- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to use multiple authentication profiles for Global Protect VPN
- LIVEcommunity
- Discussions
- General Topics
- How to use multiple authentication profiles for Global Protect VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2015 12:43 PM
I have a need for our employees to use LDAP in the authentication profile for VPN connectivity, but I also have outside third parties that need remote VPN connectivity as well. I want them to use local database user accounts. How can I do this? It seems that a given portal can only use 1 authentication profile type.
I only have 1 external interface with 1 IP address assigned. Is the solution to use loopback interface?
Thanks,
Ken
- Labels:
-
Configuration
-
Networking
-
Set Up
-
Troubleshooting
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2015 03:30 PM
Hi Kkrause,
You can refer following document. Its for four LDAP profiles. Instead you can have one Local Database and one LDAP.
Using More than Four LDAP Servers in a Palo Alto Networks Configuration
Let me know if that helps.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2015 02:04 PM
Hello Kkrause
Authentication profiles can be combined in an authentication sequence. If a user is not found on one of the LDAP servers in the first authentication profile it will attempt the next one, which should result in a successful authentication attempt as a whole on the firewall. This is configured under Device > Authentication Sequence:
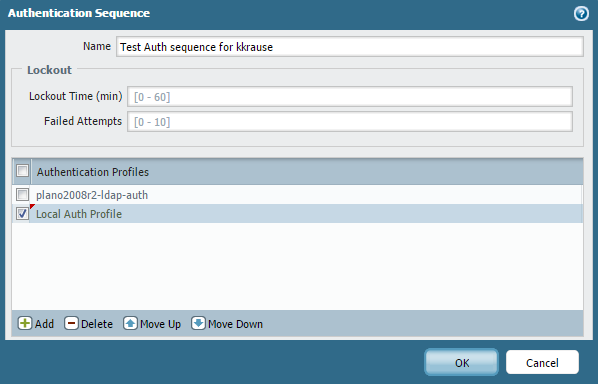
This sequence can now be used for any purpose, such as Global Protect authentication:
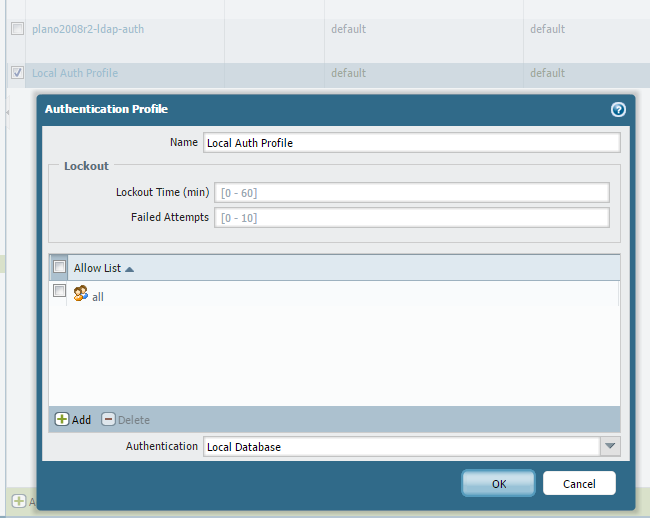
Hope that answers your question.
Regards
Khan
Note: Please mark any correct or helpful reply.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2015 03:30 PM
Hi Kkrause,
You can refer following document. Its for four LDAP profiles. Instead you can have one Local Database and one LDAP.
Using More than Four LDAP Servers in a Palo Alto Networks Configuration
Let me know if that helps.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2015 06:07 AM
Thanks for the response. I implemented the Authentication Sequence and I can see in my logs that the VPN authentication attempt is occurring on both the local profile and the LDAP profile. However I have a username/password issue for this particular user account that I need to resolve. I'm absolutely 100% sure that the username and password I'm testing with is correct and the account is enabled....so I'll check again ![]()
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2015 06:08 AM
Thanks for the response and additional documentation. It seems that the Authentication Sequence will take care of my needs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2015 07:58 AM
Hi KKrause,
Its top-down approach, first it check first method of authentication, if it doesnt authenticate than it go to next one. Let me know if this helps.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2015 01:35 PM
I found my password problem. I had changed the Portal to use Auth Sequence but not the gateway. Once I put that in place I can now VPN with my AD users and with my local database users. Oh, the joy of learning a new platform!
Thanks to all for the help.
- 1 accepted solution
- 13327 Views
- 6 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect windows negating/disabling RSA Authentication in General Topics
- GP HIP Profile Applied to Security Policy with Multiple Zones in GlobalProtect Discussions
- Group Mapping Nesting LDAP Filters in General Topics
- GP SAML authentication with multiple client configurations in gatway in GlobalProtect Discussions
- PaloAlto Predefined IP Lists not appearing in General Topics



