- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to Enable WildFire to block jar file with 'malicious' Verdict
- LIVEcommunity
- Discussions
- General Topics
- Re: How to Enable WildFire to block jar file with 'malicious' Verdict
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to Enable WildFire to block jar file with 'malicious' Verdict
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-31-2018 01:34 AM
Hello Everyone,
New to Palo Alto firewalls and new to this forum.
Can I please ask how I go about changing the Wildfire action on a jar file to block? The action for this file has been to allow the file, despite the file being flagged as "malicious, as can be seen below:
I wish to change the action to "block", as is the case with the "pe" files I can see in the Wildfire logs, as can be seen here:
Many thanks in advance.
Regards,
Steve
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-31-2018 08:14 AM
Within the Antivirus Security Profile that is assigned to the rule allowing the SMTP traffic to pass, you'll have to modify the 'WildFire Action' to reset-both instead of the default action of 'alert'. This article HERE should point you in the proper direction
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2018 09:08 AM
Dear BPry, many thanks for your reply.
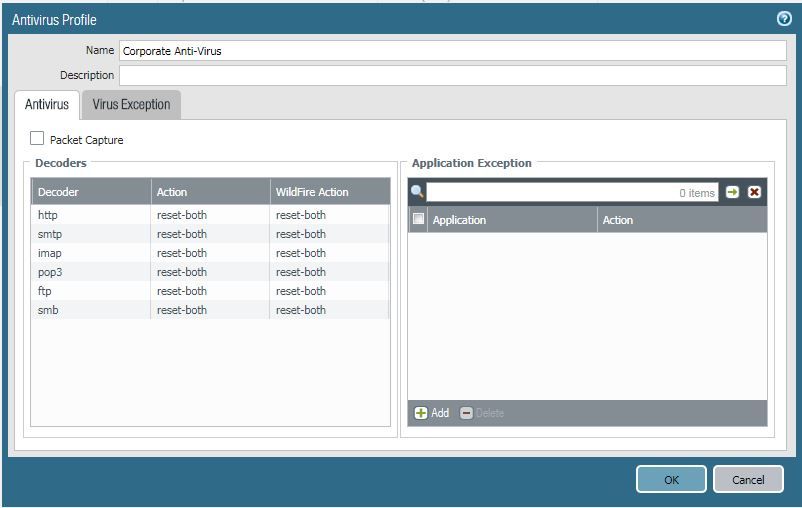
I have checked the Anti-Virus profile that is assigned to the applicable rule (Internet to Email Gateway) and the WildFire action is set to "reset-both" for all the listed decoders, including smtp, as can be seen here:
It would therefore seem that some other setting is at play here that is not immediately obvious.
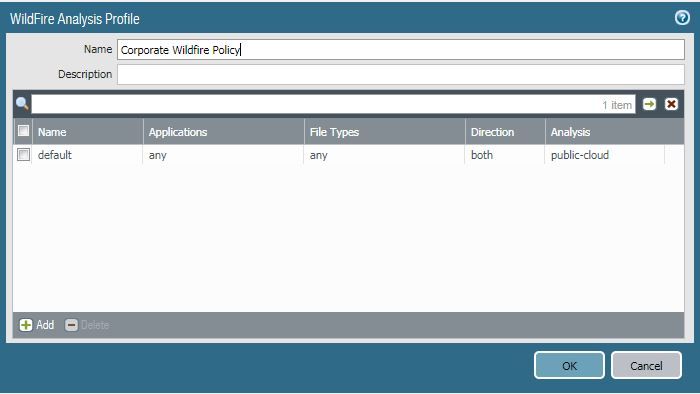
I have examined the WildFire Analysis security profile, but this is set to analyze any file type and any application, so there does not appear to be a applicable setting here:
I'll continue to investigate..
Regards,
Steve
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 05:58 AM
So one thing to potentially think about is if wildfire actually 'knew' about the file yet. A file that hasn't been inspected by WildFire which doesn't have identifyable markers for the Antivirus engine may log an as an 'alert' action until a wildfire signature has been generated for it. That may explain why you are seeing 'alert' actions rather than the desired 'reset-both' with this traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2018 01:36 AM - edited 02-08-2018 01:37 AM
Dear BPry,
Many thanks for your reply and theory for why the email was allowed despite being malicious.
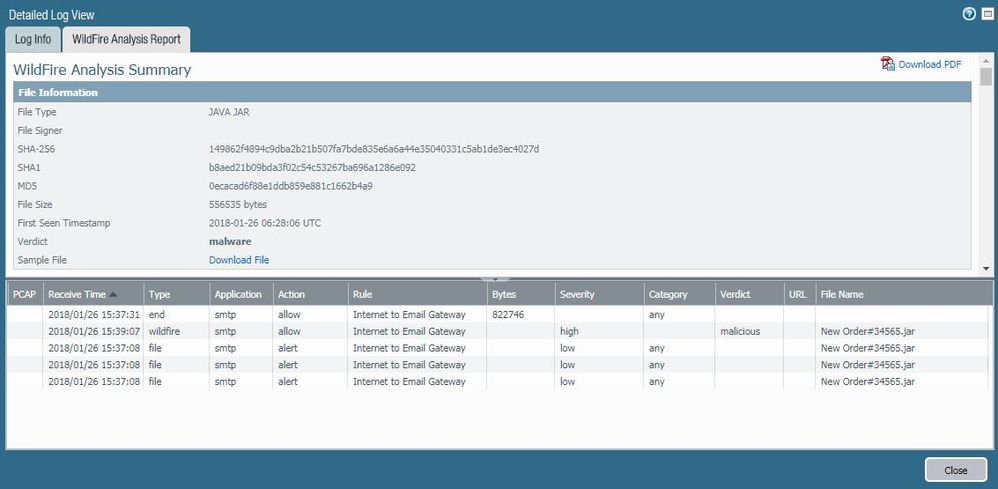
I have captured the timestamps of the Wildfire evets here, in case that helps accurately diagnose the issue:
WildFire Analysis Summary
Does this information give more visibility to the issue?
Many thanks,
Steve
- 2445 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- What's the difference between antivirus signatures and WildFire signatures in Threat & Vulnerability Discussions
- Cortex XDR flagged malicious macros in Cortex XDR Discussions
- Cortex XDR in Cortex XDR Discussions
- Advanced Wildfire Allowing High Severity Verdicts but blocking Informational in Next-Generation Firewall Discussions
- False positive swll.to in VirusTotal