- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
which app and content code Petya ransomeware attack is mitigated
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: which app and content code Petya ransomeware attack is mitigated
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
which app and content code Petya ransomeware attack is mitigated
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2017 12:01 AM
want to know in which app and content release "Petya ransomware" attack is mitigated/protected. What code I should update it on to get the protection from this attack.
As os now, we are on 698-4026 app and content code. Please suggest.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-28-2017 10:52 AM
If you search Petya in the Threat Vault at https://threatvault.paloaltonetworks.com/ you will find the specific content release for Pre or Post 7.1.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2017 06:16 PM
Hi @vsingh
The below Palo Alto article gives you lots of good information on how to mitigate this threat.
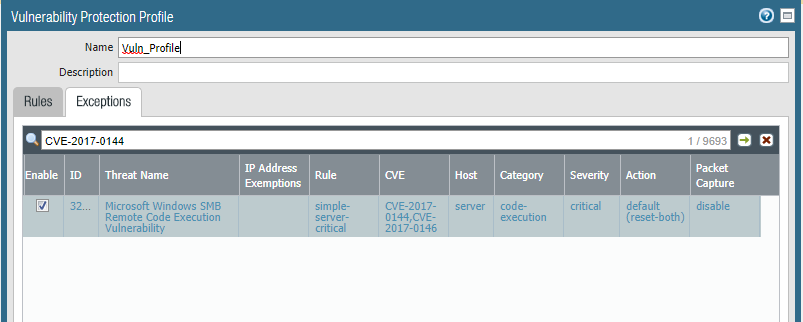
Also, make sure that your firewall has the following Vulnerability Protection signature enabled and applied to your security rules to prevent exploitation by the EternalBlue exploit.
https://researchcenter.paloaltonetworks.com/2017/06/palo-alto-networks-protections-petya-ransomware/
As for checking the AV signatures (Hashes) for this malware, as @Michael_Zook mentioned, go to https://threatvault.paloaltonetworks.com and type the name Petya in the search box, and it will list all contents for you.
I hope this helps
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2017 02:41 AM
by using which app &content or antivirus code bad rabbit ransomeware attack is mitigated.
- 6771 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!