- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Certificates CA Verisign
- LIVEcommunity
- Discussions
- General Topics
- SSL Certificates CA Verisign
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Certificates CA Verisign
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2014 05:30 AM
Hello,
we have import the CA Certificate from Verisign and want to activate the Antivirus function (policies).
But only the
"Trusted Root CA"
is available in the "Certificate Information"
the option "Forward Trust Certificate" is gray and not available.
But that the function what we need.
We will check upload traffic to the servers in the trust lan of the paloalto
System: PaloAlto 500 v5.0.6
Anyone knows this problem.
Info: when we make a self signed CA we can choose the option "Trusted Root CA".
- Labels:
-
Configuration
-
Networking
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2014 05:56 AM
Hi
Please read last reply by Gwesson from Re: Decryption certificate
and follow this doc https://live.paloaltonetworks.com/docs/DOC-1412
I hope that will explain You enought.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2014 07:46 AM
Hi Netmaster,
Decryption can be done only by self signed Root CA or Sub-ordinate CA. The reason is this certificate signs, another certificate for the traffic.
Lets say you generate a.crt self signed certificate on the firewall. Now traffic comes for bankofamerica.com on firewall. Now a.cert will sign a certificate for bankofamerica.com and forwards it to user.
Only self signed cert and subordinate cert has this capability to sign another certificate.
As long as I know verisign will not provide you subordinate certificate. Let me know if it helps.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2014 11:45 PM
Hi,
thanks for the two answers, thats help to understand how it works in the firewall.
Now we have make a self signed Root CA and a decrypt like this doc:
https://live.paloaltonetworks.com/docs/DOC-1412
but it doesnt work. We want to make Inbound SSL decryption!
The traffic were not decrypted, we don´t see a decrypt flag in the logs of the packets (policies).
And when we make a openssl question from outside to the server we see the ssl cert from the server and not self signed from the firewall.
Config:
shared {
ssl-decrypt {
ssl-exclude-cert;
trusted-root-CA [ int_test_com int_test];
forward-trust-certificate int_test_com;
forward-untrust-certificate int_test_com;
}
int_test_com {
subject-hash fc08871a;
issuer-hash fc08871a;
not-valid-before "Aug 27 14:16:26 2014 GMT";
issuer "/C=DE/ST=Bayern/L=Ismaning/O=test AG/CN=int.test.com";
not-valid-after "Aug 27 14:16:26 2015 GMT";
common-name int.test.com;
expiry-epoch 1440684986;
ca yes;
subject "/C=DE/ST=Bayern/L=Ismaning/O=test AG/CN=int.test.com";
public-key "-----BEGIN CERTIFICATE-----
.....
decryption {
rules {
int_test_antivirus {
category any;
type {
ssl-inbound-inspection int_test_com;
}
from untrust;
to trust;
source any;
destination any;
source-user any;
negate-source no;
negate-destination no;
action decrypt;
from untrust;
to trust;
source any;
destination int_test_com;
source-user any;
category any;
application [ ssl web-browsing];
service [ service-http service-https];
hip-profiles any;
action allow;
log-start yes;
log-end yes;
negate-source no;
negate-destination no;
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2014 07:00 AM
Hi Netmaster,
In Inbound Decryption, you get original certificate of the server, its different than outbound decryption. So, you always get server cert, its expected behavior.
Configuration looks good, can I get same configuration in GUI format.
1. Provide certificat in GUI
2. Provide Decryption policy in GUI
3. Provide Traffic log in GUI, which says its not decrypted.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2014 09:01 AM
Hello,
when we import the server certificate, no CA flag is set and we dont can choose "Forward .... Certificate" and "Trusted Root CA" in the informations.
Thats a Certificate from Verisign. And wehn we load any other public root certficates from Verisign and import this ones, its the same....
For what you need it in GUI Format, its the same informations as about cli.
Anyone a Idee?
best regard
Markus
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2014 09:03 AM
The certificate what we used in the upper config was created in the firewall, i think thats the problem why this one not matched, thats for your info guys.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2014 09:35 AM
Hello Netmaster,
Actually its pretty simple configuration and work for most of the customer.
Most likely this is issue with the Certificate provided by Verisign. Verisign will not provide root certificate, they will provide sub-ordinate certificate. Make sure that sub-ordinate certificate has private key. If certificate matches this condition, you should be able to select "Trust/untrsuted Forward" Parameters.
For Self Signed Cert Follow bellow mentioned two steps. and it will work.
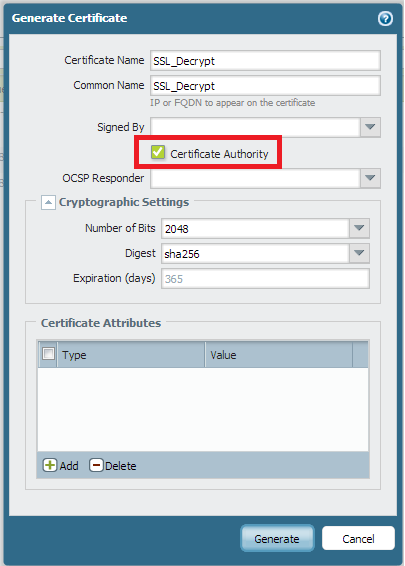
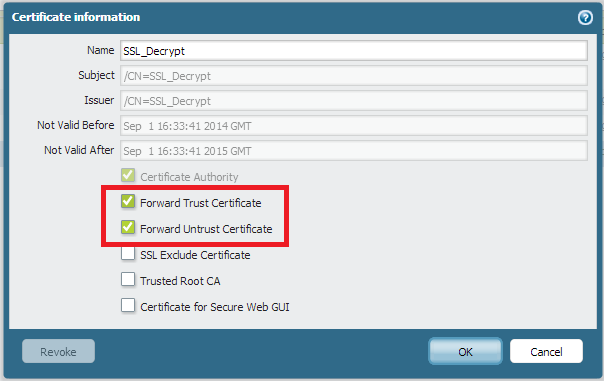
That should work just fine.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2014 09:26 AM
Hi,
now we have made a self signed certificate from the firewall, thats not working.
For the test we have change the Server cert in a self signed too.
We don´ see any encrypted packets. (in the traffic log or in the cli like: How to View SSL Decryption Information from the CLI
We have make all the steps for inbound ssl decrypt from: How to Implement SSL Decryption
but it doesnt works.
Any special thinks what we must do in the decryption and security policies?
Or any other points we must do? enabling decryption on a single tab or so?
Cert:

Policy decry:
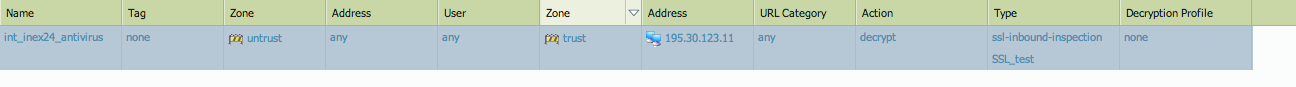
Policy sec:
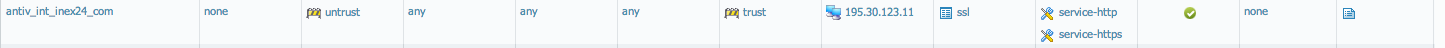
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2014 10:05 AM
Hi Netmaster,
Does server uses certificate SSL_Test?
Most likely answer is NO, thats why inbound SSL decryption is not working.
You are supposed to upload same certificate to firewall which is used by server. If you dont get option for "Forward Trust/Untrust" than its fine.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2014 10:29 AM
Hi,ok i understand we need the same certificate in Firewall as on the server, that we can make on the test Server.But the live Server had the verisign certificate. And we dont can change it. On all certificate we have downloaden From verisign we dont Have the choose to aktivate trust/untrust
On the der.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2014 10:33 AM
Hi Netmaster,
I dont think for inbound encryption you need forward trust/untrust option. All you need is certificate and its private key to upload. Let me know if that helps.
"Forward trust/untrust" is for outbound SSL decryption.
REgards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2014 11:16 AM
Hi,
Sry i think so. In the decryption policy is the last point "ssl inbound" and When we choose it we must choose a certificate. And Here is the Only certificate what we can choose the self signed with the Option
"Forward trust/untrust". Oh er certificate Here Are Not listed
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2014 11:25 AM
Did you uploaded cert with private key ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2014 04:37 AM
Hi,
now we have uploaded whit key and make a policy and it works.
But 1 point, the documentation is here a little bit confuse!
There is the info that you need " forward trust/untrust option" and a CA but for this case is this not the point.
"1. The first thing we would like to do is to install and manage the certificate we would like to use. Navigate Device > Certificates and generate a new self signed Certificate, be sure to activate CA,Forward Trust Certificate, Untrust and Trusted Root CA:"
thanks for your help.
best regards
- 5979 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- How to use a Machine Cert with a Private Key for Global protect prelogon in GlobalProtect Discussions
- Can't install device certificate in General Topics
- Can't import a certificate via XML API using C# in General Topics
- Device Certificate for managed device in Panorama Discussions
- Firewall and Panorama mangement certificate expire in Panorama Discussions



