- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Expired Cert and SSL decryption
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Expired Cert and SSL decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Expired Cert and SSL decryption
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 08:16 AM
We have vendor site which we access.
Recently their SSL cert expired and when I try to access that website chrome shows cert is invalid and still in brower it shows
it is decrypting the website and i can see the PA cert there.
Traffic log shows isession end reason was policy deny?
Why PA shows cert as invalid or non trusted when vendor ssl cert is expired?
How does PA know that vendor ssl cert is expired?
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 11:08 AM
Hi @MP18 ,
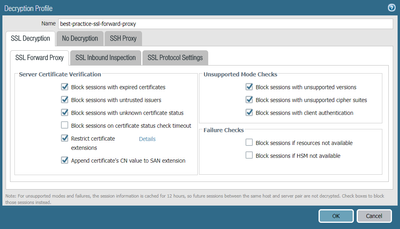
You probably do not block sessions with expired certificates as shown in the image below :
Block sessions with expired certificates—Always check this box to block sessions with servers that have expired certificates and prevent access to potentially insecure sites. If you don’t check this box, users can connect with and transact with potentially malicious sites and see warning messages when they attempt to connect, but the connection is not prevented.
For forward SSL Proxy, the validity date on the Palo Alto Networks firewall generated certificate is taken from the validity date on the real server certificate. (SSL FORWARD PROXY).
Cheers !
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 11:11 AM
The firewall will decrypt all of the traffic regardless of certificate status, but it will utilize the 'Forward untrust Certificate' instead of the 'Forward Trust Certificate'. If it's denying the traffic it means that your decryption profile likely has the 'Block sessions with expired certificates' checked.
Why PA shows cert as invalid or non trusted when vendor ssl cert is expired?
Because if a certificate is expired it is no longer trusted, even though it was issued by a trusted issuer.
How does PA know that vendor ssl cert is expired?
When proxying the connection the firewall reads the certificate of the website to issue a certificate for the site on the fly, so your clients actually trust the connection.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 11:37 AM
For decryption Profile
Block expired certs is unchecked then also my session was blocked
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 11:41 AM
For decryption Profile
Block expired certs is unchecked then also my session was blocked?
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 12:00 PM
Is it actually being blocked and you're getting a firewall block page?
Or are you saying that your browser shows the certificate as expired even though the firewall is decrypting it?
If it's the latter, that is expected. The firewall copies values from the server's certificate to create the decryption certificate. It takes the Subject and the Validity Period values, so if the server's cert or common name/sni are "bad" then the decrypted version will be "bad" as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 12:05 PM
I am saying that my browser shows the certificate as expired even though the firewall is decrypting it-- yes
Traffic log shows session end reason as policy deny
So if traffic log shows policy deny then it is normal behaviour right?
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 12:29 PM
I apologize, I completely missed that in your original post.
No, if you see policy deny, then that session was definitely denied. What is the user experience when this happens? Can the site be browsed as normal if you proceed past the certificate warning? If you can browse normally then the denied session is likely not all that important.
I hate leaving something like that unknown, but it all depends on how much time you want to put into research if the user experience is fine.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 12:46 PM
No user were unable to go beyond the cert warning page.
There was no option to click on proceed further.
During that time i did pcap on PA it shows no drops.
I see fw,tx and re stages.
Anything i should check in pcaps?
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 12:55 PM
There are some debugs, but they can be dangerous to turn on because of the volume of logs it generates (flow basic + proxy basic). I highly recommend opening a case with support to go through the policy and config to see if they can help with a review of your system before diving in to the debugs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 01:08 PM
So one thing you would really want to verify here is if the user is actually getting a firewall block page. If the firewall is generating a block page then I would think that the decryption profile for the decryption policy would actually have the option checked or something is missreading the configuration.
There are some browsers, safari being the most prevelent I get reports for, that simply won't allow a user to bypass the certificate warning regardless of the traffic being decrypted.
I wouldn't expect to see a policy-deny as the session end reason for traffic that has been denied due to the decryption profile, that should end with SER 'decrypt-cert-validation' and the user should get the proper response page from the firewall unless you've disabled it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2019 02:04 PM
No Firewall does not generate any block page.
Users were using the google chrome browser.
Runing PAN OS 8.0.15.
Help the community: Like helpful comments and mark solutions.
- 10489 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Comp certificate expired, how to allow users to log in in GlobalProtect Discussions
- Decryption: Received fatal alert CertificateUnknown from client in Next-Generation Firewall Discussions
- Restrict Microsoft365 tenant in General Topics
- Getting PAN Cert Expires message in Panorama Discussions
- Palo-hosted EDL empty when using certificate profile in Prisma Access Discussions