- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cryptocurrency Mining?
- LIVEcommunity
- Discussions
- General Topics
- Cryptocurrency Mining?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 11:20 AM
Hi folks,
We recently had a pen test and had positive results. We do not use URL filtering, but have everything else.
However, on 12/24/2017 we can now see a reboot.txt file sitting in our Windows\temp directory on an Oracle OAM server.
Luckly, Carbon Black flagged the file as it was trying to be run and denied, running from cmd.exe.
We can also see a new Windows task scheduler task created on 1/2/2017 that calls to run schtask1.ps1, that we did not create. Also cannot find that file. Did a restore of the VM to 12/21/2017, no trace of these new files and settings.
We continue to our threat alerts denying malicious traffic. Quick searches so far seem to indicate cryptocurrency mining.
I see there are a couple of PA references out there for this.
Curious if anyone has any comments as we continue our investigation or any of this rings a bell?
I've been searching our traffic logs for cryptocurreny as mentioned here, but nothing so far.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 08:17 AM
Thank you guys for the responses.
Even though I feel this demonstrates that I am still learning and need to focus more time in reviewing our profiles, wanted to post this update for record, and others.
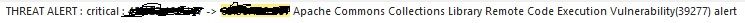
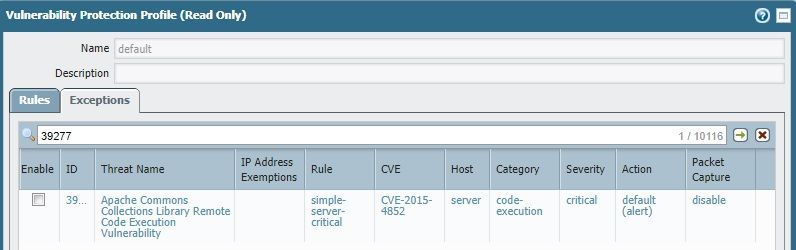
After reviewing with terrific PA support, I believe the issue started with the fact that our Vulnerability profile was set to default (long before I got here). Therefore, the threat in question was processed as its default action, alert (instead of reset both).
Seems that the traffic was able to pass and then the server in question is an Oracle Weblogic server that was not patched to resolve this exploit!
Since we had Carbon Black in place, the threat was unable to run. One of the behaviors was a powershell script would try to run scheduled or periodically and we blocked powershell to run and monitored its attempts.
We corrected our vulnerability profile, restored the Oracle server from backup (previous to exploit) and so far we have no other powershell execution attempts and see that the threat is now identified and blocked at the firewall (reset both).
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 12:20 PM
Hello,
Sorry for your troubles, never a good time. As a quick solution, you may want to try the following. While you wont get the bells and whistles without being a customer, it will block DNS qureies to their known bad sites:
https://www.opendns.com/setupguide/
Also take a look at https://live.paloaltonetworks.com/t5/Configuration-Articles/How-to-Configure-DNS-Sinkhole/ta-p/58891
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 02:10 PM
The steps mentioned in that Reddit article are pretty good, and would be my immediate reaction. Honestly though you should really be looking at how someone was able to access your OAM server in the first place and mitigate that. Crypto mining isn't really a 'threat' per say, since they are just stealing your resources. However, if enough access to your server is actually allowed for this to happen then you could be leaving yourself open to bigger issues in the future.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 02:15 PM
Thank you for the feedback folks.
BPry
Yes, I we are wondering how access was gained. This is a server behind our PA with an internal IP, behind a load balancer with an internal IP. We do NAT of course from a public IP to the load balancer private IP.
We do see that there are several Weblogic patches for vulnerabilities, and we are likely out of date. But trying to figure out how access was gained in the first place.
Still investigating...
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 02:43 PM - edited 01-03-2018 02:49 PM
BPry
Otakar.Klier
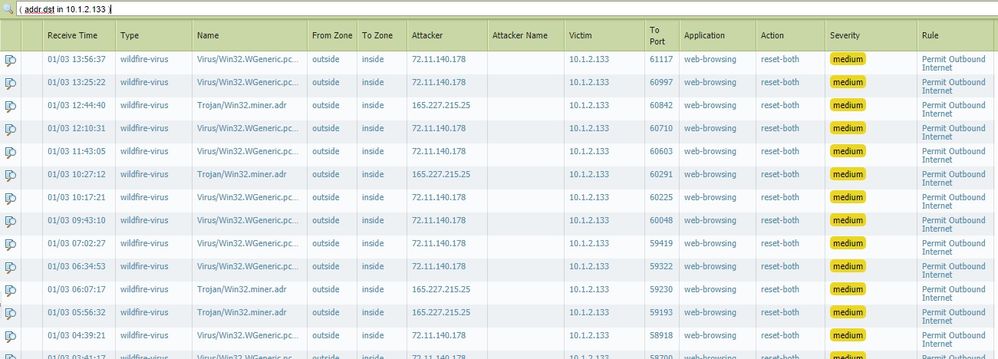
I see there are wildfire traffic and threat detection coming from this server in question. The rule is an outbound to internet rule.
Would this mean that this server is in fact infected some how?
Since it is using wildfire, would that mean unknown or zero day perhaps?
I also see this server attempting to reach out to the internet and session ends in threat.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 02:51 PM
I would say that its a safe bet the system is compromised. I would not hestitate to implement your incident response plan if you have one.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 02:54 PM
Thank you Otakar.Klier
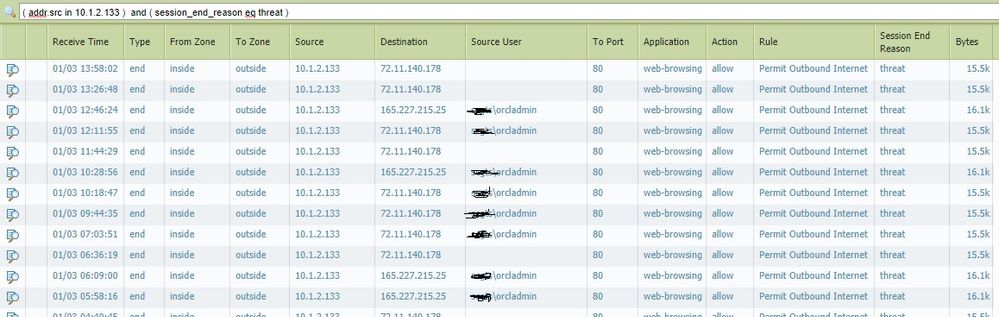
Would you know if the reset-both action means that the traffic is denied or dropped?
I mean that's what the PA is doing here, right?
Detecting the attempts of outgoing traffic as malcious?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 02:58 PM - edited 01-03-2018 02:59 PM
You are correct. PAN see's malicious traffic and is blocking it.
There are several types of actions the PAN can take.
- a silent drop is useful if obscurity is preferred.
- reset-client is useful when user experience is key, the application will immediately be able to let the user know a connection is not available.
- reset-server is useful when internal resources need to be protected from excessive resource consumption due to half-open sockets.
- reset-both will provide best user experience and protect servers' resources, but may facilitate malicious use.
- zone protection will add protective mechanisms that allow a more userfriendly experience while still protecting against abuse.
A reset both just means that the PAN sent a close socket to both the attacker and victim in this case to prevent a DoS scenario.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 03:04 PM
Here is some info on those IP's:
https://www.virustotal.com/en/ip-address/165.227.215.25/information/
https://www.virustotal.com/en/ip-address/72.11.140.178/information/
I would say it depends on what you are looking for as your next steps. Some like to let the traffic continue and try and analyze to see if they can figure out where it can from. Others just want to shut it down ASAP, meaning put in policies to deny traffic to/from those IP's and any others that are not legit.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 03:13 PM
Thanks again.
I guess the trick is to know which are legit or not, and block them automatically if not legit.
We have not made any changes to remediate yet, since Carbon Black seems to be preventing it to run and PA is blocking traffic. But don't know how it got there in the first place.
We have a call with a security provider tomorrow morning...will update.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2018 03:25 PM
Best of luck. Also CB isnt catching everything since something is running and attempting to make those call outs. If you have a next gen AV package, it might be worth a shot to install it. If you dont I like to use Immunet. Its free, cloud based, and backed by some good intel.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 08:17 AM
Thank you guys for the responses.
Even though I feel this demonstrates that I am still learning and need to focus more time in reviewing our profiles, wanted to post this update for record, and others.
After reviewing with terrific PA support, I believe the issue started with the fact that our Vulnerability profile was set to default (long before I got here). Therefore, the threat in question was processed as its default action, alert (instead of reset both).
Seems that the traffic was able to pass and then the server in question is an Oracle Weblogic server that was not patched to resolve this exploit!
Since we had Carbon Black in place, the threat was unable to run. One of the behaviors was a powershell script would try to run scheduled or periodically and we blocked powershell to run and monitored its attempts.
We corrected our vulnerability profile, restored the Oracle server from backup (previous to exploit) and so far we have no other powershell execution attempts and see that the threat is now identified and blocked at the firewall (reset both).
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 10:24 AM - edited 01-08-2018 10:27 AM
@OMatlock wrote:Thank you guys for the responses.
Even though I feel this demonstrates that I am still learning and need to focus more time in reviewing our profiles, wanted to post this update for record, and others.
After reviewing with terrific PA support, I believe the issue started with the fact that our Vulnerability profile was set to default (long before I got here). Therefore, the threat in question was processed as its default action, alert (instead of reset both).
Seems that the traffic was able to pass and then the server in question is an Oracle Weblogic server that was not patched to resolve this exploit!
Since we had Carbon Black in place, the threat was unable to run. One of the behaviors was a powershell script would try to run scheduled or periodically and we blocked powershell to run and monitored its attempts.
We corrected our vulnerability profile, restored the Oracle server from backup (previous to exploit) and so far we have no other powershell execution attempts and see that the threat is now identified and blocked at the firewall (reset both).
I think this highlights an important fact...It's not necessarily always best to accept a "standard config." At my company I went ahead an made the decision to override the defaults of all "Critical and High" signatures to a "reset." Just for this very reason. I'd rather respond to "why is something being blocked" versus "how did we get compromised.
Your scenario does highlight a positive though...Defense-in-Depth. While one source of protection may not be sufficient, either from misconfiguration or a straight failure, others should always be in-place to catch what might be missed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 10:46 AM
As @Brandon_Wertz mentioned I highly recommend overriding severity Critical and High threats to simply reset the connection. In some cases I've even assigned medium severity to reset-both as well. In my experiance it hasn't caused a lot of issues; and even when it has it's an easy discussion to have. "Hey I can't do this thing" is pretty easy to explain away; "Hey my computer/server is doing this thing" is a lot harder of a conversation.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 03:15 PM
Hello,
I have to agree with @BPry and @Brandon_Wertz, its time to maybe review your settings. Personally I have anything medium and higher set to block.
Regards,
- 1 accepted solution
- 4736 Views
- 16 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!