- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Route all traffic through the firewall
- LIVEcommunity
- Discussions
- General Topics
- Route all traffic through the firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Route all traffic through the firewall
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 05:20 AM
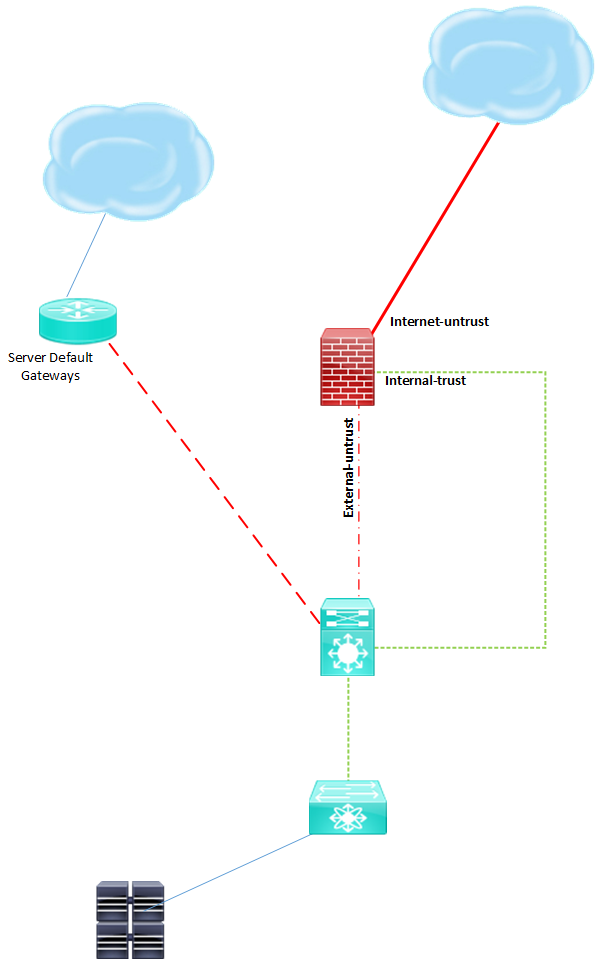
I have one HA pair that sits at the edge of the network running internet traffic outbound. I want to also run all other traffic through this pair as well, but don't want to use it for default gateways for networks. I have done this before, but in one scenario we had edge and core PAs so it made it easier for routing. The other scenario was running vWire and not working about the routing at the PA level.
So I am trying to understand if this is possible. So I want MPLS traffic to come in on the MPLS router (also being the server gateways) and I want the router to have a default route to push ALL traffic to the firewall and come in on the external-untrust interface, then when the traffic gets "in" the firewall I will have static routes or using a routing protocol to know that if it needs to get server resources then go out the internal-trusted interface down to the servers, or if anything else is the destination then go to the internet.
For some reason I don't think what I want to do will work because of routing, or asymetrical routing...I am not sure though. I just dont know how I would run vWire between a router and a switch to achieve this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 08:57 AM
Is the gateway for the servers currently the MPLS router or is it the switch (icon looks like a Nexus 7K)?
What is the current routing between the 7K and the PA?
Do you have another interface available on the MPLS router?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 09:11 AM
The MPLS router is the gateway, the nexus is 5k running Layer 2. Yes there is one more interface on the MPLS router. No routing protcols are running on the PA.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2017 05:14 PM
You can definitely end up with some asymmetry if you're not careful. If all traffic sourced from MPLS destined for a server is pushed through the PA, the return traffic back to MPLS will bypass the PA because the router is the gateway. This will cause problems since the PA won't see the 3-way handshake.
If you want to keep the router as the gateway for the servers, you could use a separate vrf for the MPLS traffic and connect the unused router interface to the PA. Then just send all MPLS traffic to the PA and it will decide where to forward, either to the servers or the internet. I wouldn't use the untrust zone for this MPLS connection, just a different zone.
If you want to avoid sending all the server traffic back through the 5K, you could use subinterfaces on the unused router interface. Each subinterface on the router would be in a different VRF and each subinterface on the PA would be in a different zone.
Is there a reason you don't want the gateway for the servers on the PA? That would simplify things from a routing standpoint.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2017 07:11 PM
Well it has to be a phased approach and eventually the "router on a stick" design is going away and we will run something like 4500x's in the core and move all Gateways there. Then the idea is get Core Firewalls which will make running internal traffic through a firewall easier because then I can use vWire, which is what I have done in the past, I just dont know how you would run vWire between a router and a switch.
VRFs would be the way, I am a ASA guy so I am trying to wrap my head around the PA platform as this is the way we are moving for all firewalls. They just work better and scale better than ASAs do these days when it comes to security. That being said would I need more than a single virtual router? I assume VRs work like VRFs in the R&S world.
I could move all my gatways to the PA, but I rather wait till I get core PAs and run gateways there, rather than the edge firewall if that makes sense. It would only be a temporary fix if I did it now on the edge FW.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-28-2017 01:57 PM
Virtual routers do work like VRFs. But you wouldn't need to run a separate virtual router on the PA. The PA is what's tying together the MPLS connection and the server network so you can have the routes in the same routing table.
Makes sense to keep the gateway on the router for now if you have a redesign coming in the near future.
- 3451 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Help whitelisting a URL that routes through Cloudfront in General Topics
- Should we block HTTP range requests? in Next-Generation Firewall Discussions
- Getting an error while pushing the policy from Panorama to local PA- 3020 firewall in General Topics
- Web Exception in General Topics
- Fast boot PA-450 in General Topics