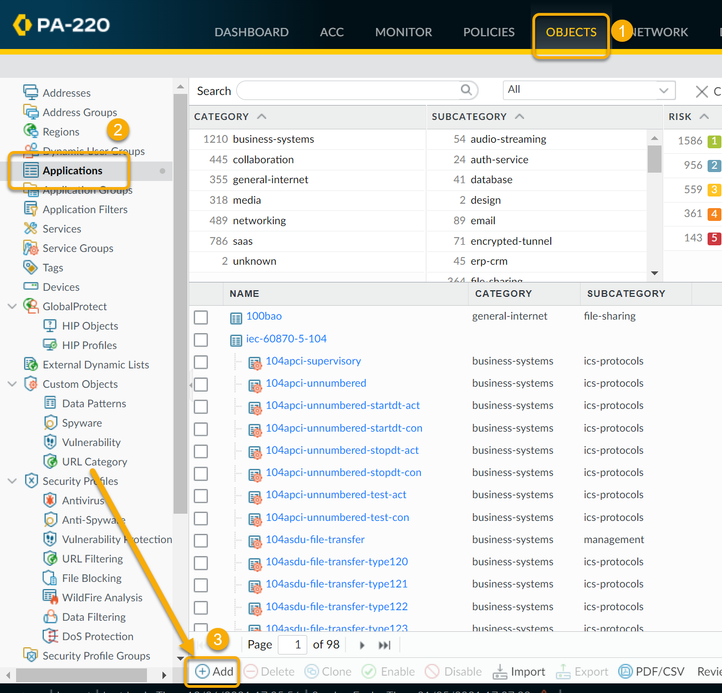
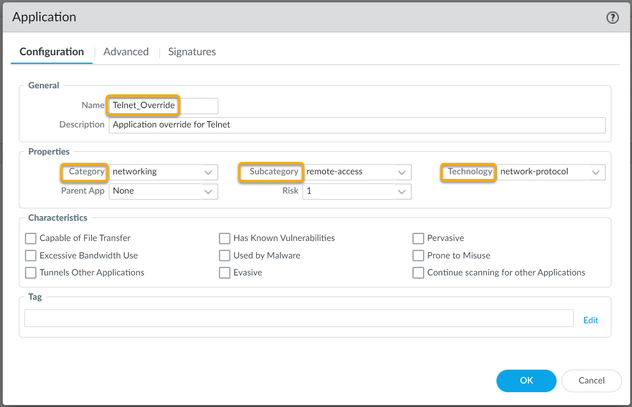
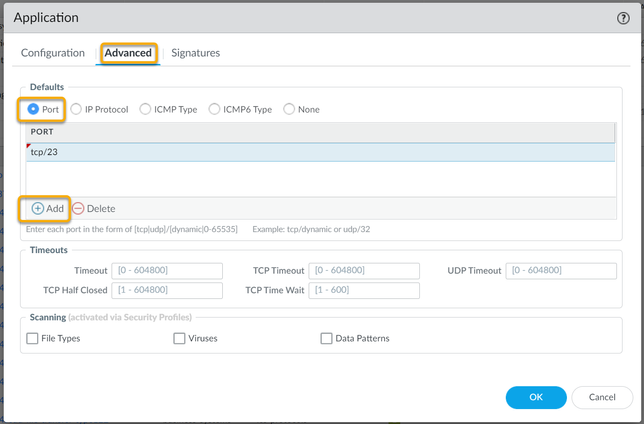
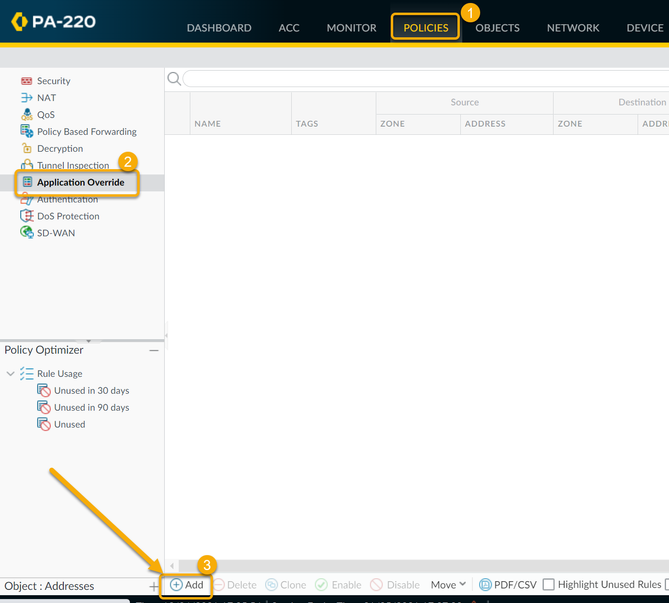
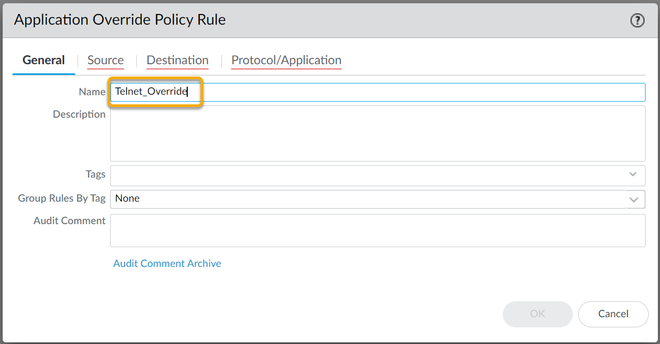
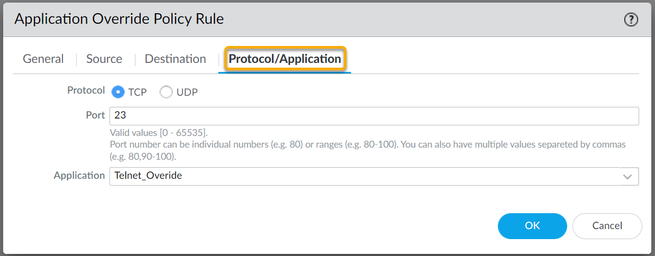

Now in order to use this new Application override, you need to create a new Security Policy to allow this new application through the firewall, or modify an existing rule.
Additional Information
Note: Once an override is configured for an application, it must be assigned to any and all pre-existing rules that leverage the application. If not, once the override is in place the policies with old Application will break.
Some questions:
Q: About the timeouts associated with the custom app.
A: If they are left blank, the system global setting (show session info) will be used.
Q: In this example, if you were to also have to allow the same behavior from the untrust server to the trust server, would it require a second custom App? (Since you apply the to/from in the app override, but in the security policy you are select the custom app not the app override?)
A: You'll need to create a second app override policy to match the direction of the session if it is initiated in the opposite direction (no need to create an app override policy for returning packets)
Q: I still cant understand why not just use a port number? What's the benefit to creating the custom app?
A: If you have created your own internal application that behaves like an application AppID can identify, you will be fine and the connections will be fine. Only the logs will reflect some standard application (eg http, telnet, ....)
There's two additional steps:
1. A custom app can help you fine-tune your logging and reporting as they will reflect your homebrew application instead of it's parent application. As long as there's no problems with the connections themselves, the custom app will simply help identify your custom app in logs and reports.
2. Application override will ensure AppID does not break your application in case it does not behave like anything it can identify: AppID will try to protect you from misbehaving applications by interrupting sessions that have been identified as applicationX, but do not behave like applicationX, e.g. you built something that sends out some http syntax and then switches to SQL queries and also chucks in some DNS queries, maybe even some GRE over TCP. AppID might not be happy with that and drop packets because the behavior is not normal. If you create a custom app and set your sessions to override to this custom app, we'll stop inspecting the sessions for 'normal' behavior.
My thanks to @reaper for his Q&A help with this one.
Thanks for taking time to read my blog.
If you enjoyed this, please hit the Like (thumb up) button, don't forget to subscribe to the LIVEcommunity Blog area.
As always, we welcome all comments and feedback in the comments section below.
Stay Secure,
Joe Delio
End of line
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |




