- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Panorama 8.0.2 Managing PAN-OS 7.1.10 - Aggregate Ethernet AEx has no member interfaces
- LIVEcommunity
- Discussions
- General Topics
- Re: Panorama 8.0.2 Managing PAN-OS 7.1.10 - Aggregate Ethernet AEx has no member interfaces
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 11:31 AM - edited 06-24-2017 11:33 AM
Hi All,
I am currently working with customer, who had an existing Panorama implementation that was upgraded from 7.1.7 to 8.0.2. The reason for the upgrade was due to the certificate expiration, take too place on June 16. The new HA pair I am implementing are running PAN-OS 7.1.10.
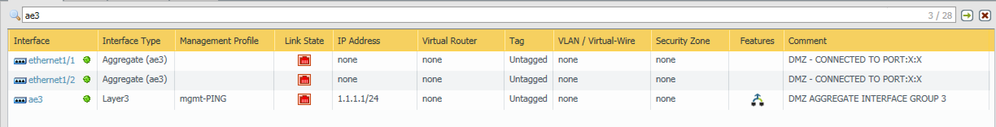
I need to configure an aggregate interface in the HA pair for their DMZ switch. We do not need sub-interface (Tagging) as it will be a direct connection. I did create the AE3, and then added the E1/1 and E1/2 to the AE group. I configured the AE3 as Layer 3 with an IP address as it will be the default gateway for the servers sitting in the DMZ. LACP is also enabled in the aggregate group.
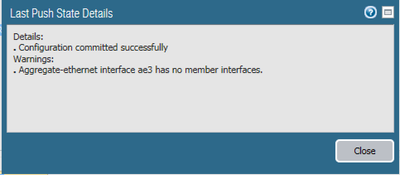
When I push the policy template from Panorama to the HA pair, Panorama returns the following warning: "Aggregate Ethernet AE3 has no member interfaces".
When I log in the Active firewall, and look at the interface list, I can see that the template was applied and the interfaces are associated to AE3.
Does anyone have any idea what the problem may be?
Thank you
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 12:11 PM - edited 06-24-2017 12:39 PM
Hi @acc6d0b3610eec313831f7900fdbd235
Do you see the same warning also locally on the firewall for the commit-all job?
Did you (or another admin accidentially) push the configuration already when you haven't added the interfaces to the AE group, so that this warning is not from rhe newest commit-all?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 12:44 PM - edited 06-24-2017 12:46 PM
Hi @Remo
Thanks for the hints. You are completely right. I was not seen the same error locally, but I did notice some disparaty between the template and the local configuration.
When I tried to push the configuration locally, it pointed some lose sub-interfaces in the VR that did not exist in the template and locally either.
I had to remove them from the VR, as well as from the zone configuration. Also, because the VR and the Zone had been overriden, I had to revert it to Panorama to apply the correct changes.
Because of the above issues, although in the template I had the zone and virtual-router assigned, this part of the configuration was not being pushed to the appliance.
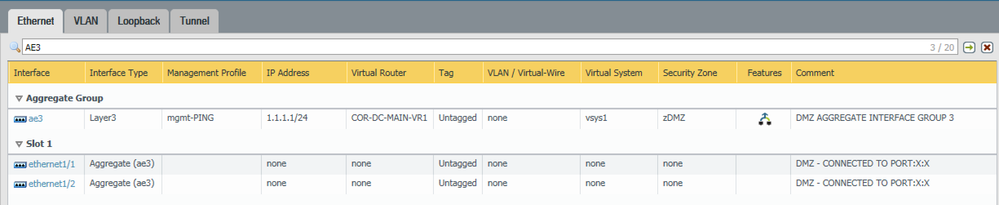
Panorama Template Configuration
PA1 Interface Configuration
I am trying to find out, what happend with the previous option "Force Template Values" that is present on Panorama PAN-OS 7.1.x. I don't see this option in the 8.0.x.
Thank you @Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 01:01 PM - edited 06-24-2017 01:13 PM
Hi @acc6d0b3610eec313831f7900fdbd235
I also noticed this behaviour also with PAN-OS 8.0.2 firewalls, that the panorama push state does not always show the same as locally and I dven had the other situation where I had all good in panorama but some warnings locally.
At least your problem is solved now 😉
Regards,
Remo
PS: The option " Force template values" will be shown when you click "edit selection" in the push/commit-and-push window
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 12:11 PM - edited 06-24-2017 12:39 PM
Hi @acc6d0b3610eec313831f7900fdbd235
Do you see the same warning also locally on the firewall for the commit-all job?
Did you (or another admin accidentially) push the configuration already when you haven't added the interfaces to the AE group, so that this warning is not from rhe newest commit-all?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 12:44 PM - edited 06-24-2017 12:46 PM
Hi @Remo
Thanks for the hints. You are completely right. I was not seen the same error locally, but I did notice some disparaty between the template and the local configuration.
When I tried to push the configuration locally, it pointed some lose sub-interfaces in the VR that did not exist in the template and locally either.
I had to remove them from the VR, as well as from the zone configuration. Also, because the VR and the Zone had been overriden, I had to revert it to Panorama to apply the correct changes.
Because of the above issues, although in the template I had the zone and virtual-router assigned, this part of the configuration was not being pushed to the appliance.
Panorama Template Configuration
PA1 Interface Configuration
I am trying to find out, what happend with the previous option "Force Template Values" that is present on Panorama PAN-OS 7.1.x. I don't see this option in the 8.0.x.
Thank you @Remo
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2017 01:01 PM - edited 06-24-2017 01:13 PM
Hi @acc6d0b3610eec313831f7900fdbd235
I also noticed this behaviour also with PAN-OS 8.0.2 firewalls, that the panorama push state does not always show the same as locally and I dven had the other situation where I had all good in panorama but some warnings locally.
At least your problem is solved now 😉
Regards,
Remo
PS: The option " Force template values" will be shown when you click "edit selection" in the push/commit-and-push window
- 3 accepted solutions
- 3798 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Layer 3 Ethernet Interface vs Layer 3 VLAN interface in General Topics
- Configuring Dual Leased Lines on PA-220 for Efficient Failover in General Topics
- Do I need to deploy a switch between 2xPA firewall (Active-Passive) and 1xJuniper MX router ? in General Topics
- Features column in Network Interface shows an IPSec Gateway in General Topics
- Palo Alto and Microsoft NLB multicast in Next-Generation Firewall Discussions