
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
The content you are looking for has been archived. View related content below.
Special shoutout to Cyber Elite @reaper for his contribution to this blog!
It's considered best practice to create an Out Of Band (OOB) network for the management interfaces of your security appliances and services, so that they cannot be compromised.
But an OOB network can create interesting challenges. Your appliances may need to access resources that are not available on the secured network. One example is Palo Alto Networks' integrated User Identification mechanisms, where either the firewall reads security audit logs on an Active Directory server, or the server gets an agent software installed that does the reading and sends the output back to the firewall. If the AD server is not connected to the secured network, a different route needs to be taken to get that information on the firewall.
For this particular use case, a service route can be configured that redirects connections originating from the management plane, via the backplane, to the dataplane. This will force the outgoing connection to egress from a normal network interface without exposing the management interface (pretty cool, huh?).
To configure a service route:
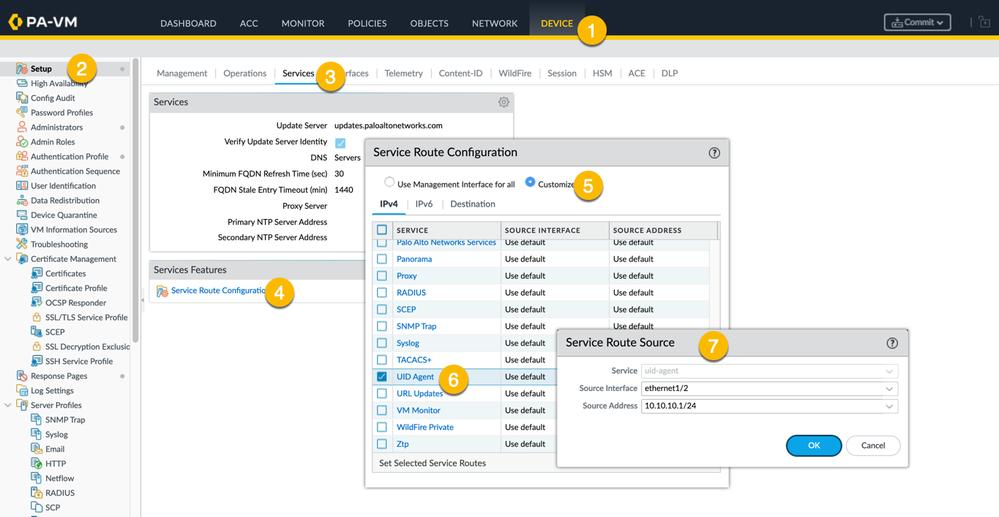
NOTE: This will work for both the installed UID agent software and the clientless configuration on the firewall.
So, have you configured any service routes?
Feel free to share your questions, comments and ideas in the section below.
Thank you for taking time to read this blog.
Don't forget to hit the Like (thumbs up) button and to Subscribe to the LIVEcommunity Blog area.
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 8 Likes | |
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |




