- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Application Filtering and Basic Setup
- LIVEcommunity
- Discussions
- General Topics
- Re: Application Filtering and Basic Setup
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Application Filtering and Basic Setup
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2017 06:13 AM
Hi All,
I would like to ask the FF.
1. I want to use Application filtering but permits web browsing.
- Enabled App filtering, Permit Web-browsing, SSL and DNS but I can't browse and launch any website. Any idea how to permit only browsing on app level? What should i allow?
2. In future is it hard or does it affect you in production when using application on palo alto?
3. Can we combine URL and APP filtering? Can you share some best practice?
4. What palo alto feature enabled is a MUST on your production to help, improve and provide more security and fully use palo alto features? Give example? (ex. Wildfire, Dos, File Blocking Profile, Zone Protection).
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-02-2017 08:56 AM
First of all: keep in mind that PaloAlto’s definition of web-browsing, could be a different definition than yours. For example: you might see facebook as web-browsing, where PaloAlto sees this as a different application.
So, if you would “only” allow web-browsing, a lot of “applications” gets broken.
I suppose you are on a working environment where you want to transfer from allowing specific ports to allowing specific applications? I personally prefer this approach:
- Create a new Application Group and add all applications that you would like to allow.
- Add a new rule above the allow port rule, where you allow the new application group.
- Start monitoring the traffic that is still passing the firewall by the old (port) rule.
- Extend you’re new application group with applications that you want to allow and are still passing the port based rule.
- After a while, when you don’t see any applications passing the port rule that you want to allow you can disable this port rule.
Another approach is to use application filters. For example: create an Application Filter with Technology "browser-based" and Risk 1,2,3 and 4 and allow this in your newly created rule.
You can also use application filters to explicitly block certain traffic. For example: You can create an application filter where you select subcategory “encrypted-tunnel” and “proxy”, characteristics “Evasive”, and create a rule (above your allow rule) to block these kind of traffic.
As a global rule: for the allow rules you should choose “application-default” under the Serive/URL Category, and for the deny rule’s you should use “any”. If you’re using SSL decryption you should create some workarounds for the allow application-default part.
The Application and Threats update can ruin the firewall’s behavior. When a user was able to use a certain application, and after a while the update desides that this isn’t just web-browsing, but a specific application, it can gets blocked. I think you can disable this at Device -> Dynamic Updates -> Application and Threats -> Schedule -> Enable the checkbox “Disable new apps in content update”.
However, I should prefer letting the user request a firewall change after this update.
I think this also answers your 2nd question: Yes, there will be some work in the future updating you’re application rules. (as new applications comes out or you're users are finding new applications to use, which you should allow)
And for the 3rd question: sure you can use URL filtering. Since we tried to block evasive proxy / tunnel applications you should also block URLs of the category “proxy-avoidance-and-anonymizers” (and all other categories you would like to block).
Good luck!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2017 12:18 PM
Hi Man,
Thanks for the info. very informative. But, I would like to ask how do you create a policy using app and url filtering? http://imgur.com/psscJvm in this photo we can see that i have created a policy called "BROWSE" and APP group was only googlebased named as "WEB-BROWSING" w/ url filtering enabled, I also add on whitelist the "instagram" url and blocklist "speed" is it possible?
Second is i created a policy for banking named as "Banking" now since we cannot determine or i don't want to filter on app and just use url filtering and whitelist the following site, "User1" will able to access skype even though hes not included on "Skype Policy" and user1 will use the banking policy which App is in "ANY"?
In that case the policy will not be a good for user and hr for example. Also another example I want to block create a policy that will blocked specific url for all segment. What app category should i user? and should i put in higher seq. no.?
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2017 08:04 AM
It would be easier if you just take a screenshot of your policies and actually post that; as far as what you posted there isn't enough information to say for certain what the rule actually looks like. That makes things easier to allows us to see what you are actually doing, as it sits the very first rule that you have listed would allow users to visit pretty much every site since you've included SSL any allow.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-21-2017 09:58 PM
Hi,
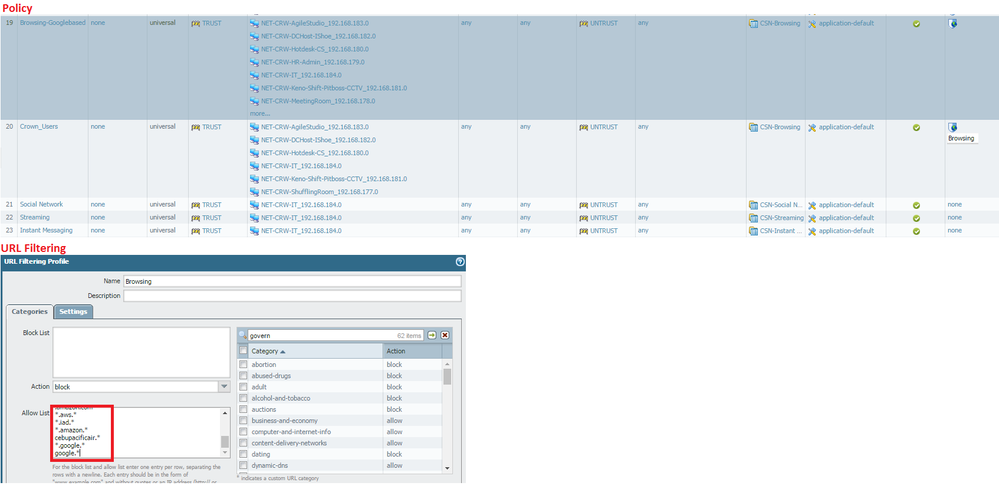
As requested kindly see the below photo.
I created a policy "Browsing (Google based)" and created a URL filtering "Browsing" in it and has the list of whitelist urls which i need oto allow/access.
Is this setup is possible?
Since upon checking some of the whitelist url still not working?
ex.
*.aws.* - not
*.iad.* - not
*.amazon.* - working
cebupacificair.* - working
Webpage error is "Application blocked" when trying to access the url on whitelist. How can we allow the those url even though we have app filtering that only allow google based?
Thank you and Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2017 01:10 PM
One important thing to remember is that a URL whitelist only means that the URL isn't going to get flaged for any category. For example if I have adult blocked but I whitelist xxx.com then I'll be able to avoid the adult category block and actually go to xxx.com since it's in the whitelist.
The pictures provided give a little bit more insight into what could actually be going on, thanks! When you say that you built out a Google-Base allow rule is that the only application that you are allowing through the rule? I see that you have an application group, but I can't see what you actually have in it. If you are going to be allowing traffic on a strict application level then you need to know what application that traffic is actually going to show up as.
For Example:
AWS- Amazon has a lot of different signatures, so if you are going to the aws console you would need to allow the amazon-aws-console application, some aws traffic is categorized simply as ssl or web-browsing, amazon-cloud-drive is it's own application.
Amazon- Again, different services have different signatures; amazon-workspace, amazon-unbox, amazon-redshift, amazon-instant-video, and amazon-cloud-player are all additional signatures that you potentially need to have access to.
I'm not sure about the other two sites but they are likely identified as an application that actually isn't in your applicaiton group, which is why you are running into that message.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-30-2017 04:45 AM
Thanks for the info. But, just to verify in your product are you using app w/ url filtering on same policy? because if we are going to enable that feature (APP) there's so many things that we need to enable. ?
Could give us sample? What is the best way to deploy?
Again Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-30-2017 10:13 AM
What exactly are you trying to lock down/setup? So an example for this would be if you were setting up a rule to allow Skype you wouldn't just enable the Skype id and be good to go; you would enable office365-consumer-access, skype, skype-probe, stun, ssl, websocket, and web-browsing. Applications are going to have either dependants or say that it implicitly uses different applications as well as that one app id, this info can be found under objects in the applicaiton field or on applipedia.
If this is the first time that you are setting up this firewall I would personally create a trust zone to untrust zone rule and configure it to log with any application and any service. Put this at the end of your rule list and build whatever rules you are trying to setup on top of this rule. This way you can continue to work on rules without hindering traffic and you can monitor the logs to verify what applications your users are trying to use and build up from there.
- 6920 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Need clarification on URL Filtering logs in Next-Generation Firewall Discussions
- Log forwarding - Filtering and Auto- tag not working in General Topics
- SMB share - Right clicking shared folder and selecting folder properties in Next-Generation Firewall Discussions
- Clientless VPN Applications and Application Groups in GlobalProtect Discussions
- GlobalProtect | External Gateway | SAML | Reconnect Issue in GlobalProtect Discussions