- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Reading firewall palo A20 logs
- LIVEcommunity
- Discussions
- General Topics
- Reading firewall palo A20 logs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-22-2019 07:06 AM - edited 05-22-2019 07:08 AM
Hello Paloalto community,
I ask for help please, I collect the logs of a Firewall palo lato A20 with graylog, I find a difficulty in reading Firewall logs. Can anyone help me to explain this logs, I want a clear interpretation of this logs.
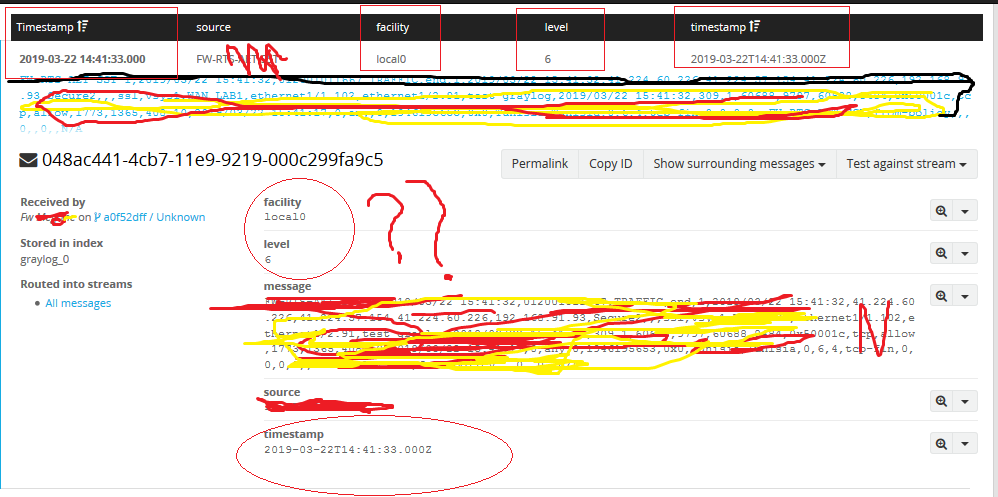
On the web interface of Graylog I see this logs from FW Palo alto:
1/ All the logs of the FW palo are "level6", what does mean "level 6" ?
2/ Facility ( local 0, local 6, user-level) ???
3/ log_subtype, url_category ( any) ? , " session_flags =" 0x1b", " 0x10001c " ", ?
4/ repeat_cout=1 , time generated ???
Please I want a clear interpretation
Thanks ,
AYOUB LABIDI
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 07:41 AM
Afaik lvl6 is informational, facility is configured in the log forwarding profile, subtype is the subtype (url threat traffic wildfire,...) repeat count is the nu ber of tines an identical log was counted in a short timeframe
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 07:41 AM
Afaik lvl6 is informational, facility is configured in the log forwarding profile, subtype is the subtype (url threat traffic wildfire,...) repeat count is the nu ber of tines an identical log was counted in a short timeframe
PANgurus - Strata specialist; config reviews, policy optimization
- 1 accepted solution
- 2389 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- SSL Inspection issues with GlobalProtect users in General Topics
- Sending NFGW (Palo Alto) firewall logs to Cortex XDR. in Custom Signatures
- Fast boot PA-450 in General Topics
- Need clarification on URL Filtering logs in Next-Generation Firewall Discussions
- NIPS in Next-Generation Firewall Discussions