- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Setting up an IPSEC VPN Tunnel on AWS
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: Setting up an IPSEC VPN Tunnel on AWS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2019 11:08 AM
Hi Palo Alto community,
I've been trying to follow this guide to set up a static IPSEC tunnel on AWS between two VPCs but having a bit of trouble:
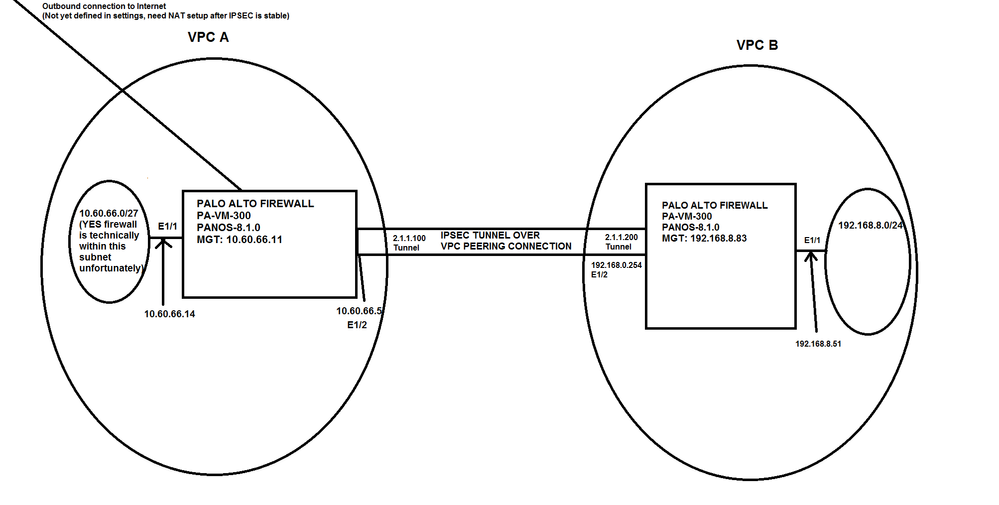
This is my network diagram:
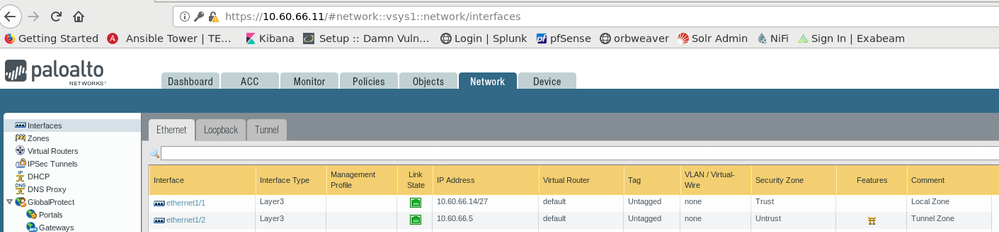
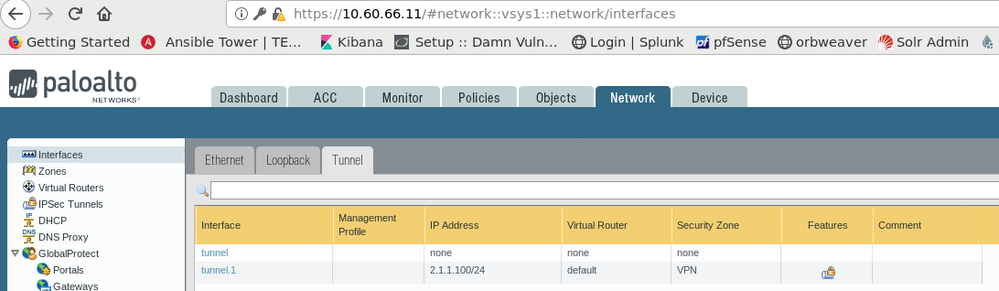
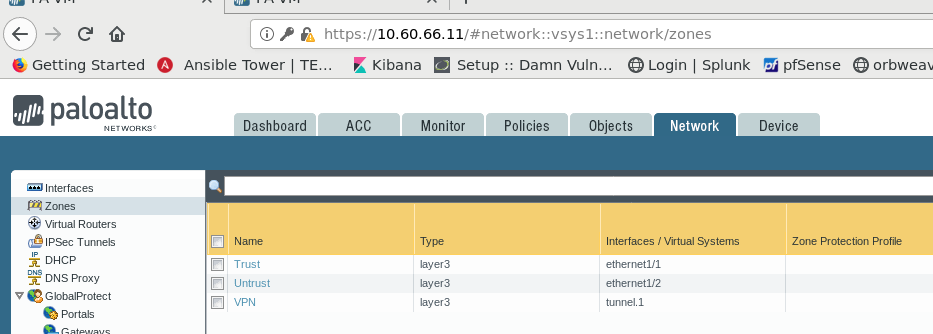
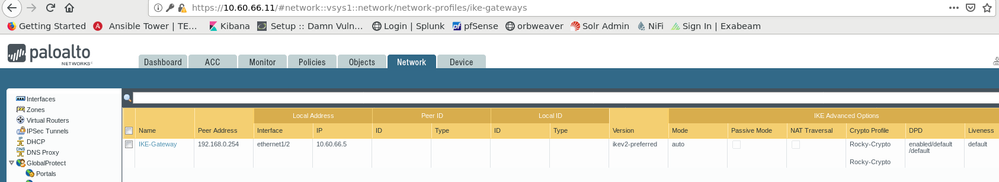
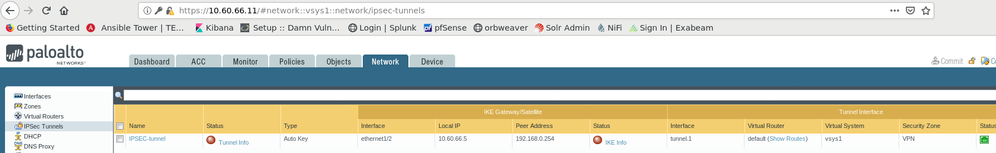
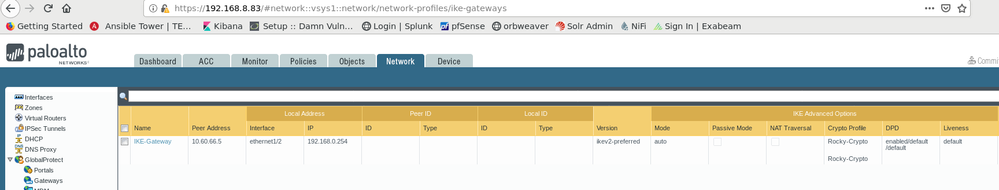
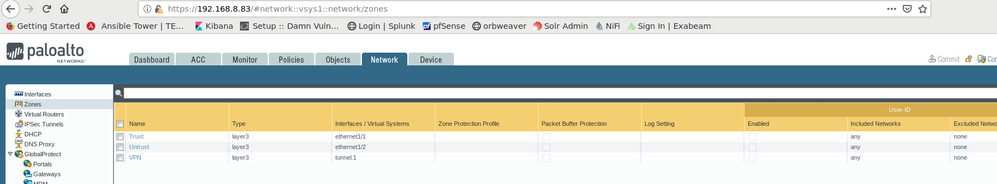
This is my configuration for the firewall in VPC A:
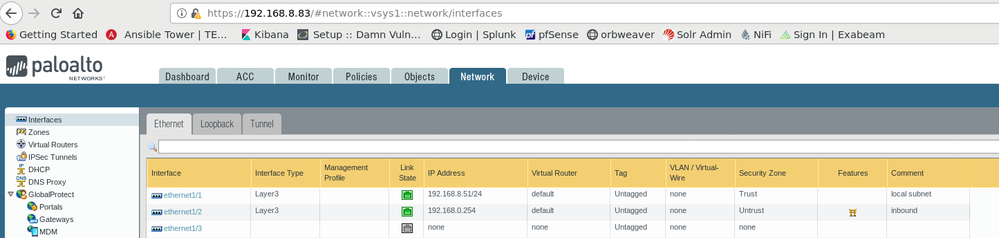
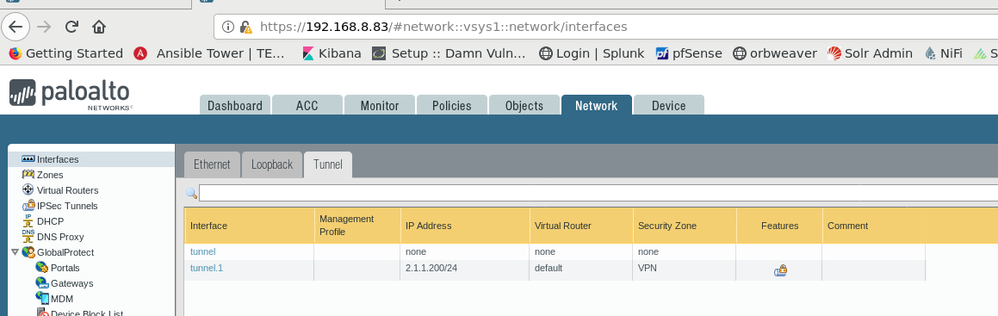
This is my configuration for the firewall in VPC B:
I had also added some firewall rules that weren't in the screenshots according to the guide but that didn't help turn the IPSEC tunnel status green either.
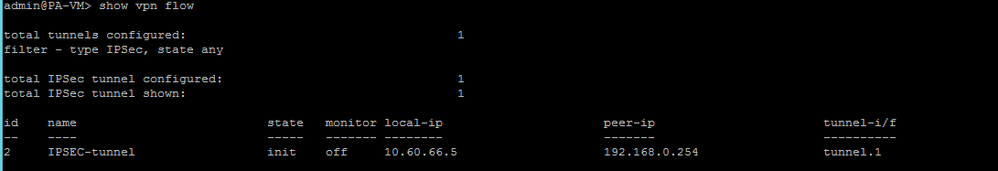
I also ran the command show vpn flow in the CLI but the state remains "init" on the tunnel:
Any suggestions would be appreciated, pretty new to using PA as I've been using mostly cisco/pfSense up to this point, thanks!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:10 AM
So the support team resolved it.. it was due to the tunnel endpoint sitting on the same subnet as the private subnet on VPC 1.. apparently you need some subnet indicator on the 10.60.66.14 or it won't know where the gateway is, even if you hardcode the ARP. We solved the issue by making another subnet at 10.60.0.0/24 and used that for E1/1 in VPC 1.
I also needed to setup static routing config on the virtual router for E1/1.
Finally, we needed to run the following two commands to manually initiate the tunnel.
test vpn ike-sa gateway [ike gateway name]
test vpn ipsec-sa tunnel [tunnel name]
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2019 02:56 PM
Hello,
Check the logs to see if the packets are getting from one pan to the other. If not it could be the AWS ACL firewall or your security groups are preventing the communication.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-27-2019 10:10 AM
So the support team resolved it.. it was due to the tunnel endpoint sitting on the same subnet as the private subnet on VPC 1.. apparently you need some subnet indicator on the 10.60.66.14 or it won't know where the gateway is, even if you hardcode the ARP. We solved the issue by making another subnet at 10.60.0.0/24 and used that for E1/1 in VPC 1.
I also needed to setup static routing config on the virtual router for E1/1.
Finally, we needed to run the following two commands to manually initiate the tunnel.
test vpn ike-sa gateway [ike gateway name]
test vpn ipsec-sa tunnel [tunnel name]
- 1 accepted solution
- 21062 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure Palo VM IPSec Tunnel to another Azure Palo VM in VM-Series in the Public Cloud
- Show IPsec tunnle uptime duration in Next-Generation Firewall Discussions
- Firewall has the IPSec tunnel but Panorama don't. How to fix? in Panorama Discussions
- Problem Using New Digitally Signed Certificate in GlobalProtect Discussions
- IPSEC Tunnel monitor for policy based site to site VPN in Next-Generation Firewall Discussions