- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Issue NAT via VPN tunnel - VPN zone to Trusted zone
- LIVEcommunity
- Discussions
- General Topics
- Issue NAT via VPN tunnel - VPN zone to Trusted zone
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Issue NAT via VPN tunnel - VPN zone to Trusted zone
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 10:57 AM
Hello
I'm having a very similar issue with trying to configure a NAT translation from VPN to Trusted zone. In my case I'm building a VPN tunnel for monitoring using /32 ProxyIDs. My configuration VPN ProxyID is like the example below:
Remote: Local:
3.3.3.3/32 172.25.40.3/32
My NAT is configured as follows.
Source Zone: Dest Zone: Source Address: Dest Address: Destination Trans:
VPN Trusted 3.3.3.3/32 172.25.40.3/32 10.100.10.10/32
I can't get the translation to happen when send pings from the VPN and that's what I need working.
If I switch from a Dest translation to Source translation it works when I ping from Trust to VPN.
Source Zone: Dest Zone: Source Address: Dest Address: Source Trans:
Trusted VPN 10.100.10.10/32 3.3.3.3/32 172.25.40.3/32
What am I missing? Do I need to add a static route for the V-Router? To get to 172.25.40.0/32 use tunnl.x?
Please advise. Thanks.
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2017 12:04 PM
I assume that you are not using 172.25.40.3/32 in your network internally.
It means that based on routing table traffic to this IP is sent towards Untrust zone.
So for NAT to match it should be VPN > Untrust (not Trust).
And you also might need second NAT rule if traffic is initiated from inside.
In this case it is Trust > VPN.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 10:35 AM
I'll try that. Thank you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2017 03:02 PM
I don't have an Untrusted zone as an option. But yes the 172.25.43.1/32 is just an object to match Proxy-ID setup in a VPN tunnel. It is not a part of an internal network. I do have active security polices allowing these Inside, DMZ and Subnets between them and the VPN zone.
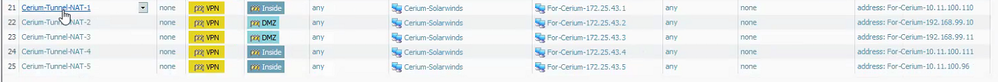
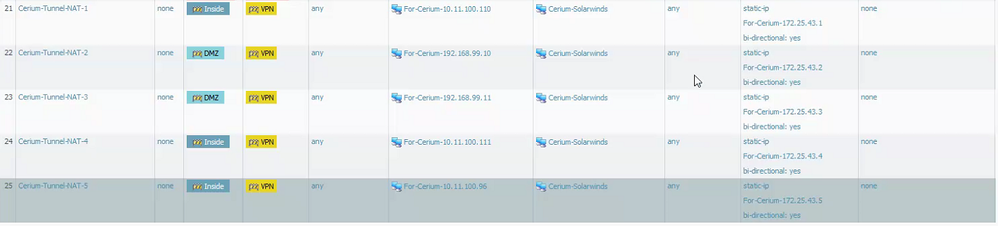
Below is the destination NAT that doesn't work.
These are source NAT entries that work only when traffic is initiated from Trusted or DMZ resouces. When traffic is initiated from the VPN resource it doesn't work. Even when Bi-Directional is enabled. On most firewalls this source NAT configuration set to Bi-Directional is all that is required.
- 2730 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Data Base application acees is slow through IPSEC Tunnel in Next-Generation Firewall Discussions
- Problem Using New Digitally Signed Certificate in GlobalProtect Discussions
- Moving from GP to Prisma access - Prisma prompts client to choose a certificate. in Prisma Access Discussions
- GP Internal Gateway does not work after upgrading to 10.2.7-h3 in GlobalProtect Discussions
- Tunnel Monitor - PAN-OS SDWAN in General Topics