- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
X-forwarded-for not showing results
- LIVEcommunity
- Discussions
- General Topics
- X-forwarded-for not showing results
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2018 09:29 AM - edited 06-05-2018 09:37 AM
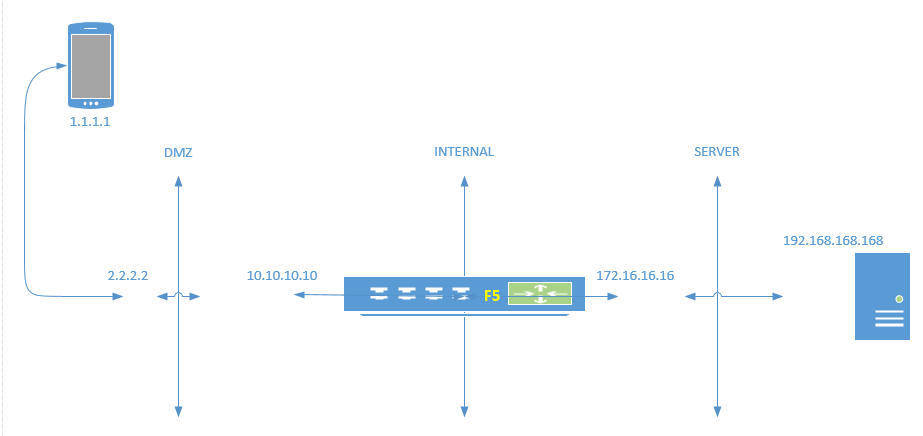
We use F5 with its VIP interfaces in DMZ and is doing SSL offloading (presents a cert on the webserver's behalf allowing plain text traffic to be inspected). As in below example, external source(1.1.1.1) acesses 2.2.2.2(PA NATS to 10.10.10.10 of the F5 VIP). F5 then does SSL offload and SNAT for communication with server, but the source interface for this SNAT that it uses resides in INTERNAL network. F5 uses 172.16.16.16 as source to contact to 192.168.168.168.
With this setup when F5 (172.16.16.16) communicates with server it is in plain text and firewall is able to do inspection and drop traffic. But then for it F5 becomess the culprit while actually it is 2.2.2.2. There is no way to correlate both sides of communication and our management is not inclined towards using SSL decryption. F5 is able to insert external source IP(2.2.2.2) in to the header X-Forwarded-For. Can PA pull this information in logs. If this option "Use X-Forwarded-For Header in User-ID" is for what i am asking, I have it enabled on the firewall and all i see are our AD users and no external/internal IP in the source user field. And this webserver is heavily used from outside. Is there any other setting that i need to configure. I have it enabled on the URL profile also. Does that mean it shows results in URL logs only.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2018 01:48 PM
I'm not sure that really fixes the issue though does it? The logs will still record the F5 as the source address for outside sources and you wouldn't map outside sources to user-id.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2018 10:49 AM
That option would only work if you were trying to generate user-id logs via something like a captive portal on forwarded traffic. SInce the firewall sees the source as the F5 VIP that's the interface that it's going to view as the source of any threat that it identifies.
I'm not sure how you would address this if management is against doing the decryption on the Palo.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2018 01:37 PM - edited 06-05-2018 01:59 PM
Starting with PAN-OS 8.0, you can use the XFF header for URL Filtering logs as well as for general use with security policies by mapping the XFF IP with a user name. You will need User-ID configured for that mapping to work:
@BPry pointed out that these are external clients rather than users managed by the firewall. I missed that these are external addresses. There wouldn't be a way to map the external addresses to user names in that scenario.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2018 01:48 PM
I'm not sure that really fixes the issue though does it? The logs will still record the F5 as the source address for outside sources and you wouldn't map outside sources to user-id.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2018 12:24 PM
I had it enabled, addresses are now showing under XFF column in URL filtering logs, source address is still the F5. I also had alerting diabled on few URL categories which was not showing the results.
- 1 accepted solution
- 3526 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Fast boot PA-450 in General Topics
- Intermittent inet connectivity after updating to 10.2.8-h3 in Next-Generation Firewall Discussions
- best practice assessment option is not showing in paloalto customer portal in General Topics
- Setup > Management > Cortex Data Lake > Cortex Data Lake Status > Show Status in AIOps for NGFW Discussions
- 403 forbidden error while importing IDP fiile in General Topics