- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Certificates from enterprise CA
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Certificates from enterprise CA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Certificates from enterprise CA
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2019 08:12 AM
I will admit, certificates are one of my bigest hates.. I just can't get on with them
Firstly we have a microsoft EnterPrise CA. Which I am not overly familiar with anyway ( But I have managed to get the web interface workig on it...)
Idealy what I would love is top be able to generate certificates on the firewall that are trusted by all clients...
But I can start small!
I have followed many BITTY guides to try and pice together some thing that works, but keep getting no good success.
Firstly I would like a certificate that works for the management login page! Tried many thing ( creating a sigingin request, importing the CA [i think] from Microsoft, trying SubordinateCA's ) But nothing works on the login page , and yes I am attaching the service profile in the device config..
Then I need to create decryption certificates, but that's the next step.
Loosing the will to live.
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2019 09:32 AM - edited 06-11-2019 09:33 AM
Hello,
This is the article you will need to follow for the management interface certificate:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClSxCAK
For the SSL decryption, you'll need a Subordinate CA certificate so it can generate certs on the fly.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2019 03:27 AM
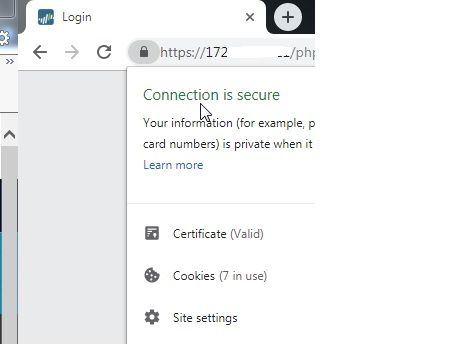
Yes followed those a million times over and could not get a certificate that was trusted by Chrome (Don't use IE as the Palo interface causes it to SWALLOW memory)....
After a bit more digging, looking at the chrome error "ERR_CERT_COMMON_NAME_INVALID" this is actually a bit of a poor eroor message. Chrome aparently looks at the cert for a SAN, supposedly..
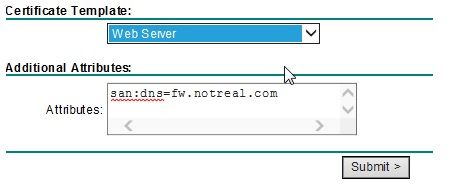
During the PA certificate generation there is no option to populate the SAN attribute.
So, when generating this through the web interface on the Internal CA, you can manualy add the attribute.
After importing that cert and deleting all my unsuccessful previous attemtps from the CA...
Cheers
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-13-2019 01:18 AM
So,
I have no idea how I got this to work yesterday, I did some further work and removed the workign certificate then could not get it to work again????
On inspecting the certificates that were being generated I could see there was no SAN entries??? But no errors were generated.
I tried on the CLI of the CA server, and got the same, certificates were generated with no errors but no SAN 😞
I tried on the CLI of the CA server, but using our old CA to generate the cert, certificates were generated with no errors but and SAN was listed.
Bit of furhter researcha nd discovered that you can enable/disable SAN on certificates..
There are policies for certificate creation and one is ( EDITF_ATTRIBUTESUBJECTALTNAME2 ) for SAN.
It's a registry key but, we can also do this
To view the policy we use...
certutil -getreg policy\EditFlags
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\cumberland-PROD-MSAPP01-CA-1\PolicyModules\CertificateAuthority_MicrosoftDefault.Policy\EditFlags:
EditFlags REG_DWORD = 11014e (1114446)
EDITF_REQUESTEXTENSIONLIST -- 2
EDITF_DISABLEEXTENSIONLIST -- 4
EDITF_ADDOLDKEYUSAGE -- 8
EDITF_BASICCONSTRAINTSCRITICAL -- 40 (64)
EDITF_ENABLEAKIKEYID -- 100 (256)
EDITF_ENABLEDEFAULTSMIME -- 10000 (65536)
EDITF_ENABLECHASECLIENTDC -- 100000 (1048576)
CertUtil: -getreg command completed successfully.
And to update the policy
certutil -setreg policy\EditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
Old Value:
EditFlags REG_DWORD = 11014e (1114446)
EDITF_REQUESTEXTENSIONLIST -- 2
EDITF_DISABLEEXTENSIONLIST -- 4
EDITF_ADDOLDKEYUSAGE -- 8
EDITF_BASICCONSTRAINTSCRITICAL -- 40 (64)
EDITF_ENABLEAKIKEYID -- 100 (256)
EDITF_ENABLEDEFAULTSMIME -- 10000 (65536)
EDITF_ENABLECHASECLIENTDC -- 100000 (1048576)
New Value:
EditFlags REG_DWORD = 15014e (1376590)
EDITF_REQUESTEXTENSIONLIST -- 2
EDITF_DISABLEEXTENSIONLIST -- 4
EDITF_ADDOLDKEYUSAGE -- 8
EDITF_BASICCONSTRAINTSCRITICAL -- 40 (64)
EDITF_ENABLEAKIKEYID -- 100 (256)
EDITF_ENABLEDEFAULTSMIME -- 10000 (65536)
EDITF_ATTRIBUTESUBJECTALTNAME2 -- 40000 (262144)
EDITF_ENABLECHASECLIENTDC -- 100000 (1048576)
CertUtil: -setreg command completed successfully.
The CertSvc service may need to be restarted for changes to take effect.
After restarting CERT Service, SAN creation now works.
I can now create a certificate with SAN names for all our firewalls and that will be accepted by Chrome.
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-13-2019 08:43 AM
Hello,
Nice writeup!
Cheers!
- 6859 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can't install device certificate in General Topics
- Can't import a certificate via XML API using C# in General Topics
- Device Certificate for managed device in Panorama Discussions
- Firewall and Panorama mangement certificate expire in Panorama Discussions
- Alerts and notifications of licenses and certificates soon to expire in AIOps for NGFW Discussions