- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
how to configure wildfire to block a malicious file?
- LIVEcommunity
- Discussions
- General Topics
- Re: how to configure wildfire to block a malicious file?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
how to configure wildfire to block a malicious file?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2014 08:11 AM
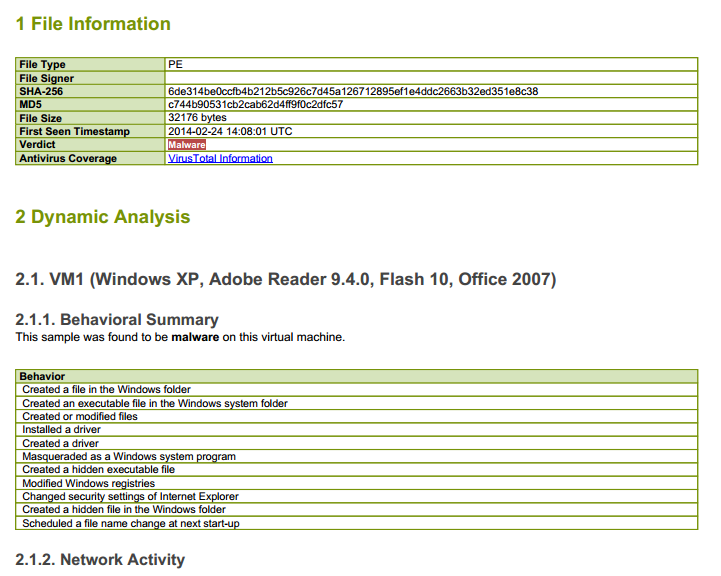
i used PA3020 and software version 6.0.0, wildfire version is 26818-33137
i configured wildfire action to block in antivirus profile and apply to security policy already.
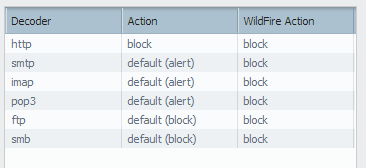
but, when i test to download a malicious files. the action is alert and i can download this file. why?
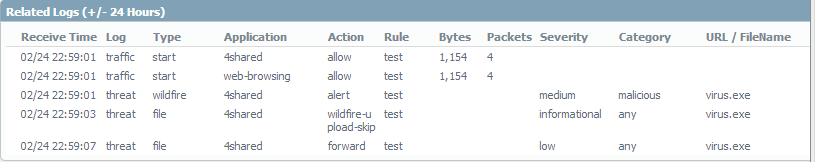
i don't know, what is wrong in my configure and i want to know, how to configure wildfire to block a malicious file.
- Labels:
-
App-ID
-
Configuration
-
Set Up
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2014 11:03 AM
i configured action in blocking profile to "forward".
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2014 08:35 PM
Wildfire report shows that the first time the malware was reported at 02-24 14:08 and the log shows alert for type wildfire at 22:59 with wildfire-upload-skip since the file has been already sent to wildfire cloud
If the firewall is equipped with a WildFire subscription then it can receive the new signatures within 30-60 minutes; firewalls with only a Threat Prevention subscription can receive the new signatures in the next antivirus signature update within 24-48 hours. Can you please confirm if you have valid license for wildfire? The wildfire version that you have is 26818-33137 and the latest available is 26836-33168.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-24-2014 08:45 PM
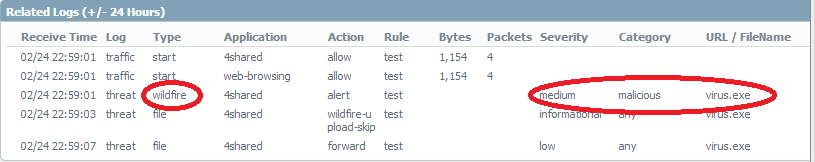
i try to test this virus.exe about 4 hours. and i download an update already.
and if you look at this pic. wildfire log is show "virus.exe" is malicious but action is alert, not block.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2014 08:34 PM
Hi thanachaip,
Nothing false in your configuration.
I got the same problem and already open case for it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2014 09:00 PM
Could you please share the case ID here.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2014 10:40 PM
Hi HULK,
My case number : 00189573.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2014 03:40 AM
Hi Hulk,
Not sure if there was a resolution to this issue but I am having the exact same issue and am getting nowhere with support.
Case ID: 00226681
Hoping maybe you can help?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2014 10:03 AM
I finally got my case escilated and am currently working on getting them more info. Will update when I know more.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2014 09:38 AM
Thanks JayD, looking forward to hearing more
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2014 09:44 AM
Antwoinne If you can, please create a ticket with your example and reference JayD 's Case ID: 00226681 when you do.
This will give support more data to work with for a solution.
Thanks for posting the information and tracking the issue for the rest of us.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- 8085 Views
- 18 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- What's the difference between antivirus signatures and WildFire signatures in Threat & Vulnerability Discussions
- Cortex XDR flagged malicious macros in Cortex XDR Discussions
- Cortex XDR in Cortex XDR Discussions
- Dynamic User Group Auto Remediation configuration in Next-Generation Firewall Discussions
- Cortex XDR agent and EICAR malware test file in Cortex XDR Discussions