- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Configuring DNS sink hole on PA 3050 running PAN-OS 7.1.18
- LIVEcommunity
- Discussions
- General Topics
- Re: Configuring DNS sink hole on PA 3050 running PAN-OS 7.1.18
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 10:47 AM
I need assistance configuring/verifying if DNS Sinkholing is correct on my PA3020 running PAN-OS 7.1.18.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 02:34 PM
There really isn't a way to verify the object easily on the firewall, you have to get involved with the XML files that actually make up the device and peek around in the tech support file. If you look at the traffic logs for the sinkhole IP do you see any activity, and have you verified that you've setup logging on the rule you created to deny the traffic?
I wouldn't filter on the sinkhole app-id, that's kind of a bad test.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 12:03 PM
Here's the knowledgbase article for it HERE, if you have any specific questions please let us know.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 12:55 PM
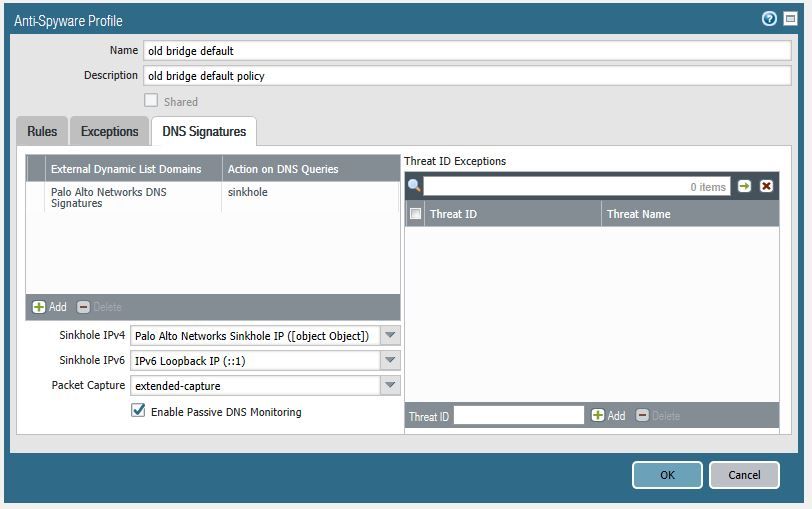
This is what I see when I choose Palo Alto Networks Sinkhole IP from the drop down
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 01:22 PM
Okay so outside of a few customizations it looks like you already have it configured and the IP of the default Palo Alto sinkhole IP is just failing to load. At the bottom of that query is a link to a verification document on how you would verify things are properly sinholing, but you should effectively be getting the response of 72.5.65.111 if you attempt to lookup a host that matches one of the DNS Signatures that are published.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 01:55 PM
So I followed step 4 of the query and created the security rule with the Palo Alto Default sinkhole address (72.5.65.111) as the destination and moved it to the top. If I look at threat logs I still see my internal DNS servers IP addresses if I filter by app eq sinkhole.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 01:59 PM
Anywhere I can verify that Palo Alto sinkhole IP object on the firewall?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2018 02:34 PM
There really isn't a way to verify the object easily on the firewall, you have to get involved with the XML files that actually make up the device and peek around in the tech support file. If you look at the traffic logs for the sinkhole IP do you see any activity, and have you verified that you've setup logging on the rule you created to deny the traffic?
I wouldn't filter on the sinkhole app-id, that's kind of a bad test.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-19-2018 09:13 AM
I'm seeing sinkhole IP activity on two of my current PA security rules now that I've confirmed logging is enabled on both session start and end. The Block-Sinkhole security rule I've implemented to drop indicates one source address currently hitting the sinkhole IP.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-19-2018 09:25 AM
I've refreshed the monitor and now it appears my sinkhole rule is dropping any source IP to the destination sinkhole IP. Thanks for all your help. Have a great holiday!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-19-2018 09:46 AM
One other question is as to what I should be looking into as far as the threat log and the sinkhole type action. I'm still seeing that traffic to a few of my on premise domain controllers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-19-2018 10:26 AM
So I'm just guessing on your setup here, but I would expect with what you're seeing the domain controllers are also acting as your DNS servers? If that's the case, it simply means that one of the clients on your network is making DNS requests that match the published DNS Signatures, likely because the requested hostname is malicious in nature.
Unless you have a way to see the actual host -> DNS traffic, or you are loggign the DNS requests on the server, you really won't get a huge amount of actionable data. As of this moment the only thing you know for sure is that someone in your network is causing the DNS servers to make malicious DNS requests; without additional logs that isn't extremely helpful for you.
- 1 accepted solution
- 4372 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- VPN error message after upgrading PAN-OS to 10.1.10-h2 in General Topics
- Stuck in - Server rebooting - please wait while the server reboots in Next-Generation Firewall Discussions
- Global Protect Disconnects Frequently in GlobalProtect Discussions
- Security rule says disabled no for an enabled policy in General Topics
- Disk usage for /opt/pancfg exceeds limit, 100 percent in use in General Topics