What does the Bi-directional NAT Feature Provide?
Resolution
In the GUI, under Policies > NAT, there is a checkbox for Bi-directional when creating a static-IP source NAT translation.
Details
In this example, the Bi-directional NAT will be for a connection from a server in the Source Zone "Inside" to the Destination Zone Outside, with private address "A_private" and public address "A_public". The user outbound traffic will be doing source translation from private to public. Traffic destined to A_public from the outside, as well as from any other zone or address will do a destination translation to A_private. The following example displays the rule:
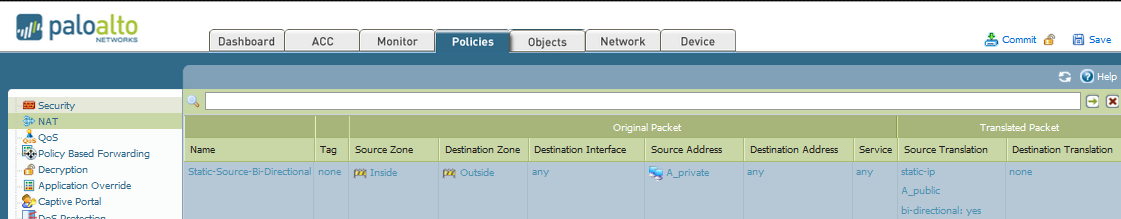
Note: With the Bi-directional option, the firewall still creates two rules, Source NAT and Destination NAT, that will count to the Devices Max Number of NAT rules. The two rules created with the Bi-directional option would be stated as follows:
- Source NAT
- Original Packet:
- Source-Zone Inside, Destination-Zone Outside, Source-Address A_private, Destination-Address ANY.
- Translated Packet:
- Source Translation Static-IP, Translated Address A_public.
- Original Packet:
- Destination NAT
- Original Packet:
- Source-Zone ANY (Inside and Outside or any other Zone), Destination-Zone Outside, Source-Address ANY, Destination-Address A_public,
- Translated Packet:
- Destination translation, Translated Address A_private.
- Original Packet:
For Bi-directional NAT translation, open the NAT policy rule and go to the Translated Packet tab. Under Source Address Translation, select Static-IP for Translation Type. For the Bi-directional option, select Yes or No based on the desired configuration:
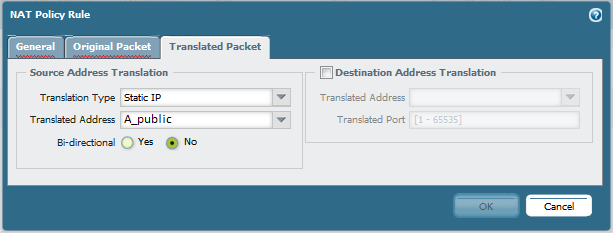
If the Bi-directional option is used, the given rule will be expanded into two rules as discussed above:
- The original source translation rule
- A destination translation rule
- The Destination NAT rule would have the following results from the example above:
- Original Packet:
- Source-Zone ANY to Destination-Zone Outside.
- Source address ANY to Destination address A_public; from the original rule translated Destination address
- Translated Packet:
- Destination address A_private; from the original rules Source address.
- Original Packet:
Note: The destination NAT rule that is created in a Bi-directional rule, the Source Zone and Source Address in the original packet will be ANY. This can break some traffic if the rule is set up as a Static Source NAT with Bi-Directional. For granular control over the Source and Destination NAT rules, create them separately. This may be necessary if the Bi-Directional NAT is not working in a given configuration.
Additional Information
Security Policy Configuration:
- For outbound access from Inside zone, the generic security policy to permit the Outside zone is required
- For inbound access from Outside zone, the security policy must match the following:
- Source and destination IP address as seen in the original packet
- Source zone: Incoming zone of the packet to the server
- Destination zone: zone where the server is physically connected