- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA-VM not recognizing SSL and denying traffic
- LIVEcommunity
- Discussions
- General Topics
- PA-VM not recognizing SSL and denying traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PA-VM not recognizing SSL and denying traffic
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-24-2019 07:42 PM
Hello,
We are implementing SSL Decryption to PA.
Because of this forcepoint agent (that is installed on theworkstation), the return traffic from the Internet (ie: facebook.com, etc) will be denied by the firewall as the SSL certificate has been changed by forcepoint and it is considered untrusted by the firewall.
Do you have any recommendation for this kind of setup?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2019 04:53 AM
Is the forcepoint certificate selfsigned?
you could generate a certificate from the same rootCA as the one you're using for decryption
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2019 09:56 AM
Hello,
Also if you are using Applications to identify traffic, you will need to specify the 'Services/Ports' as well.
i.e.
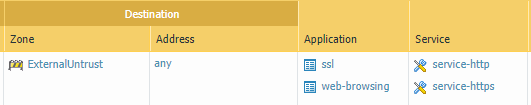
ssl is port 443 and web-browsing is port 80. With ssl decryption enabled, you will now see web-browsing traffic over port 443.
So you now have to adjust some of your policies as follows:
Check the logs and see whay the traffic is getting blocked.
Hope this helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2019 11:42 AM
To make it work, just take the CA certificate that your forcepoint system is using to create the certs for users.
Device tab > Certificate Management > Certificates > Import. Select the forcepoint CA's public key. Once that's done, click the cert name in the UI and click the "Trusted Root CA" checkbox. Hit ok, then commit.
The firewall should trust any future connections from that cert.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-28-2019 06:42 PM - edited 01-28-2019 06:47 PM
Hi @gwesson @OtakarKlier @reaper,
Thank you for the responses. We have been talking to Forcepoint regarding this. IF it is possible then the problem solved.
The issue is whether forcepoint will allow for installation of SSL cert. If that’s not possible what solution do we have?
Another solution is to bypass certain URL from using forcepoint. This is possible from Forcepoint perspective as it allows you to bypass certain URL (using domain name and wildcards).
However, this is not ideal solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2019 10:16 AM
Hello,
What about not ssl decrypting the forcepoint traffic?
Just a thought.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2019 01:31 PM
Hi @OtakarKlier
We implemented SSL decryption to certain URL category. It didn’t work due to the workstation has forcepoint agent.
We tried the same to workstation that has no forcepoint agent and SSL decryption work fine.
If there’s forcepoint agent, forcepoint will intercept the traffic and perform its own encryption and then contact forcepoint cloud service to perform URL Filtering anf malware scanning before passing the traffic to destination.
The return traffic follows the same path.
In summary, firewall could not perform SSL Decryption due to it thought the client didn’t have SSL certificate.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-29-2019 06:43 PM
Hi all,
Closing this thread, as TAC has suggested a workaround for the time being...i.e. disable "block session with untrusted issuers " in decryption profile. FW will not deny the traffic even if we don't trust forcepoint CA and forward certificate to client.
- 3145 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- X-Forwarded-For (XFF) operation query in General Topics
- SSH traffic on one policy appears to be denied by a policy that is currently disabled. How is that even possible? in General Topics
- Whatsapp traffic not recognize by palo alto firewall in General Topics
- Whatsapp traffic cannot recognize in PA for iPhone user. in General Topics
- Issue with user detection on terminal server in General Topics