- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
VPN s2s with Juniper ScreenOS with multiple networks on PA side
- LIVEcommunity
- Discussions
- General Topics
- Re: VPN s2s with Juniper ScreenOS with multiple networks on PA side
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2015 01:17 AM
Hello
I have to connect by ipsec vpn PA200 PANOS6.1.6 with NS5GT 6.2.0r15 ScreenOS.
Problem that I have is that clients behind NS must have access to two LANs on PA and to internet throuth tunnel.
LAN_A———
LAN_B——— PaloAlto……….tunel_IPSec………………Netscreen———LAN_M
Internet ——
How to do it?
At the moment I have working config like https://www.corelan.be/index.php/2007/11/17/juniper-setting-up-an-ipsec-vpn-tunnel-between-a-juniper...
but I really don't know how to set up tunnel for internet traffic - how to setup "VPN>AutoKey IKE ".
As I remember on this forum are ScreenOS experts so I ask You for help.
Regards
SLawek
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2015 01:38 AM
The settings are the same as for any VPN. The only diference are proxy IDs On PA side: local 0.0.0.0/0, remote LAN_M and vice versa on Juniper
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2015 11:21 AM
Hi,
If you followed the configuration in the link you already setup a route based VPN on the screenos side. The next step would be:
-Delete proxy-IDs on both sides (PA and screenos) and check that you can still reach the LAN through the VPN.
And on the screenos side.
-Create a static route to the PA public ip address,
-Replace your current default gateway and disable any possible DIP, do this on a maintenance window as you can lost management. If you're using the public IP interface you also need to create a route like te previous one to manage it.
On the PA side,
-Create a dynamicIP/port NAT policy for the network on the branch office and the security policy, this will allow the internet conection.
regards,
Gerardo.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2015 01:38 AM
The settings are the same as for any VPN. The only diference are proxy IDs On PA side: local 0.0.0.0/0, remote LAN_M and vice versa on Juniper
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2015 03:09 AM
Hi Santonic
I did as You wrote and tunnel is working for LANs, now problem is with internet access only.
Now my routing table looks like:
IPv4 Dest-Routes for <trust-vr> (7 entries)
--------------------------------------------------------------------------------------
ID IP-Prefix Interface Gateway P Pref Mtr Vsys
--------------------------------------------------------------------------------------
* 3 0.0.0.0/0 untrust x.y.z.129 C 0 1 Root
* 5 192.168.5.1/32 trust 0.0.0.0 H 0 0 Root
* 4 192.168.5.0/24 trust 0.0.0.0 C 0 0 Root
* 1 x.y.z.128/26 untrust 0.0.0.0 C 0 0 Root
* 6 192.168.1.0/24 tun.1 0.0.0.0 S 20 1 Root
* 7 192.168.50.0/24 tun.1 0.0.0.0 S 20 1 Root
* 2 x.y.z.158/32 untrust 0.0.0.0 H 0 0 Root
x.y.z.129 is a default gateway for NS device.
My untrust interface of NS is in route mode.
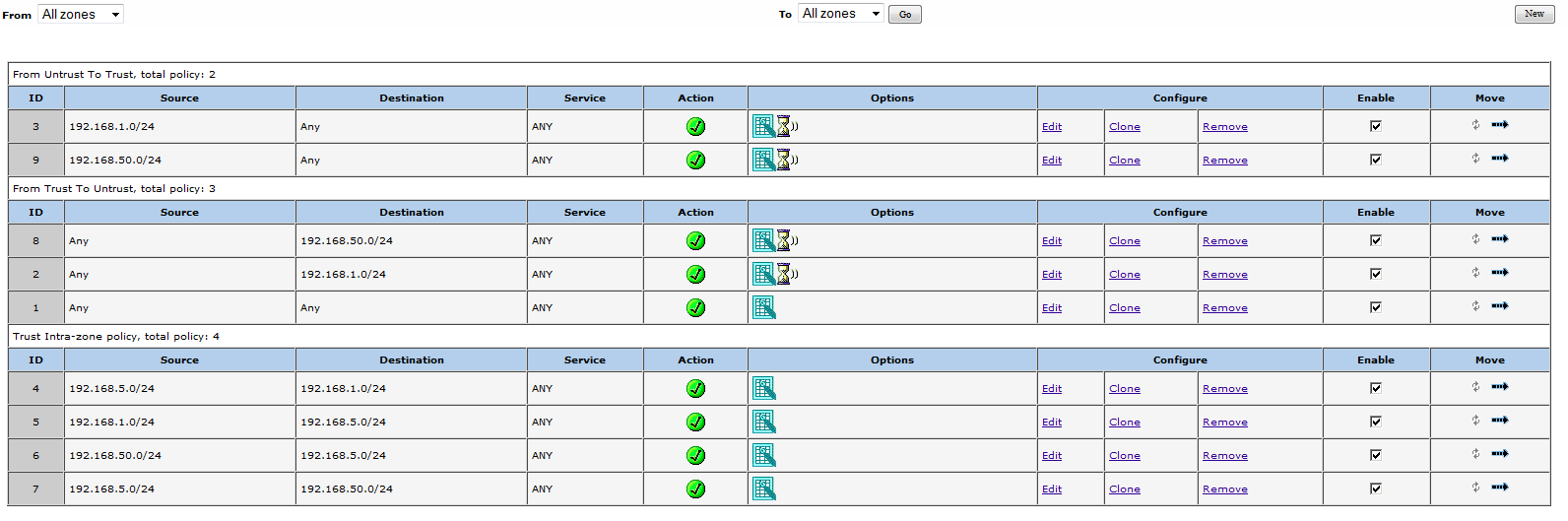
My security policies loks like:
Are they policy nessesary? How do I change it according to proxy_id change?
Help me please
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2015 11:21 AM
Hi,
If you followed the configuration in the link you already setup a route based VPN on the screenos side. The next step would be:
-Delete proxy-IDs on both sides (PA and screenos) and check that you can still reach the LAN through the VPN.
And on the screenos side.
-Create a static route to the PA public ip address,
-Replace your current default gateway and disable any possible DIP, do this on a maintenance window as you can lost management. If you're using the public IP interface you also need to create a route like te previous one to manage it.
On the PA side,
-Create a dynamicIP/port NAT policy for the network on the branch office and the security policy, this will allow the internet conection.
regards,
Gerardo.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-14-2015 01:43 AM
Hi Glastra
I cretaed static source route from LAN of Netscreen device and internet traffic started working.
Thank You for all of You for Your help.
Regards
SLawek
- 2 accepted solutions
- 3137 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- How does Expanse know about my website? in General Topics
- AWS Reference Architecture, Subnet Sizes and Automation in VM-Series in the Public Cloud
- error: azure marketplace vm-series do not bootstrap in VM-Series in the Public Cloud
- Multiple Static Route(s) for PA-VM in Azure in VM-Series in the Public Cloud
- Excessively long useragent in General Topics