- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
What is the correct way to send all traffic to the virtual firewall?
- LIVEcommunity
- Discussions
- General Topics
- Re: What is the correct way to send all traffic to the virtual firewall?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2017 07:33 AM
Hello, good morning,
I plan to purchase the product vm100 (kvm), to have a virtualized firewall on a dedicated server.
In the same rack will have other servers connected to a switch.
I wonder, what would be the right way to pass all incoming and outgoing traffic from the other servers through the firewall.
Thank you very much for advising me on good practices.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2017 03:09 AM
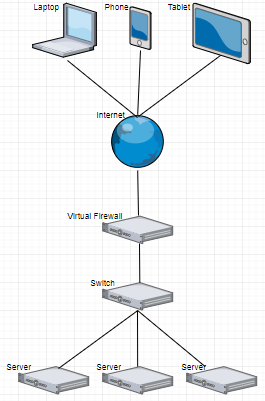
as per the diagram, your network setup is quite simple. You just need to have the servers and the firewall's internal interface on the same subnet and configure the firewall as the default gateway for the servers.
On the outside interface configure the public IP your isp have provided.
Create a security/nat policy from inside to outside for outbound. Similarly, for inbound traffic, you will have to setup port forwarding/DNAT rules and security rule to allow traffic to hit the servers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2017 09:00 AM
I am assuming that currently, you have a router which takes of your incoming and outgoing traffic for the servers. If this is true then make firewall as the default gateway for the servers and then connect the firewall to router over a different interface.
Setup nat and security policies accordingly.
If you can share your current network diagram, then I should be able to suggest further.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2017 02:26 AM
Hi, thanks for the answer. Sorry for not being able to attend the publication sooner.
I will publish the basic diagram that will better explain the model of the connections than I do with text. Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2017 03:09 AM
as per the diagram, your network setup is quite simple. You just need to have the servers and the firewall's internal interface on the same subnet and configure the firewall as the default gateway for the servers.
On the outside interface configure the public IP your isp have provided.
Create a security/nat policy from inside to outside for outbound. Similarly, for inbound traffic, you will have to setup port forwarding/DNAT rules and security rule to allow traffic to hit the servers.
- 1 accepted solution
- 2867 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- SSL Inspection issues with GlobalProtect users in General Topics
- B2B VPN IKEv2 Fail with Amazon Private Cloud Peer in General Topics
- Help understanding Asymmetric Path issue in General Topics
- Basic Palo Alto configuration Help in General Topics
- Need clarification on URL Filtering logs in Next-Generation Firewall Discussions