- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Testing Sinkhole DNS
- LIVEcommunity
- Discussions
- General Topics
- Testing Sinkhole DNS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2018 01:34 AM
Hello, all
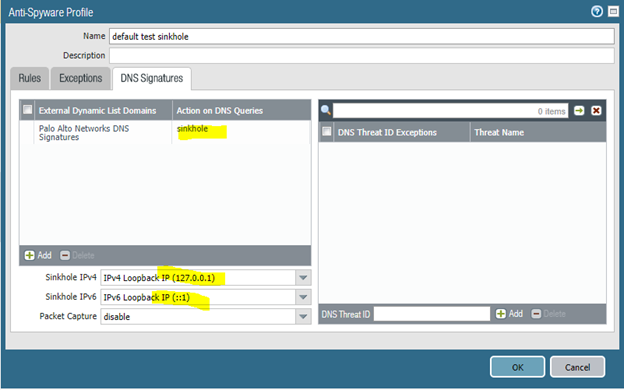
I am testing Anti-Spyware DNS sinkhole. I set:
I make policy with this profile.
For most DNS-names in category “Malware” и “Command and Control” (https://threatvault.paloaltonetworks.com/) i see nslookup answer, for example:
Addresses: ::1
127.0.0.1
And it is good.
But for two DNS-names: namecha.in, 4cdf1kuvlgl5zpb9.pmr.cc (Malware category too) sinkhole is not working and i see ip-adresses in nslookup answer.
What can be wrong? I need advice.
Yes, i can make my own external dynamic list, but why standart not working for malware?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2018 06:52 AM
While namecha.in is present in the PAN-DB URL Classifications it doesn't look like it currently actually has an active DNS Signature in place, which is what the Sinkhole process would trigger on. It was first released in 2732, but it's not showing as being active in a current release. The other domain has the same issue, it isn't showing as having a current active signature.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2018 06:52 AM
While namecha.in is present in the PAN-DB URL Classifications it doesn't look like it currently actually has an active DNS Signature in place, which is what the Sinkhole process would trigger on. It was first released in 2732, but it's not showing as being active in a current release. The other domain has the same issue, it isn't showing as having a current active signature.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2018 09:18 PM
Hello, BPy
It is clear for me now, what PAN-DB URL database is not same as PA DNS Signature database.
Thank you.
- 1 accepted solution
- 2065 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Real Incidents Not Transferring to ServiceNow from Prisma Strata Cloud Manager in Prisma Access Discussions
- B2B VPN IKEv2 Fail with Amazon Private Cloud Peer in General Topics
- NGFW - Panorama registration 3978 : Traffic allowed but RST constantly. in Panorama Discussions
- XSOAR Incident Re Run in Cortex XSOAR Discussions
- XSOAR Multi-Engine Deployment on CentOS7 in Cortex XSOAR Discussions