- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Wildfire - Time required to block known malware
- LIVEcommunity
- Discussions
- General Topics
- Re: Wildfire - Time required to block known malware
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Wildfire - Time required to block known malware
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2013 09:24 AM
Using the 'free' Wildfire service, does anyone know how long should I expect the delay to be before downloads marked as malware are blocked subsequently?
For example, today we had a download ("pdf_delta_ticket.scr" below) that was logged as upload-skip which to my knowledge means that it has been seen before by this device. As the last previous upload-success was ~6 days previously (and as it was a DLL it almost certainly wasn't the original download) this seems to suggest that the time taken is more than a few days (we download and install AV updates daily).
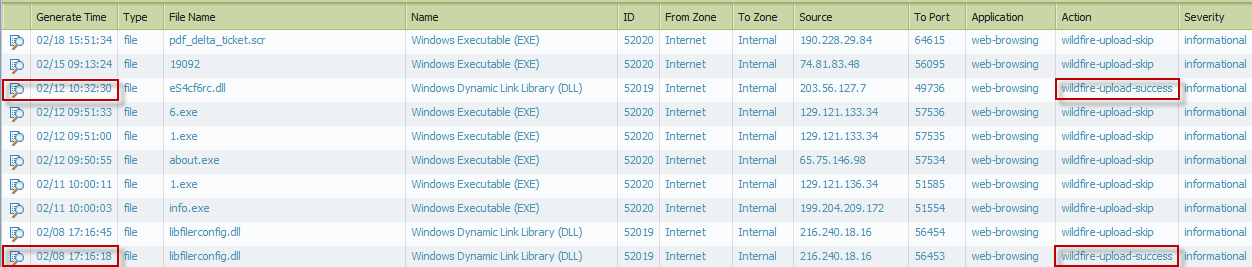
Rgds
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2013 09:44 AM
Whenever a new file is sent to wildfire it is analyzed for various malicious behaviors. You can login to your wildfire portal to check the status of your files i.e only if it is found to be malicious an av signature is created and released. So have you had a chance to look at your wildfire portal @ https://wildfire.paloaltonetworks.com/Wildfire .
Also refer the following documents:-
Thanks,
Subijith Raghunandan.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2013 09:56 AM
Yes - I've checked the portal and it is VERY malicious (turning off IE phishing protection, disabling the firewall etc)!
While I understand that some malware is polymorphic and will change it's binary fingerprint, the fact that this was a skipped upload means that it must have been seen before in it's current "guise" and I can only assume that it would have looked just as malicious previously (I can;t see why not).
As we haven't had a upload for 4 days (and the most likely EXE upload was at least 12 days ago) that seems to suggest that no AV signature has been released in the previous 2 weeks that should have triggered on the re-download (or the signature released failed to match it properly?).
Rgds
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2013 10:09 AM
However - having checked the flowchart in the referenced documents (thanks) I note that the hash check is actually performed in the Palo cloud, not on the PA device - so I guess this means that it is not dependent on the previous upload from our network.
Rgds
- 2223 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cortex XDR flagged malicious macros in Cortex XDR Discussions
- Prisma Cloud Wildfire Runtime protection on hosts in Prisma Access Cloud Management Discussions
- Cortex XDR agent and EICAR malware test file in Cortex XDR Discussions
- Advanced Wildfire Allowing High Severity Verdicts but blocking Informational in Next-Generation Firewall Discussions
- Wildfire Malware Alert in Cortex XDR Discussions



