- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
What ports are needed for site to site IPsec tunnels to work?
- LIVEcommunity
- Discussions
- General Topics
- Re: What ports are needed for site to site IPsec tunnels to work?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 11:21 AM
We have 2 palo alot firewalls & we are trying to establish a ipsec tunnel between both. We proved that all vpn configurations are correct and were able to establish the tunnel & pass traffic but only if we add a firewall rule saying allow any/any/any/any at the very top of the rule base, which goes against our security requirements. Once we deleted the firewall rule the tunnels stopped working. Simply put, we need to open firewall rules for site to site tunnels to work in our environment. Does anyone know the Palo Alto TCP/UDP ports to open in order for phase 1 & 2 to go green?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 11:48 AM
IPSec - UDP 500
IPSec over NAT - UDP 4500
GlobalProtect - TCP 443 and UDP 4501
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 11:48 AM
IPSec - UDP 500
IPSec over NAT - UDP 4500
GlobalProtect - TCP 443 and UDP 4501
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 11:51 AM
Thanks! Which zones do these ports need to be opened on?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 02:01 PM
Hello,
The one from the internet, ie untrust.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 08:40 PM
Usually vpn is terminated on UNTRUST interface.
Unless you have added "block any" rule to the end this traffic is permitted already by "interzone-default" policy.
If you terminate vpn on on some other interface (TRUST, LOOPBACK etc) and have NAT in place then you need to adjust your security policy accordingly.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 01:15 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 06:29 AM - edited 03-15-2019 06:31 AM
Hi I think I had typo in my answer about interzone. If traffic stays in same zone it is intrazone.
Basically rules are evaluated top to down.
First one that matches will take effect. Either allows or blocks and based on security profile will check for viruses or not (only allow rules).
If no rule matches then one of last 2 will match.
intrazone-default will match if traffic source and destination is in same zone. For example if traffic from vpn peer will come from internet and you have configured IPSec gateway on WAN interface then this rule will match.
If traffic (based on NAT and virtual router) is destined to some other zone then "interzone-default" will match.
Those default rules will not log by default so you don't see any traffic that matches those rules.
To gain this visibility you have to click on the rule and choose "override".
Click on the rule name.
On "Actions" tab check "Log at session end".
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2019 01:05 AM
Hi! I suggest install and setting VeePN and servers.
This vpn differs from other vpn providers:
1) Besides vpn you are provided with fully working vps
a) Personalized configurations for your vpn
b) Regulated logs
c) Generating your own services, such as http
d) There is no 3rd silent persons, after setting up you are going to be the only owner
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2020 05:55 PM
Hi,
I am currently encountering an issue, UDP 500 and 4500 are not enough to get site to site vpn tunnel up and running. Is that esp also required to be allowed?
THanks
Best Regards,
Elroy
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-08-2020 06:47 AM
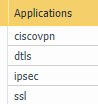
Hello,
I went beyond ports and use the L7 Applications. Including the screen shot below. I also allow ping as some devices send ping to monitor tunnel status.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2020 05:35 PM
Hi,
Thanks for your reply. Does that mean UDP 500 and 4500 are not enough and esp is also required? THanks
Best Regards,
Elroy
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2020 10:10 PM
ideally if you have allowed ports , then it should work . for better security/clarity , instead of using service ports , you can use ipsec related applications as mentioned in earlier post .
Now , if it is still not working , then i would suggest you to check logs and see what exactly is getting denied and then allow it by ports OR application.
NOTE :- allow logging in default policies to see deny logs if it is hitting those policies
Hope it gives you a direction
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2020 10:14 PM
Thank you so much for your response. In my scenario, I am considering if it is blocking by the intermediate network devices which is mainly port-based. So I have limited visibility on those devices. But thanks again and it gives some insights as well.
Best Regards,
Elroy
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2020 10:18 PM
you should not see any logs in your firewall if some intermediate device is blocking it and that way it can be confirmed.
Or if you want to dig in further , just apply packet capture with both ends public ip in filter.
Cheers
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2020 10:58 PM
I have performed a packet capture and see that traffic is encap and no decap is sending back and most likely is using esp. My question is that ipsec should be using udp 500 and 4500 from documents. if I should enable esp as well
Thanks
Best Regards,
Elroy
- 1 accepted solution
- 31323 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure Palo VM IPSec Tunnel to another Azure Palo VM in VM-Series in the Public Cloud
- Firewall has the IPSec tunnel but Panorama don't. How to fix? in Panorama Discussions
- IPSEC Tunnel monitor for policy based site to site VPN in Next-Generation Firewall Discussions
- IPsec tunnel PA-Forcepoint Up but no traffic passing through in Next-Generation Firewall Discussions
- Should I override the intrazone-default to deny? in Next-Generation Firewall Discussions