Separate Panorama Admins Access Domains using RADIUS
Resolution
Overview
The managed Panorama platform helps firewall admins manage many devices. In cases of managed security services, Palo Alto Networks devices can be isolated from one another. There is an option on Panorama to divide the device in Access Domains. The access domain specifies the domains for administrator access to the firewalls. It is linked to a VSA (Vendor-specific Attributes) RADIUS attribute to authenticate the users.
Separating different devices in different Access Domains is a good idea when multiple administrators have the option to log on the Panorama and manage their devices. This includes full access rights to Templates and the Device Groups for managed devices in the Access Domain.
Details
In this example configuration there will be 2 access domains to separate the devices. A RADIUS profile will be created, which will give access to only one access domain.
The configuration is done on a Panorama and a Windows RADIUS server, but the same principle is valid for a Palo Alto Networks M-100 device and any RADIUS server.
Note: The user needs to be logged in as superuser on the Panorama and as Full administrator on the windows server.
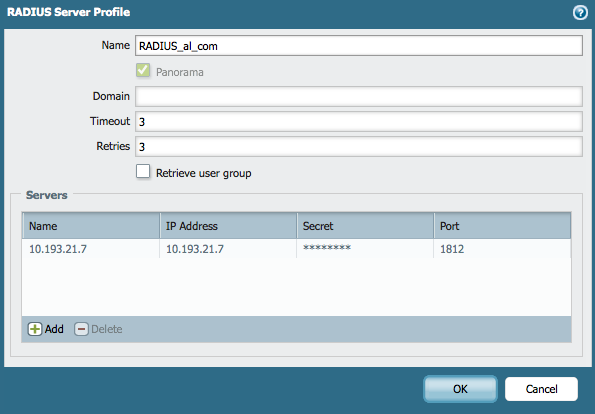
- Create a Radius Server Profile.Under Panorama > Server Profiles > RADIUS, create the profile that will be used for authentication for the Panorama administrators:
- Create the Authentication Profile.
Under Panorama > Authentication Profiles, create the RADIUS authentication profile: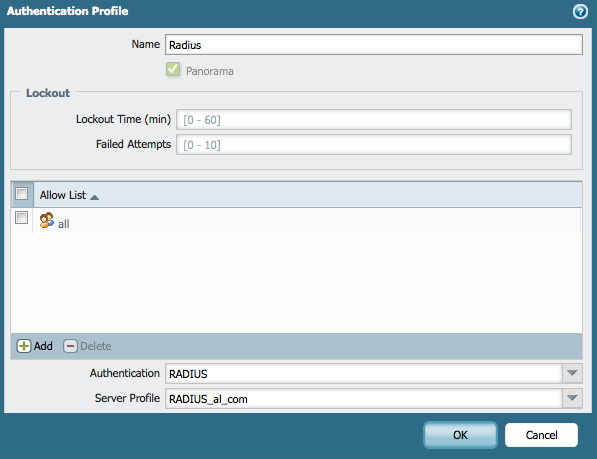
- Go to the RADIUS as an Authentication Profile that needs to be used.
Under Panorama > Setup > Management > Authentication Setting, select the created RADIUS Authentication Profile.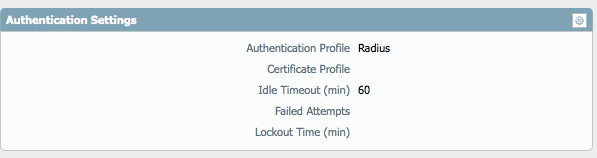
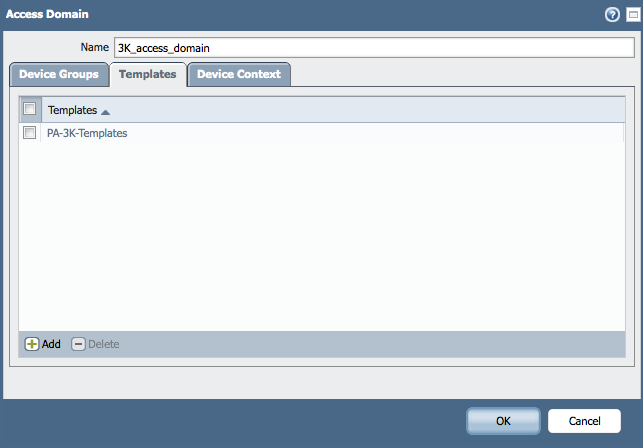
- Under Panorama > Access Domain, create the Access Domain:
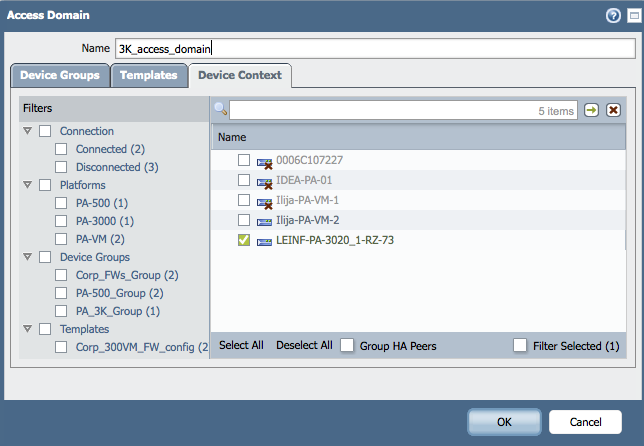
Chose the Device Groups, Templates, and Physical Devices and/or vsys you would like to include in this Access Domain: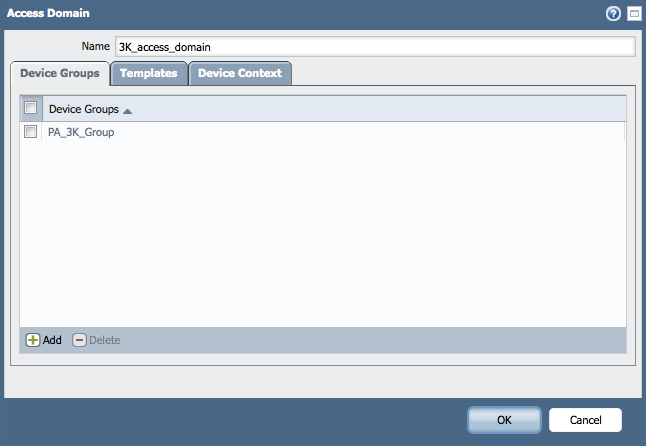
- Create the Admin Role.
Under Panorama > Admin Roles, create an admin role that will have the desired admin rights.
Note: Select "Device Group and Template" as a Role.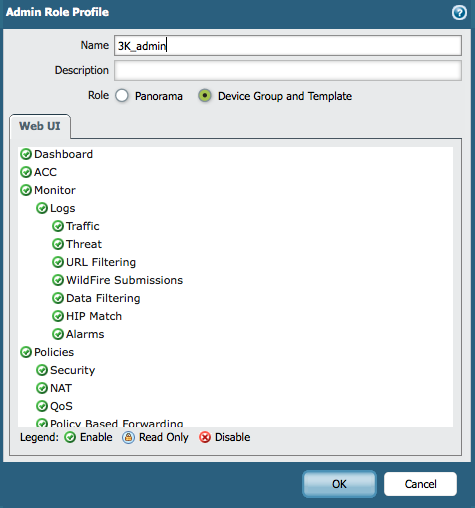
- Create the Policy on the Windows RADIUS Server.
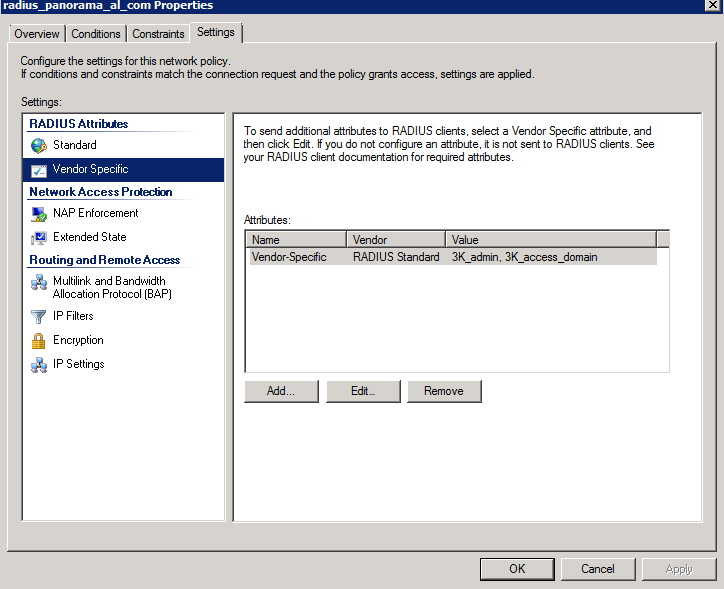
- Under NPS > Policies > Network Policies, create a policy to grant access to the user.
- In the policy, add the conditions and constrains if needed.
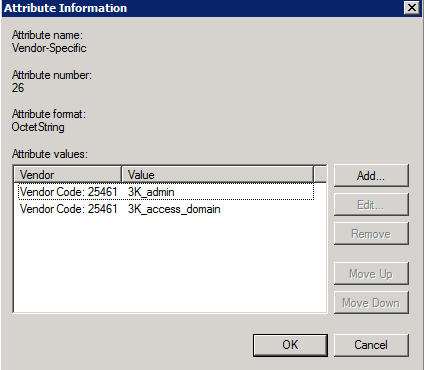
- In the policy proporties, under the settings tab, under the Vendor Specific, create the needed attributes for the authorization:
-use the Vendor atribute code: 25461
-for the VSA number 3, use the 3K_admin
-for the VSA number 4, use the 3K_access_domain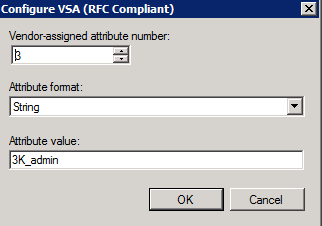
- Verify the setup.
In the authd.log, users logging in with the appropriate access domain and role are visible:
2014-09-17 20:15:55.524 +0200 debug: pan_authd_service_req(pan_authd.c:3316): Authd:Trying to remote authenticate user: emea
2014-09-17 20:15:55.524 +0200 debug: pan_authd_service_auth_req(pan_authd.c:1158): AUTH Request <'','','emea'>
2014-09-17 20:15:55.529 +0200 emea admin is being authed
2014-09-17 20:15:55.532 +0200 debug: pan_authd_handle_admin_auths(pan_authd.c:2245): Using auth prof Radius for admin emea
2014-09-17 20:15:55.532 +0200 debug: pan_authd_handle_admin_auths(pan_authd.c:2299): shared/Radius is auth prof is of type (auth profile)
2014-09-17 20:15:55.546 +0200 debug: pan_process_radius_auth(pan_authd.c:1088): Found vsa radius role 3K_admin for user emea
2014-09-17 20:15:55.546 +0200 debug: pan_process_radius_auth(pan_authd.c:1105): Found vsa radius access domain 3K_access_domain for user emea
2014-09-17 20:15:55.546 +0200 authentication succeeded for user <shared,Radius,emea>
2014-09-17 20:15:55.546 +0200 authentication succeeded for remote user <emea(orig:emea)>
...
2014-09-17 20:15:55.561 +0200 Request received to unlock shared/Radius/emea
2014-09-17 20:15:55.562 +0200 User 'emea' authenticated. From: 10.193.100.140.
2014-09-17 20:15:55.562 +0200 debug: pan_authd_generate_system_log(pan_authd.c:866): CC Enabled=False
2014-09-17 20:15:55.566 +0200 debug: pan_authd_service_req(pan_authd.c:3322): Authd:get group request
2014-09-17 20:15:55.566 +0200 debug: pan_authd_get_userinfo(pan_authd.c:3432): Found access domain (3K_access_domain) and role (3K_admin) for user emea
2014-09-17 20:15:55.566 +0200 debug: pan_authd_handle_group_req(pan_authd.c:3210): Got user role/adomain 3K_admin/3K_access_domain for user emea
2014-09-17 20:15:55.567 +0200 Error: pan_authd_handle_group_req(pan_authd.c:3223): Failed to get user pw profile settings
2014-09-17 20:29:29.438 +0200 debug: cfgagent_opcmd_callback(pan_cfgagent.c:418): authd: cfg agent received op command from server
Web UI verification
When the user now tries to logon to Panorama, access will be limited to the devices in the defined access domain.
This includes access to the templates, device groups, logs and changing context from the Panorama to the devices in the access domain.
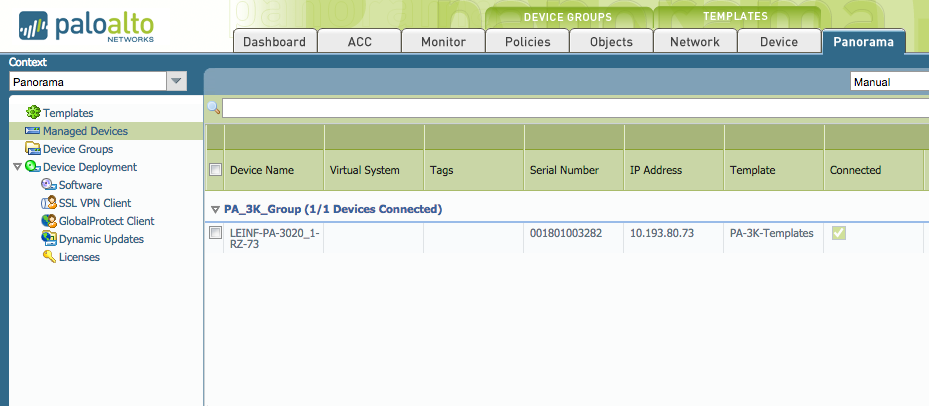
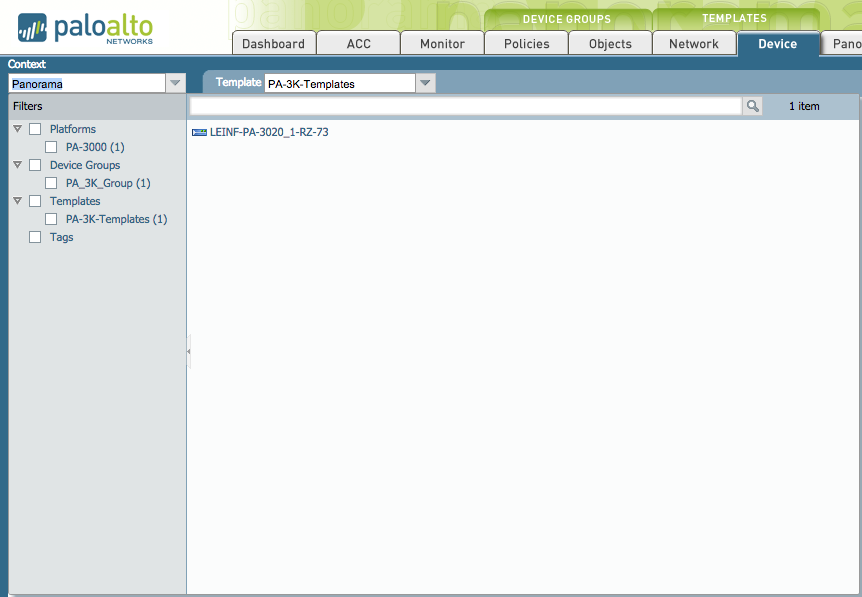
For example, managed devices shows only the devices in the 3K_access_domain:
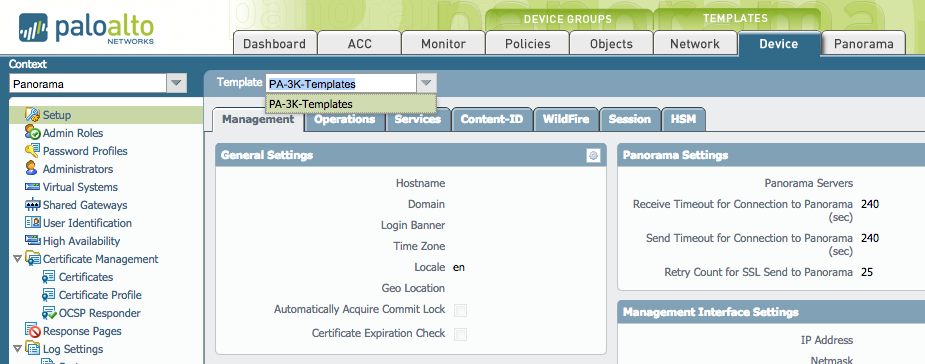
Only the PA-3000 template is shown in the list:
Only the devices in the 3K_access_domain are available to change context to:
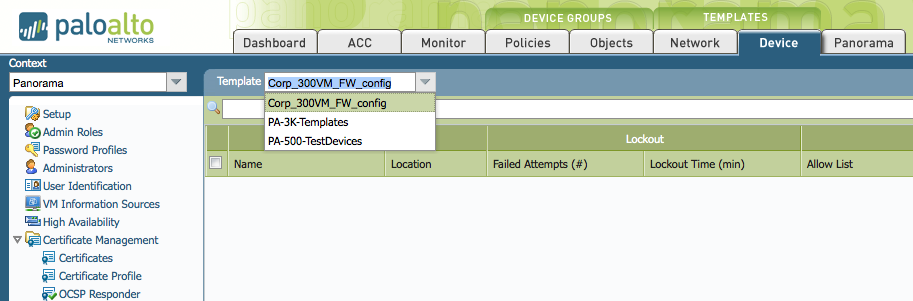
The full admin has rights to see all the Templates and Contexts:
Three templates are shown for the admin user.
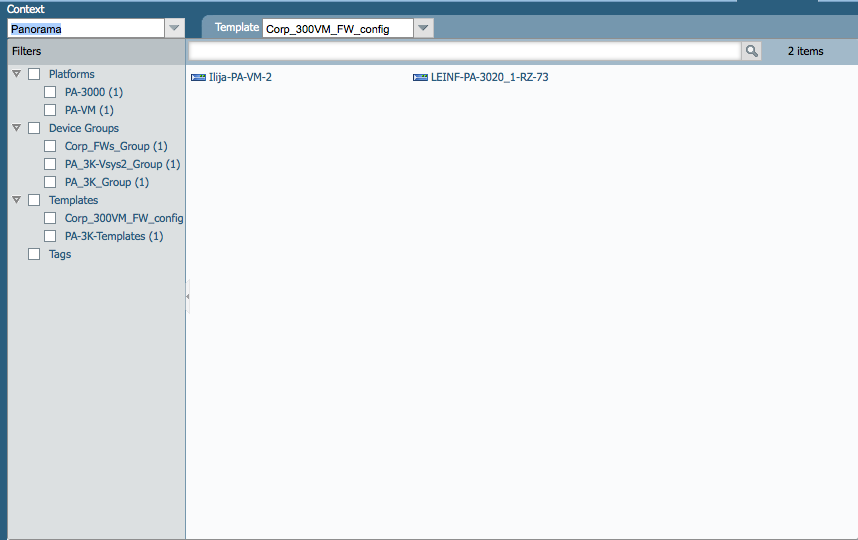
Two devices are available to be connected to via context change.
owner: ialeksov