- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
DNS proxy and strange system logs entries
- LIVEcommunity
- Discussions
- General Topics
- Re: DNS proxy and strange system logs entries
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
DNS proxy and strange system logs entries
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2013 09:25 AM
Hi
I'm using dns proxy from two weeks. Today I observed strange entries in logs:
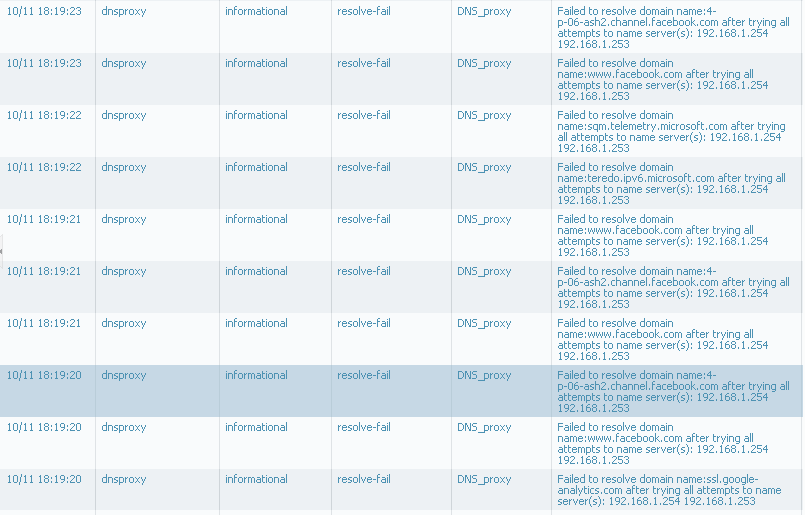
my configurqation is simple:
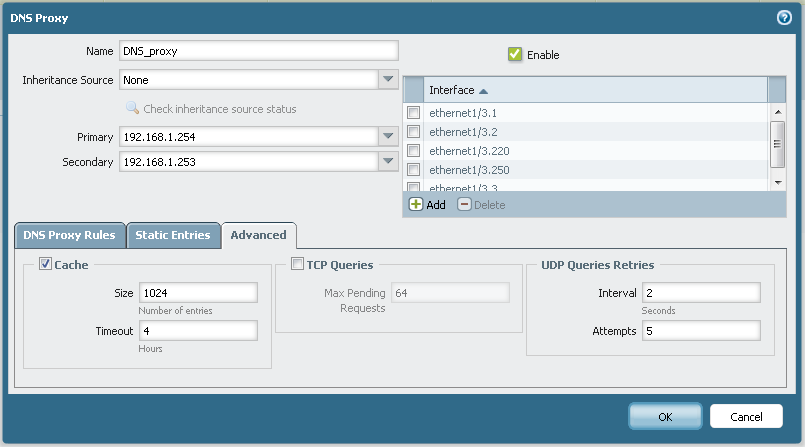
Could someone help me to undestrand what is going on?
Regards
Slawek
- Labels:
-
Networking
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2013 09:27 AM
These errors indicate connectivity issues to the configured DNS servers. Has there been any events which may have caused a loss of connectivity between the firewall and those IPs?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2013 12:05 PM
No, those two DNS servers was "pingable" all the time.
Also "DIG google.com" gives me answer - lunched from computer from one of network with dns_proxy.
Any idea how to troubleshoot it ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-13-2013 03:13 PM
Start with enabling debug for dnsproxyd and checking dnsproxy logs
> debug dnsproxyd global on debug ===>ENABLE debug
> less mp-log dnsproxyd.log ===== CHECK logs
> debug dnsproxyd global on info ===>DISABLE debug
Possible Issues:
1> Server Sending DNS Response larger than 512 bytes
Extended DNS (>512B) option not supported with PA as proxy.
2> DNSproxy logs show " No buffer space available."
Fixed with OS-5.0.8
Bug 50813—DNS proxy fails to proxy traffic with bursts of DNS requests, displaying the
error: (errno: 105) No buffer space available. This was resolved by
increasing the buffer.
3> Sessions for sourced from dnsproxy interface to the server being scanned spyware profile being discarded.
Configure a security rule to bypass threat scanning for the traffic to the DNS server sourced from DNSproxy interface.
You can enable threat scanning for traffic from the original clients to DNS proxy and also DNS response traffic (public DNS servers) if needed.
HTH,
Ameya
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-14-2013 07:33 AM
Thank You for very detailed answer!
I think that the best option for me will be upgrade to 5.0.8 and after check logs.
I had this errors ie 10.10.2013 about 13:58, in dnsproxyd.log a have enries:
Oct 10 14:52:58 Error: pan_dnsproxyd_recv_server_udp_cb(pan_dnsproxy_udp.c:487): [Drop Rcvd Server Pkt]: Error in processing packet
Oct 10 14:54:57 Error: pan_dnsproxy_process_server_pkt(pan_dnsproxy_pkt.c:1335): [14122/-][Drop Rcvd Server Pkt]: No pending entry in conn tbl for server_tid:14122
Oct 10 14:54:57 Error: remove_conn_tbl_entry(pan_dnsproxy_pkt.c:284): conn_tbl[14122] entry is already freed!
Oct 10 14:54:57 Error: pan_dnsproxyd_recv_server_udp_cb(pan_dnsproxy_udp.c:487): [Drop Rcvd Server Pkt]: Error in processing packet
Oct 10 14:55:37 Error: pan_dnsproxy_process_server_pkt(pan_dnsproxy_pkt.c:1335): [44552/-][Drop Rcvd Server Pkt]: No pending entry in conn tbl for server_tid:44552
Oct 10 14:55:37 Error: remove_conn_tbl_entry(pan_dnsproxy_pkt.c:284): conn_tbl[44552] entry is already freed!
Oct 10 14:55:37 Error: pan_dnsproxyd_recv_server_udp_cb(pan_dnsproxy_udp.c:487): [Drop Rcvd Server Pkt]: Error in processing packet
Oct 10 15:06:14 Error: cfgagent_modify_callback(pan_cfgagent.c:81): Modify string (sw.mgmt.runtime.clients.dnsproxyd.err) error: Unknown error code (1)
Oct 10 15:10:36 Error: pan_dnsproxy_query_done_cb(pan_dnsproxy_pkt.c:772): Cache entry not found for Wsadecka.feris.pl.
Oct 10 15:52:34 Error: pan_dnsproxy_process_server_pkt(pan_dnsproxy_pkt.c:1335): [26579/-][Drop Rcvd Server Pkt]: No pending entry in conn tbl for server_tid:26579
Oct 10 15:52:34 Error: remove_conn_tbl_entry(pan_dnsproxy_pkt.c:284): conn_tbl[26579] entry is already freed!
Oct 10 15:52:34 Error: pan_dnsproxyd_recv_server_udp_cb(pan_dnsproxy_udp.c:487): [Drop Rcvd Server Pkt]: Error in processing packet
Oct 10 15:53:00 Error: pan_dnsproxy_process_server_pkt(pan_dnsproxy_pkt.c:1335): [36977/-][Drop Rcvd Server Pkt]: No pending entry in conn tbl for server_tid:36977
Oct 10 15:53:00 Error: remove_conn_tbl_entry(pan_dnsproxy_pkt.c:284): conn_tbl[36977] entry is already freed!
is everything OK in this logs?
How to make rule for >3
In my scenario I have DNS servers in Zone A, clients in Zone B, my security rule:
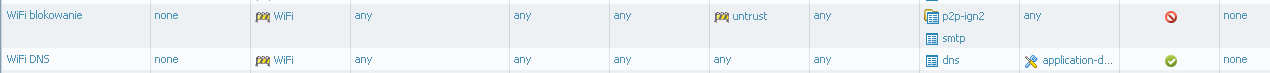
Should I add rule that alloving traffic from WiFi zone (with source IP = gateway IP for this zone) to Zone A?
>You can enable threat scanning for traffic from the original clients to DNS proxy and also DNS response traffic (public DNS servers)
How to achieve that?
Should I make rule from WiFi to WiFi app=dns with enabled thread prevention profile on it?
Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-14-2013 01:55 PM
This seems to be an issue related to configuration of Threat scanning as logs do not indicate any Buffer related messages.
You should be able to confirm this by checking the session table for destination = DNS server in DISCARD state during the failure.
Assuming :
Clients and DNSproxy Interface===>ZONE WiFi
DNS servers - Zone B
You an create a security policy as follows:
Zone WiFi to Zone WiFi app=dns with enabled thread prevention profile .
Zone WiFi to Zone B app=dns Destination IP : DNS servers ==> Should not have threat profiles.
HTH,
Ameya
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-16-2013 12:45 AM
From 10.10.2013 I had no problem with dns proxy so I can't do any further investigations. I'm waiting for another issue with dns proxy.
Regards
SLawek
- 5634 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Way to dual-boot MacOS without violating encryption requirements for GlobalProtect? in GlobalProtect Discussions
- PaloAlto Predefined IP Lists not appearing in General Topics
- DNS Issue on Debian 12.5 and other by using GP 6.1.3 on PA1420 11.0.3-H3 in GlobalProtect Discussions
- SIP Invites timing out for certain calls in General Topics
- Set a new GlobalProtect VPN portal to prisma for 1000+ devices in General Topics



