- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Threat logs
- LIVEcommunity
- Discussions
- General Topics
- Re: Threat logs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2015 11:59 PM
Hi,
Yes it's possible.
You can add a 3rd party syslog server under "Device" -> "Server Profiles" -> "Syslog". Then under "Objects" -> "Log Forwarding" you can specify which profiles you want to send to your syslog-server.
/Staffan
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2015 05:06 AM
Yes I know how to set up log forwarding and am doing it but those are added to the security policies. What I am asking is if you go to monitor\threat can those be monitored
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2015 01:03 PM
Hello,
Currently, the system only allows to see if Monitor Tab was accessed. You can see these events at Monitor->Logs->System.
However, it does not provide information if any sub-options of the tab were used.
Regards,
Val
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2015 07:40 AM
I don't believe that the point of what I am trying to do is being understood. I know how to set up syslogs,but I want to know if there is a way to send the information from the monitor---> logs-->threat can be sent to a syslog to be analyzed. I am trying to do some automation of the process
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2015 08:00 AM
So googol if you choose traffic - any, does that include all the other settings such as threat?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2015 09:05 AM
Are you asking about event correlation? That's done via a SEIM like ArcSight or QRadar. Via a syslog profile you can forward the threat logs to a SEIM which in turn will correlate all relevant logs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2015 09:50 AM
We currently send the information from our syslogs to a seim server to analyze the information but I was asked if we could be more grandular on the type of threat information that is being sent to the seim server from the palot alto
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2015 02:05 PM
Well, setup configuring syslogs in my understanding means not only to configure syslog profile, but also setup log forwarding profile as googol says and configure policies to log forward to your syslog server.
Make sure that you have configured your security policies with Threat Prevention Profiles, DDoS profiles so you can see events in Logs->Threat
After all that configured, you will be able to visualize logs that you configured on syslog server in syslog format. You can use simple Kiwi Syslog to do a quick test.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2015 02:08 PM
Yes it is going to a syslog server and we are using seim to sort and view the logs but I wanted to know if its possible to send more granular or specific threat logs to the syslog servers
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2015 06:55 AM
Could you please explain what do you mean by "more granular"? You will receive threat logs "as is" and in pre-established format. There is no way you can enhance them. Your SIEM can apply correlations and alerts, but they will be based only on the information received from PA.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2015 07:06 AM
My boss asked me if it was possible to apply a filter to the threat logs before they are sent to the syslog just like you can add a filter when you are in monitor--->logs--->threat.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2015 09:33 AM
In the 'Log Forwarding" profile that googol included a screen shot of you can elect which threats you wanted to send to your SEIM/Syslog.
Further within the SEIM you can use REGEX to parse the fields and filter exactly the records you're looking for.
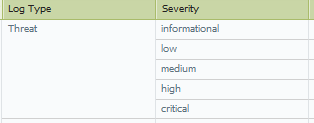
For instance a "Threat" log with a threat type of "virus" of a "medium" severity can be filtered to either be included or excluded in your SEIM:
2015/07/21 09:49:53,*DEVICE SN*,THREAT,virus,*A BUNCH OF STUFF SEPARATED BY ALPHA NUMERIC CHARACTERS SEPARATED BY COMMAS* ,Virus/Win32.ramnit.aztfn(2022885),any,medium,server-to-client,*MORE STUFF FOLLOWS*
Here was a log example from our SEIM. You'd have to use REGEX to parse through the log message to the relevant fields but you could filter to the log types you're wanting this way as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2015 02:19 PM
As Brandon replied, it is best way to apply filtering on SIEM side. There is no way you can filter it on PA level, the only thing you can do is just select certain severity level to be sent to SIEM. But in that case you are not filtering - you simply not sending these logs to SIEM.
What SIEM do you use? Splunk to be proven good, I tried the others commercials and free - Splunk still best for PA.
- 6337 Views
- 21 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- CVE-2024-3400 Unit42 Threat Brief / Private Data Reset in Threat & Vulnerability Discussions
- SSL Inspection issues with GlobalProtect users in General Topics
- Tons of receptivity.io in Cortex XDR Discussions
- NGFW - Panorama registration 3978 : Traffic allowed but RST constantly. in Panorama Discussions
- Sending NFGW (Palo Alto) firewall logs to Cortex XDR. in Custom Signatures