- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Captive Portal With SSO Breaks All Rules
- LIVEcommunity
- Discussions
- General Topics
- Captive Portal With SSO Breaks All Rules
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2017 11:37 AM
Hello ALL -
This is my second post here regarding Captive Portal. I enabled Captive Portal in my environment the other day thinking it would be for webaccess for my users in the event the User ID tool did not work. Upon enabling this feature other rules on my firewall stopped processing since there was no users associated with those rules.
Is this really the way that Captive Portal is supposed to work? I have a rule that allows a certain IPA to ping an external resource, when captive portal is enabled the rule stops working till I authenticate through the captive portal and there is a user to IP mapping regadless if my rule has an associated user listed in it.
That seems like a huge flaw to me especially since I have service like DNS that do not run as any user.
Just so you are all aware, I am currenlty running 2 850's in HA on 8.0.3
I really need a way for users to authenticate for web access if User ID fails without breaking all my other firewall rules. I thought that enabling the captive portal would allow them to authenticate that way. My SSO rule covers my entire subnet as my network environment is flat network with no segregation between servers and clients(this could be changed if needed to get things to work) as I think this might be causing part of the issue.
Any help would be appreicated.
Thanks!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2017 06:40 AM
That's going to be your issue as you are making everyone authenticate. For anything that you don't want to be presented the captive portal you need to configure a rule to proceed without a broswer challenge, the default-no-captive-portal Authentication Enforment should work for that.
Alternatively modify the source address to just exclude your server IP range should work perfectly fine as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2017 07:11 AM
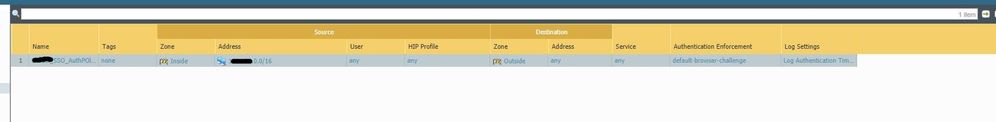
Can you send a screenshot of your Authentication policy list. If you have not made exceptions to allow the traffic to pass without authentication for the required source/destination on the proper app/service you will be presented with the captive portal page if that is how you have things configured. So in essence yes, this is how it will work until you tell it how to handle the traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2017 11:21 AM - edited 09-20-2017 11:24 AM
What you are saying makes sense. I am not sure how I would add the exception to say do not authenticate everyone. I have a group of users in AD that should be the only ones effected by the captive portal. Maybe I should put thier group in the SSO rule instead of Domain Users.?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2017 02:07 PM
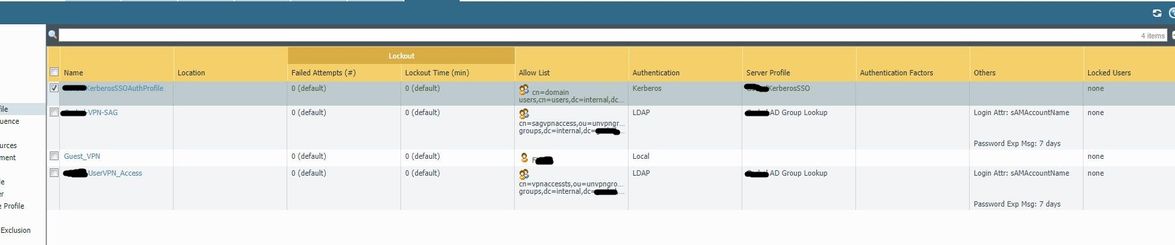
That appears to be your authentification profile. You should have a policy within the Policies tab on either Authentication Policy or It could be called Captive Portal policy depending on what version you are running.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2017 05:50 AM
Ahh, yes. Sorry, I guess I misunderstood what you were looking for. Here is the screenshot of what you want.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2017 06:40 AM
That's going to be your issue as you are making everyone authenticate. For anything that you don't want to be presented the captive portal you need to configure a rule to proceed without a broswer challenge, the default-no-captive-portal Authentication Enforment should work for that.
Alternatively modify the source address to just exclude your server IP range should work perfectly fine as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2017 10:52 AM
Ahhhh, yes. What you are saying now makes complete sense to me! I am requiring that everyone authenticate which I do not need. I just need certain users in certain subnets to authenticate. I will create another auth rule and put my servers in it and also change it to no captive portal. Thanks for the extra set of eyes on this BPry!!
- 1 accepted solution
- 3043 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Problem Using New Digitally Signed Certificate in GlobalProtect Discussions
- Connect Before Logon + Enforce GlobalProtect for Network Access + Captive portal in General Topics
- Captive Portal is not Working in Next-Generation Firewall Discussions
- LDAP User based policy not working in Next-Generation Firewall Discussions
- NTLM authentication 10.2 PANOS in General Topics