- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
HOWTO Wanted : Trunked L3 intrerface with tagged VLAN's
- LIVEcommunity
- Discussions
- General Topics
- Re: HOWTO Wanted : Trunked L3 intrerface with tagged VLAN's
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-27-2019 09:10 PM
Hi folks.
I need to configure a L3 iterface with a trunked conenction to my core switching infrastructure - twos eperate VLAN's on the one physical interface which MUST be seprate VLAN's, security zones and IP ranges.
I can't figure out if I'm mking this work right - I add sub interfaces tot he physical interface configuration, and they are tagged - but the main interface isn't.
Do I need to create VLAN's to match the sub-interface definitions? VLAN INterfaces? Or does the act of creating the sub interface get it working?
I'm quite confused over this one.
Thanks.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2019 01:41 PM - edited 05-28-2019 01:42 PM
See this comment for the difference between VLAN interfaces (which are actually bridged interfaces for creating a virtual switch) and layer 3 interfaces with 802.1q vlan tags (which is probably what you are looking for):
When you say "trunk" do you mean a vlan trunk (meaning only tagged vlans on the physical interface, no untagged vlans), or an LACP trunk (where you bond together multiple physical interfaces into a single aggregate interface to increase throughput or provide fail-over)?
I really hate it when the same terms are used for different things based solely on context. 🙂
I'm guessing you want to create a single Layer 3 interface (you don't have to actually configure anything on it), then create multiple sub-interfaces underneath the physical interface, with each sub-interface having a vlan tag associated with it. Thus creating a vlan trunk. We do this on all our firewalls. Each sub-interface can be configured with it's own Zone, Virtual Router, Zone Protection, Management Profile, etc (they're treated as separate interfaces).
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2019 12:01 PM
Hello,
In the past I have always made the physical interfaces layer2. Make sure the sub interfaces are tagged for the specific vlan. I then create a layer3 vlan interfaces for routing of the traffic.
You can do the same with layer3 physical interfaces, just make sure you Tag them to what the vlan is.
Interface Name | Layer3 Subinterface | The read-only Interface Name field displays the name of the physical interface you selected. In the adjacent field, enter a numeric suffix (1-9,999) to identify the subinterface. |
Comment | Enter an optional description for the subinterface. | |
Tag | Enter the VLAN tag (1-4,094) for the subinterface. |
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2019 01:41 PM - edited 05-28-2019 01:42 PM
See this comment for the difference between VLAN interfaces (which are actually bridged interfaces for creating a virtual switch) and layer 3 interfaces with 802.1q vlan tags (which is probably what you are looking for):
When you say "trunk" do you mean a vlan trunk (meaning only tagged vlans on the physical interface, no untagged vlans), or an LACP trunk (where you bond together multiple physical interfaces into a single aggregate interface to increase throughput or provide fail-over)?
I really hate it when the same terms are used for different things based solely on context. 🙂
I'm guessing you want to create a single Layer 3 interface (you don't have to actually configure anything on it), then create multiple sub-interfaces underneath the physical interface, with each sub-interface having a vlan tag associated with it. Thus creating a vlan trunk. We do this on all our firewalls. Each sub-interface can be configured with it's own Zone, Virtual Router, Zone Protection, Management Profile, etc (they're treated as separate interfaces).
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2019 05:29 PM
@fjwcash wrote:See this comment for the difference between VLAN interfaces (which are actually bridged interfaces for creating a virtual switch) and layer 3 interfaces with 802.1q vlan tags (which is probably what you are looking for):
When you say "trunk" do you mean a vlan trunk (meaning only tagged vlans on the physical interface, no untagged vlans), or an LACP trunk (where you bond together multiple physical interfaces into a single aggregate interface to increase throughput or provide fail-over)?
I really hate it when the same terms are used for different things based solely on context. 🙂
I'm guessing you want to create a single Layer 3 interface (you don't have to actually configure anything on it), then create multiple sub-interfaces underneath the physical interface, with each sub-interface having a vlan tag associated with it. Thus creating a vlan trunk. We do this on all our firewalls. Each sub-interface can be configured with it's own Zone, Virtual Router, Zone Protection, Management Profile, etc (they're treated as separate interfaces).
OK, the comment you quoted makes it a bit clearer - a "vlan" interface is simply used to make ports into local switch ports.
Yes, I mean VLAN trunk - a port which allows ONLY tagged traffic in one (or more) VLAN's in and out - connected to a "trunk" port on a switch (trunk mode switch port in Cisco/Juniper land).
And yes, I hate it when the same word means two completely different things depending on which vendor you're talking to as well! 🙂
Based on your last paragraph, what I have should work, as that's exactly what I've done - my only concern is that the "physical" interface is listed as "untagged" - does that mean it passes native VLAN traffic with a default (1) tag, or passes nothing at all?
Thanks - I think you've cleared this up enough that I can make things work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2019 03:43 PM
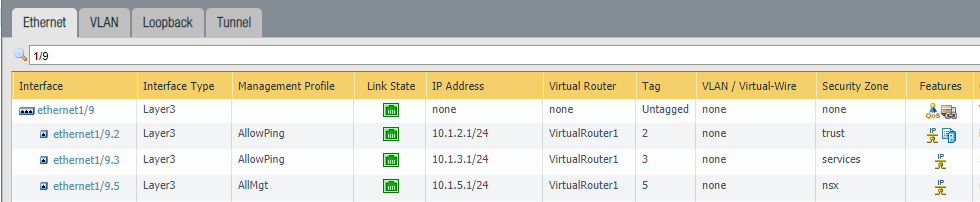
Here's a screenshot from my firewall. Instead of using "layer-2" with "vlan interfaces" - I usually use straight layer-3 subinterfaces. This picture should explain it all. No need for a vlan interface with this type of configuration:
You're correct that traffic may hit the parent "ethernet1/9" interface - but that will only happen if the VLAN trunk from your switch includes an untagged (aka "native") vlan as well. Even that shouldn't be a problem since this particular interface on the firewall: 1.) isn't part of a VR, 2.) doesn't have an IP address, and 3.) isn't a member of any security zone.
- 1 accepted solution
- 7877 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- L2 trunks between 3 Cisco switches in General Topics
- Multiple vsys share one pair of WAN circuits? in Next-Generation Firewall Discussions
- Single Interface Trunk Hairpin problem for All traffic traversing Firewall? in General Topics
- Palo Alto unable to route traffic into LACP trunked subinterface vlans in General Topics
- HOWTO Wanted : Trunked L3 intrerface with tagged VLAN's in General Topics