In today's modern networks, a big majority of the traffic is DNS traffic. This is especially true for the perimeter devices, going towards the internet.
The DNS sessions are very short lived sessions and a query is sent and the response comes back really fast.
Since they are UDP sessions the firewalls don't have a way to track them and they don't know when no more traffic is going to be sent via them, so the closing of the sessions from the firewall's perspective is very hard.
That is why every firewall has a recommended value for a time-out which starts as soon as the UDP session is established and after it hits the value 0, the session is closed.
This value is usually 30seconds across all firewall vendors.
Since Palo Alto Networks does App-ID all the time, it has a time-out timer for the DNS traffic that is not the same as for usual UDP. This means that the timer can be changed if needed for the DNS application only and will not affect the other UDP traffic.
Issue
In networks where there is a high session count that comes close to the limit of the device, and a big majority of the traffic is DNS, the session timeout value can be changed from the default 30sec to a lower value. If ordered by the session, verify this by looking at the ACC statistics.
Solution
- Go to Objects > Applications.
- Search for DNS.
- Under the timeouts, change the value to an appropriate value for the given network.
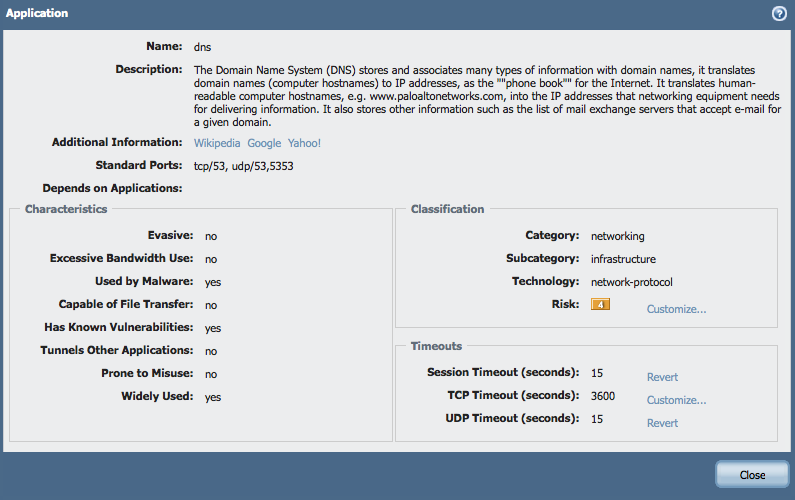
In the example above we have lowered the value to 15 seconds.
This will cause the DNS sessions to timeout faster and the sessions to be cleared from the session table faster, lowering the number of total concurrent sessions on the device too.
Make sure before going down to an extreme value that you do a test to see how fast the communication is actually done between the client and the server, so that the configured value is not too low, which causes the sessions to close on the firewall before the data is completely transfered.
In most of the cases 15 seconds is a good value, but tests are always recommended.