- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
VPN to Azure dropouts
- LIVEcommunity
- Discussions
- General Topics
- Re: VPN to Azure dropouts
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
VPN to Azure dropouts
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2016 04:24 PM
I have searched high and low for this and found a few articles regarding IKE configuration and nothing seems to fix it.
PAN 3020 v7.0.5. IKE 2 VPN to Azure. The VPN works but around every 50 mintues the tunnel drops out for a few minutes then re-establishes. I have tried various different IKE and IPsec settings as per advice from Palo Alto articles, Microsoft Azure articles and settings from a comment against a Palo Alto article that the commentor said worked. No joy.
From the Azure console there is no way of checking IPsec ettings.
Any help would be good.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2016 06:41 AM
Hi,
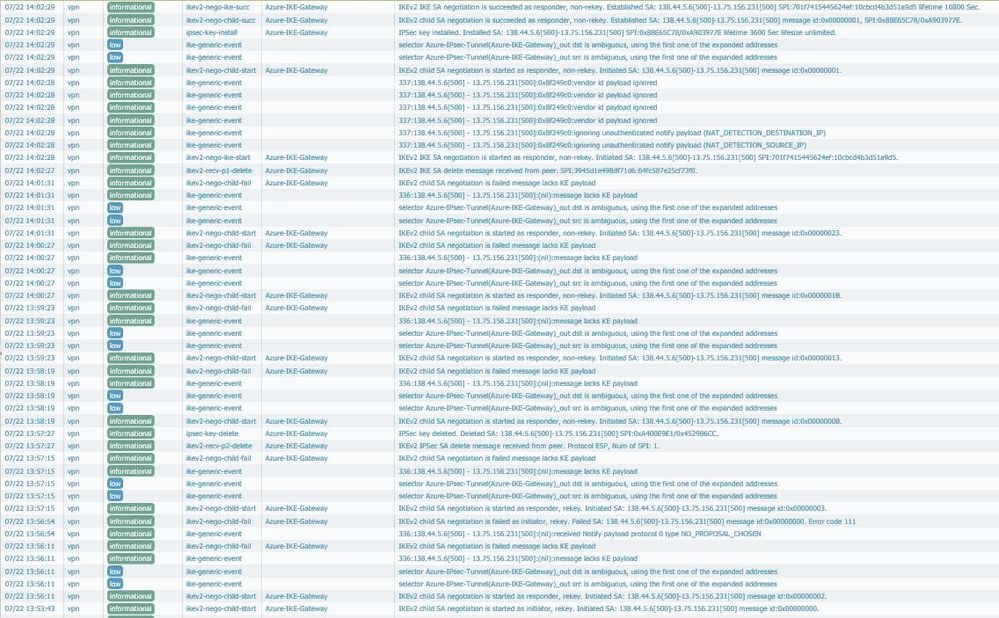
Just had a similar issue. Can you post your VPN settings so I can compare with my and tell you what I have changed to make it working? Please send a screenshot of the logs from the Monitoring tab> System. Both successful and unsuccessful.
Cheers
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2016 11:06 AM - edited 07-21-2016 02:40 PM
Hi,
Just a quick update/tips on this:
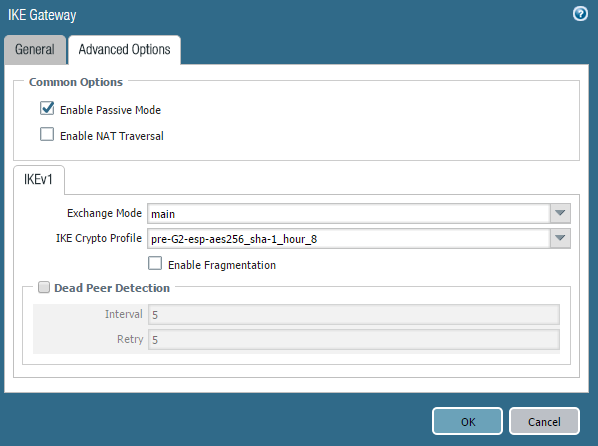
- make sure Palo in the "passive" mode. So it will not be able to initiate a VPN but we could not make it working when its disabled.
- IKEv2 initiate 2 tunnels: IKE tunnel ( old name of IKEv1 Phase 1) and CHILD_SA (old name of IKEv1 Phace 2). Default lifetime for IKE Tunnel is 86400 or 28800 seconds (depends of the vendor) for CHILD_SA is 3600 seconds hence your tunnel will be always re-established every hour. But it takes couple seconds not minutes.
- disable no-pfs on IPSec Crypto
- disable "Liveness Check" on the IKE Gateway configuration.
Make sure that all other setting are compatible with Azure. Please see below:
IPsec Parameters
Although the values listed below are supported by the Azure VPN Gateway, currently there is no way for you to specify or select a specific combination from the Azure VPN Gateway. You must specify any constraints from the on-premises VPN device. In addition, you must clamp MSS at 1350.
IKE Phase 1 setup
| Property | Policy-based | Route-based and Standard or High Performance VPN gateway |
| IKE Version | IKEv1 | IKEv2 |
| Diffie-Hellman Group | Group 2 (1024 bit) | Group 2 (1024 bit) |
| Authentication Method | Pre-Shared Key | Pre-Shared Key |
| Encryption Algorithms | AES256 AES128 3DES | AES256 3DES |
| Hashing Algorithm | SHA1(SHA128) | SHA1(SHA128), SHA2(SHA256) |
| Phase 1 Security Association (SA) Lifetime (Time) | 28,800 seconds | 10,800 seconds |
IKE Phase 2 setup
| Property | Policy-based | Route-based and Standard or High Performance VPN gateway |
| IKE Version | IKEv1 | IKEv2 |
| Hashing Algorithm | SHA1(SHA128) | SHA1(SHA128) |
| Phase 2 Security Association (SA) Lifetime (Time) | 3,600 seconds | 3,600 seconds |
| Phase 2 Security Association (SA) Lifetime (Throughput) | 102,400,000 KB | - |
| IPsec SA Encryption & Authentication Offers (in the order of preference) | 1. ESP-AES256 2. ESP-AES128 3. ESP-3DES 4. N/A | See Route-based Gateway IPsec Security Association (SA) Offers(below) |
| Perfect Forward Secrecy (PFS) | No | Yes (DH Group1, 2, 5, 14, 24) |
| Dead Peer Detection | Not supported | Supported |
After doing all this tunnel still stable for the past 3 days.
You can clear the tunnel couple times to see if everything is working correctly:
> clear vpn ike-sa gateway (for IKE Tunnel)
> clear vpn ipsec-sa tunnel (for CHILD_SA)
Hope it helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2016 11:48 PM - edited 07-22-2016 03:57 AM
Hi,
The first thing I have noticed that you Palo device not in the "Passive" mode. Try to configure/modify config using my settings and get back, please.
All the best
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2016 03:17 PM
I noticed that first log entry myself as the PAN tries to start the SA negotiation as intitator but it is definitely in passive mode.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2016 11:59 PM
Did you commit the changes?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 02:47 PM
It has been passive for quite a while now having commited multiple changes over the last few weeks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 03:51 PM
Very strange. What are the latest logs suggests? Did you try my suggestions? Our VPN still stable, fingers crossed 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 03:54 PM
Can you take some screenshots of your config and I will match that and see how it goes? I can't find much info on the log entires except what you have already suggested.
If I match what you have it might improve.
Thanks for your input.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 04:09 PM
Sorry don't have a direct access to the box but my config listed below:
IKEv2
Diffie-Hellman Group Group 2
Authentication Method SHA1
Encryption Algorithms AES256, 3DES
Phase 1 Security Association (SA) Lifetime (Time) 28,800 seconds
CHILD_SA
Encryption Algorithms AES128, 3DES
Authentication Method SHA1
Phase 2 Security Association (SA) Lifetime (Time) 3,600 seconds
Perfect Forward Secrecy (PFS) no-pfs
Cheers
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 05:28 PM
It is just passed the 1 hour mark, since making changes to match yours, where we were dropping packets before and the tunnel has stayed up. The negotiation seemed to run smoothly.
Fingers crossed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 08:57 PM
It looks as though it is dropping 4 or 5 packets every hour or so.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2016 11:47 PM
I am not sure but it could be because of the tunnel rekeying. But l don't know if 4-5packets acceptable or not
- 19457 Views
- 35 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Upgrading 10.1.11-h5 to 11.1.2 directly ? in Panorama Discussions
- After Endpoint Traffic Policy Enforcement, client can not be access microsoft login portal for smal auth. in GlobalProtect Discussions
- [HELP] How to setup Azure Monitor/Insight for PA-VM on Azure Cloud to monitor CPU/Memory Metrics? in VM-Series in the Public Cloud
- SSO and MFA for Admin Access Only in Next-Generation Firewall Discussions
- Azure Palo VM IPSec Tunnel to another Azure Palo VM in VM-Series in the Public Cloud