- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
dmz design
- LIVEcommunity
- Discussions
- General Topics
- Re: dmz design
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 01:45 PM
Hi,
What is the benefit of having DMZ setup with two firewalls.
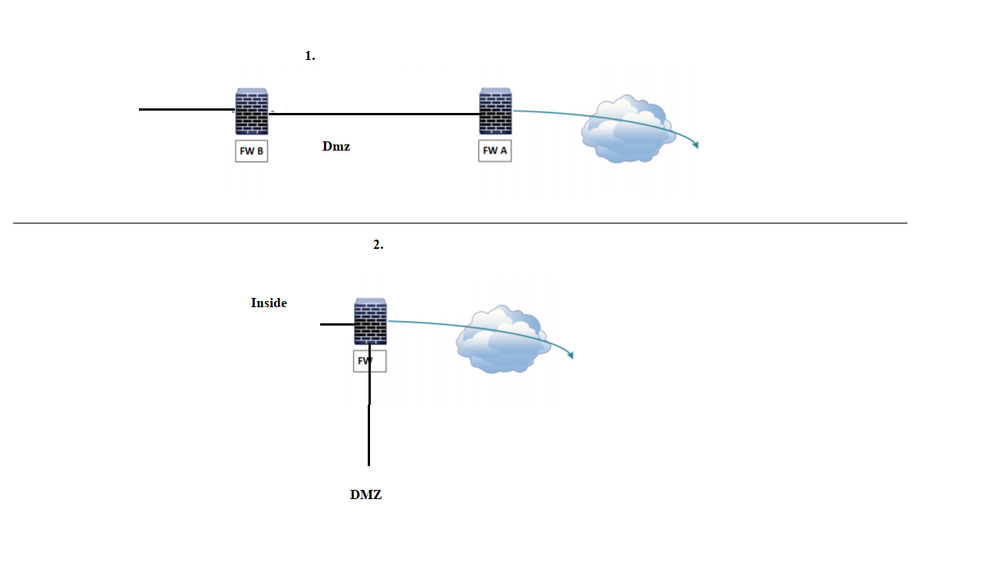
If we have dmz setup with two firewalls ( I don't know this design is valid and adopted design, I found it in the net )
If this is a valid design ,From local lan how the traffic flow to outside (10.0.10.0/24 to internet ) and outside the local lan 10.0.10.0/24
Thanks
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2018 02:14 AM
thats almost impossible to answer as all network designs, security levels and ammounts of data requests are different.
for simplicity and cost Pic 1 is the obvious choice.
both designs perform exactly the same task of creating a DMZ.
it all depends on the network design, ammounts of data requests etc..
i could not even suggest a level requirement as you could have 2 servers offering mega data or 100 servers not doing much at all....
nowadays data links and firewall processers are exceptional compared to previous decades so it all depends on your requirements and network designs.
Mick.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 02:44 PM
Hello,
One thing is the amount of load on the firewall. With two youre splitting some of the traiffc off and the outer on is taking the brunt of the external attacks. In the modern world with next gen firewalls that are sized appropriatly, either design will work. I dont see a problem with the collapsed DMZ model, e.g. one firewall with dmz branched off.
As long as they are configured correctly :).
Just my thoughts,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2018 03:54 AM
Hi,
Thanks for the reply . If I need to design DMZ with two fw , could you please give an sample toplogy and the data flow
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2018 05:44 AM
Thats a bit difficult as it depends on what you are using the dmz for and what type of services are contained within it.
in a basic setup traffic from outside is only allowed access to the dmz. More modern designs use the dmz for such devices as reverse proxies, ftp servers, rds and vdi dateways etc...
if you are twin firewalling for added intrusion prevention as @OtakarKlier suggested then the dmz just becomes a stub network.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2018 06:46 AM - edited 01-06-2018 06:51 AM
Hi,
In twin firewalling case, How the local lan network traffic flow to outside .
Sorry I really don't undertand twin firewalling case .
If I am going for twin firewalling , how the traffic flow from inside to outside and dmz
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2018 07:17 AM
Once again there are many variations but in your picture 1, traffic from the lan will go through both firewalls to the internet.
lan traffic to the dmz will only traverse firewall B.
traffic fron the internet to dmz will only traverse firewall A.
traffic from the internet to lan (not recomended) will firstly traverse firewall A and then firewall B.
if you don’t understand it then you probably wont need it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2018 07:45 AM
To add to my previous post....
For lan traffic to internet....
firewall B will need to be the default gateway for lan.
firewall A will need to be the default gateway for firewall B.
firewall B will be aware of the dmz so will not use the default gateway.
my explanation is very very basic but you will need to add variuos routes and NAT for tis to perform correctly/securely.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2018 05:13 PM
Hi,
As per the diagram I posted in the first post , between FW A and FW B is the DMZ zone ,
So the lan traffic to internet should go through this zone ?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2018 01:04 AM
Yes in your diagram 1 the lan traffic will route across the dmz to the internet and your incoming traffic from the internet to the lan will take the same route.
we do not allow this on our network for security reasons but its up to you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2018 02:58 AM
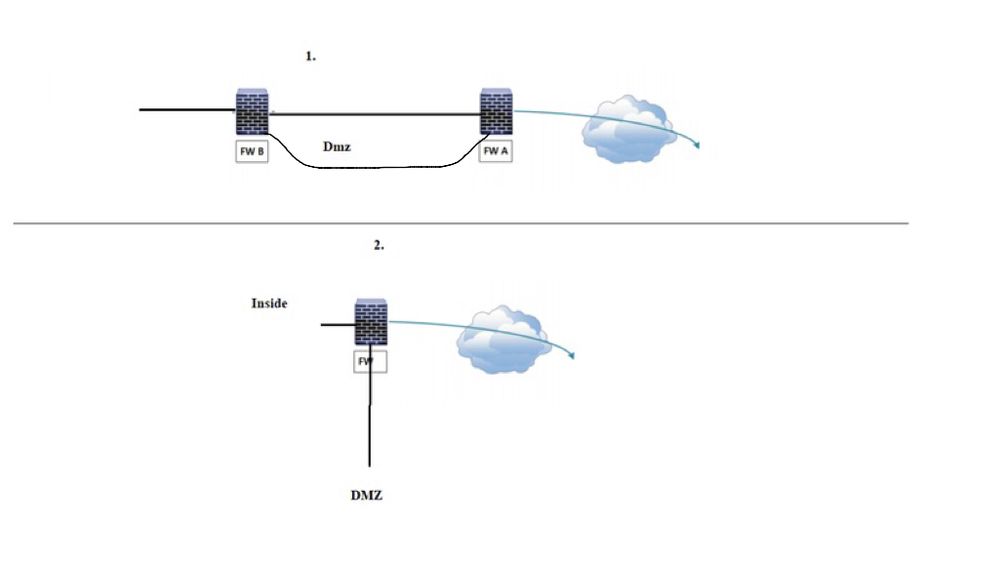
For your drawing 1 i would do as below.
this way the dmz is independant of your outgoing traffic flow.
the objective of a dmz is to allow sessions to it but no further.
you do not need the dmz on both firewalls you could have it on just one as per drawing 2 but this option will eliminate the trombone effect on the dmz interface.
please excuse my doodle, its an ipad.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2018 04:52 AM
Hi,
Thanks for your support .
One final question , You said " we do not allow this on our network for security reasons but its up to you"
Can you explain what are the security reasons
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2018 05:19 AM
Hi. No problem but please remember this is a forum and many others will have thier own interpretation of a dmz.
Regarding security...
for me.. no direct connection is allowed from the internet to our lan. It must go via the dmz.
even then it is not alowed to pass through the dmz to the lan.
for example.
lan to ftp server on dmz is allowed.
internet to ftp server on dmz is allowed.
intrenet to remote desktop on the lan is via rds or vdi gateway on dmz.
Internet web access to web server on lan is via reverse proxies on dmz.
The list is quite long but all of the above prevents a direct connection to the lan.
you can of course place your web servers, vdi farms on the dmz to keep it simple but my option saves the requirement of setting up domain trusts to the dmz.
All of the above can still be implemented with drawing 2 but for reverse proxies and vdi gateways this will double up traffic on the dmz interface.....tromboning, not sure if there is such a word.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2018 05:22 AM
Yes, it does exist.... just googled it....
laters.....
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2018 08:01 AM
Hi,
@Mick_Ball wrote:Hi. No problem but please remember this is a forum and many others will have thier own interpretation of a dmz.
Regarding security...
for me.. no direct connection is allowed from the internet to our lan. It must go via the dmz.
even then it is not alowed to pass through the dmz to the lan.
for example.
lan to ftp server on dmz is allowed.
internet to ftp server on dmz is allowed.
intrenet to remote desktop on the lan is via rds or vdi gateway on dmz.
Internet web access to web server on lan is via reverse proxies on dmz.
The list is quite long but all of the above prevents a direct connection to the lan.
you can of course place your web servers, vdi farms on the dmz to keep it simple but my option saves the requirement of setting up domain trusts to the dmz.
All of the above can still be implemented with drawing 2 but for reverse proxies and vdi gateways this will double up traffic on the dmz interface.....tromboning, not sure if there is such a word.
Can you tell me how the traffic will double up ?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-13-2018 08:34 AM
Ok the following example is for reverse proxy.
single firewall......
web requests enter the outside interface.
then routed to the dmz.
the reverse proxy on dmz then requests the web page from the lan via the same dmz interface,
so you have in and out traffic on the dmz interface.
twin firewall......
web requests enter the outside interface on firewall 1.
then routed to the dmz.
the reverse proxy on dmz requests the web page from the lan via the dmz interface on on firewall 2.
the same scenario applies to various other services within dmz, rdp gateways etc and even dns servers.
if you have just a web server on dmz then tromboning is not so much of an issue.
it all depends on your setup, data demands and services provided.
for a small to medium network, single firewall should suffice.
if your still having issues with the twin concept then happy to post a drawing on monday.
mick.
- 1 accepted solution
- 8821 Views
- 26 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Assistance with Design of Palo Alto Firewalls & Panorama in Panorama Discussions
- Should I override the intrazone-default to deny? in Next-Generation Firewall Discussions
- Multiple tunnel to single destination over multiple WAN connections. in General Topics
- URL filtering not working in Next-Generation Firewall Discussions
- GlobalProtect | External Gateway | SAML | Reconnect Issue in GlobalProtect Discussions