- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Allowing Lync: enabling SSL decryption blocks it
- LIVEcommunity
- Discussions
- General Topics
- Allowing Lync: enabling SSL decryption blocks it
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Allowing Lync: enabling SSL decryption blocks it
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2016 08:40 AM - edited 01-09-2016 08:41 AM
Hi,
In a test setup I'm trying to allow MS-Lync while SSL decryption is enabled.
I've got a general rule to enable SSL Decryption with the proper certificate installed on the clients end.
In my security policies I've got a rule to allow Lync based on App-ID.
Lync however refuses to even sign in.
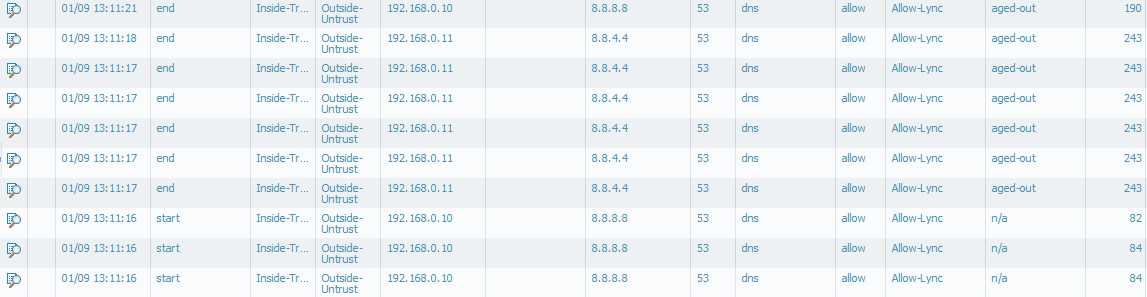
The only thing I have noticed that DNS requests seeem to age out for a to me unknown reason:
As a test, I added a no-decrypt rule for MS/Lync URL's, but that doesn't really make a difference.
As soon as I disable the decryption rule, all works fine (but of course allows more than I would want). How can I exclude lync from being decrypted, or even better, how do I get Lync to get through with decryption enabled?
there is a comment at the bottom from someone stating the issue that Lync is failing when SSL decryption is enabled, but he refers to a broken link. Any suggestions?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2016 08:29 PM
You have to stop decryption for lync otherwise it will fail. To stop decrypting you can create a customer URL category and inside that you have specify the URL used by your lync.
To find out the URL used by lync:
1> Create a URL filtering profile which have action for all category as alert.
2> Create a security policy to allow only lync traffic for one specific host and apply the URL filtering profile in this security policy.
3>Create another security policy to deny everything for that sepecific host.
4> Do a commit and check if the lync is working or not if it is not working allow more applicaitons.
5> Now if the lycn is working you will get the URL allowed by the security policy from URL logs.
Take these URLs and apply them into customer url Category. Call the custom URL cateogry into the no decrypt rule.
Hope this helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2016 07:31 AM
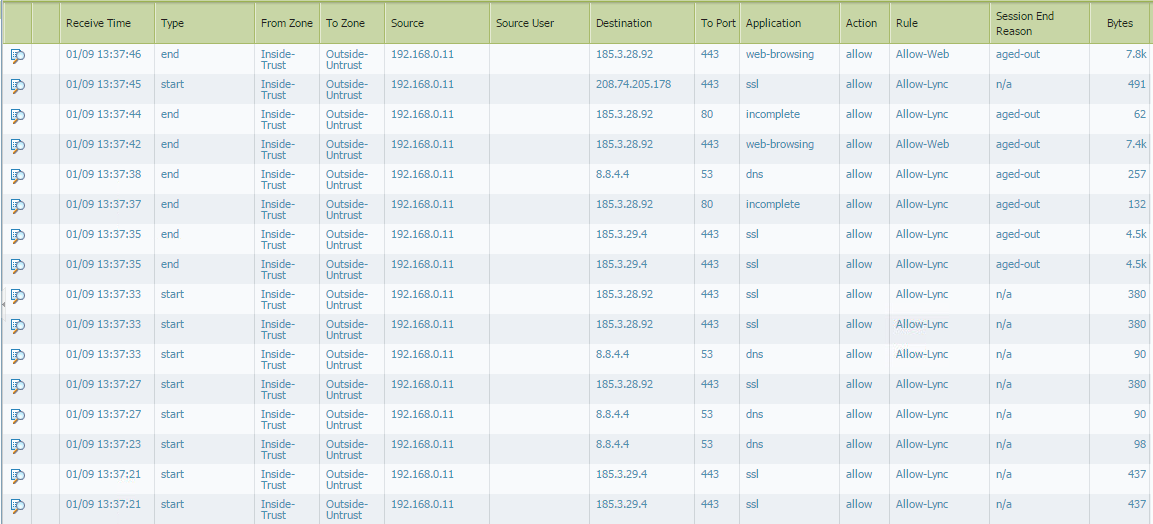
Actually, I tried that ("As a test, I added a no-decrypt rule for MS/Lync URL's, but that doesn't really make a difference.") using the list of URL's & IP addresses at:
But it still seems to fail on session age-outs..
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2016 09:30 AM
Could you attach the custom url category that you have created for not decrypt. Also the screenshot for the URL filtering logs.
- 2904 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- error: azure marketplace vm-series do not bootstrap in VM-Series in the Public Cloud
- Custom URL category matching in Next-Generation Firewall Discussions
- block yahoo mail in Next-Generation Firewall Discussions
- SSL Decryption Exclusion - What does "Obsolete (Enable me to clean)" mean? in Next-Generation Firewall Discussions
- GotoWebinar WebCam Issue in Next-Generation Firewall Discussions