- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Panorama: how to manage Security/NAT policies
- LIVEcommunity
- Discussions
- General Topics
- Re: Panorama: how to manage Security/NAT policies
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2017 02:43 PM
This is something we're struggling with. How do you write Security Policies and NAT Policies in Panorama when each firewall uses different IPs for NAT and the Security Policies include the IPs in them?
On our FreeBSD firewalls, this was easy. We just used generic variables in our rules scripts such that the rules were the same across all the firewalls, with a separate/unique config file on each firewall that was read into the scripts (to populate the generic variables).
Is everyone just using generic Security Policies that only specify the Source/Destination Zones, the Application, and the Services? How do you push out NAT Policies that are site-specific?
I have not found any way to do this in Panorama. Any pointers to documentation on best practises for this kind of setup would be nice. Having to touch 50 separate firewalls in order to add a new Security Policy is a bit of a pain. 🙂 The few bits of documentation I've found just show how to add policies into Panorama, without listing any best practises or examples.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2017 05:05 PM - edited 05-19-2017 05:05 PM
You can nest device groups.
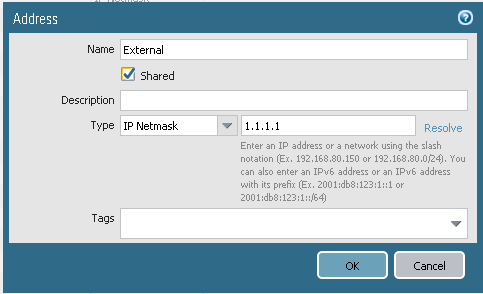
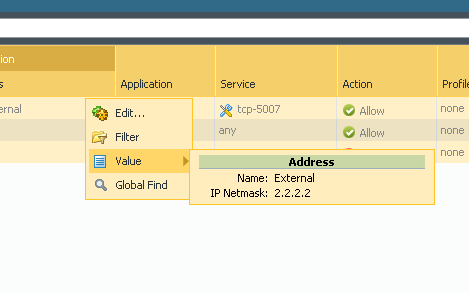
First you create Address object into parent device group.
Then into every firewall device group with correct ip.
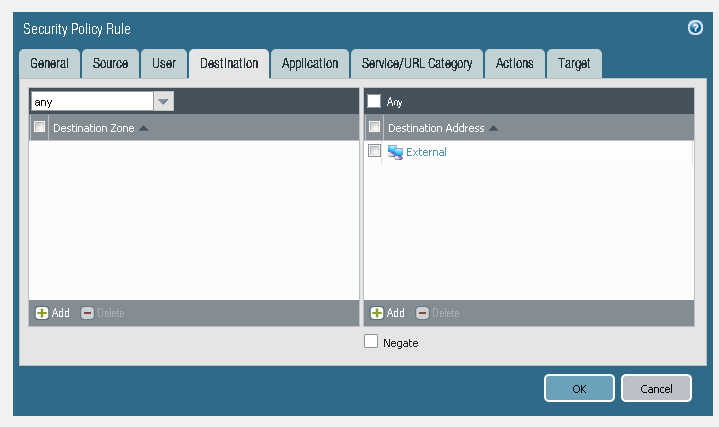
Create rule in parent device group using address object.
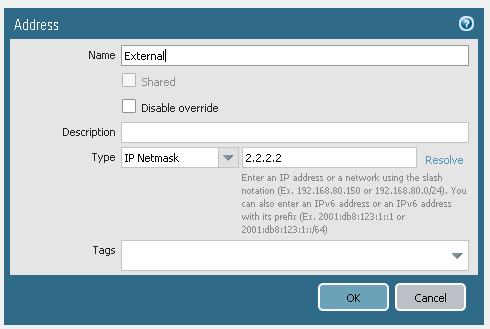
You can move around in hierarcy and verify that child device group is using IP from child device group.
And if you push policy into firewall then it uses correct IP.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2017 05:05 PM - edited 05-19-2017 05:05 PM
You can nest device groups.
First you create Address object into parent device group.
Then into every firewall device group with correct ip.
Create rule in parent device group using address object.
You can move around in hierarcy and verify that child device group is using IP from child device group.
And if you push policy into firewall then it uses correct IP.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2017 11:29 AM
Hrm, interesting. I'll have to play around with that a bit.
Thanks for the tip.
Cheers,
Freddie
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-30-2017 02:01 PM
Okay, so would create a parent Device Group that will hold all of the Security Policies and NAT Policies, and whatnot, using generic Address Object names for things. Use a generic, non-routable IP for the value of the Address Objects. There wouldn't be any firewalls associated with this Device Group.
Then create separate Device Groups for each firewall, nesting them all underneath the parent DG. Recreate each of the Address Objects from the parent DG, assigning the correct IPs for that firewall into the AOs.
Did a couple of test rules using the above, and it appears to work. Will need to play with this some, as this would also require having all the Zone configuration and whatnot configured in the Templates.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2018 07:59 AM
are you talking about "overriding" that address object in the lower device groups, or actually creating another object?
- 1 accepted solution
- 4820 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- NAT mapping public to private IP in General Topics
- Need clarification on URL Filtering logs in Next-Generation Firewall Discussions
- After Endpoint Traffic Policy Enforcement, client can not be access microsoft login portal for smal auth. in GlobalProtect Discussions
- Panorama REST API policy creation error with ' 'message': 'Invalid Body', in Panorama Discussions
- Device Certificate for managed device in Panorama Discussions