- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Network Outbound baseline.
- LIVEcommunity
- Discussions
- General Topics
- Network Outbound baseline.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Network Outbound baseline.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 09:10 AM
I need to provide a baseline of allowed traffic outbound for a period of time.
So to list
Client -> External Server [ Port/Application ]
Is there a report on the PA-3020 that can be crafted to do this
Thanks
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 09:20 AM
Hello,
A 'User Activity Report' might be what you are after. But if its to a specific exteranl IP and/or port, a custom report might be a better method. If this is a one time thing, perhaps the Unified logs would give you what you are looking for?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 10:12 AM
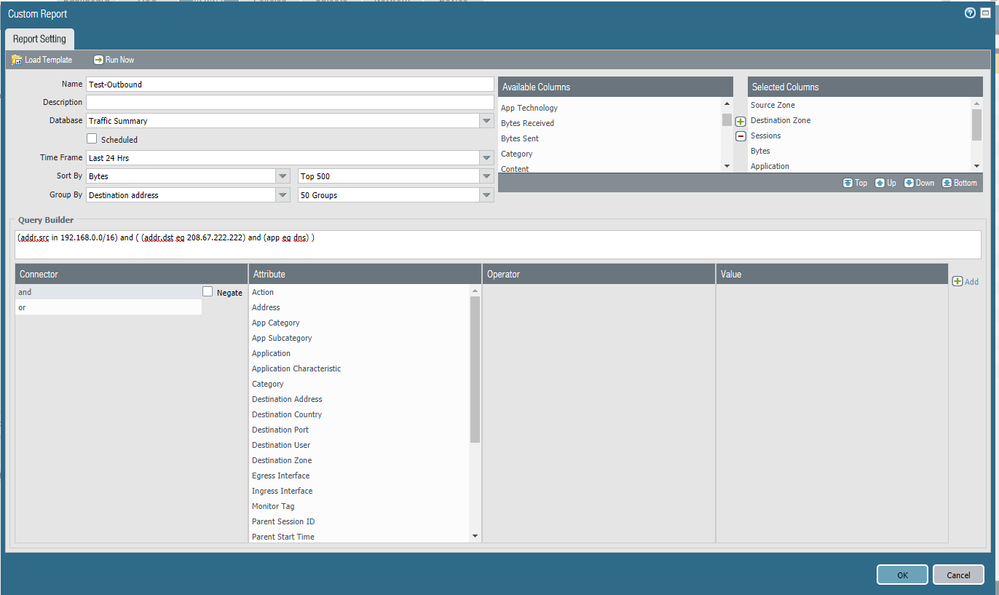
Sure. I've provided a sample of a custom report that could be utilized for a 24hr period as an example. The example simply shows traffic going to opendns with the application being dns.
<entry name="Test-Outbound">
<type>
<trsum>
<sortby>bytes</sortby>
<group-by>dst</group-by>
<aggregate-by>
<member>from</member>
<member>to</member>
<member>app</member>
<member>src</member>
</aggregate-by>
<values>
<member>sessions</member>
<member>bytes</member>
<member>nunique-of-apps</member>
</values>
</trsum>
</type>
<period>last-24-hrs</period>
<topn>500</topn>
<topm>50</topm>
<caption>Test-Outbound</caption>
<query>(addr.src in 192.168.0.0/16) and ( (addr.dst eq 208.67.222.222) and (app eq dns) )</query>
</entry>
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2018 01:32 AM
I need all unique instances of allowed traffic.
192.168.1.5 - 8.8.8.8 - DNS
192.168.1.5 - 8.8.4.4 - DNS
192.168.1.6 - 8.8.8.8 - DNS
192.168.1.5 - 8.8.8.8 - https
192.168.1.5 - 8.8.8.8 - DNS
192.168.1.6 - 178.16.40.90 - https
192.168.1.6 - 8.8.8.8 - DNS
So that no entries are repeated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-15-2018 05:52 AM
Really isn't an amazing way to do this from a custom report then. Since you are locating DNS traffic you're going to be looking at a lot of sessions and you'll quickly reach the limits on how large the custom reports can actually be. Your best bet to fullfil this is likely going to be simply filtering the 'traffic' or 'unified' logs and simply exporting the results.
Depending on what you are looking to do with this information you could simply seperate the queries based off of source address, or run all the queries individually.
( ( addr.src in 192.168.1.5 ) and ( addr.dst in 8.8.8.8 ) and ( app eq dns ) ) or ( ( addr.src in 192.168.1.5 ) and ( addr.dst in 8.8.4.4 ) and ( app eq dns ) ) or ( ( addr.src in 192.168.1.6 ) and ( addr.dst in 8.8.8.8 ) and ( app eq dns ) ) or ( ( addr.src in 192.168.1.5 ) and ( addr.dst in 8.8.8.8 ) and ( port.dst eq 443 ) ) or ( ( addr.src in 192.168.1.6 ) and ( addr.dst in 178.16.40.90 ) and ( port.dst eq 443 ) )
You'll notice that the queries for the https traffic I simply did a destination port of 443. This is because I simply didn't know what the application would usually return as. Likely the app would be SSL on either, but you'd either want to run it simply as the dst port search or actually verify in the logs what that traffic is getting identified as and switch it out in the query.
- 2735 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Inbound Policy-Based Forwarding Issue - Intermittent loss of connectivity in Next-Generation Firewall Discussions
- SIP Invites timing out for certain calls in General Topics
- AWS: GWLB endpoint mapping in Central Design Model in VM-Series in the Public Cloud
- Demystifying the SSL Decryption on Palo Alto Firewall in Next-Generation Firewall Discussions
- Palo Alto Decryption "Out of firewall resources: memory" in General Topics