
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
As the attack surface keeps getting bigger and attacks are becoming more and more sophisticated, threats are a huge concern for any security professional.
The amount of information you get might be overwhelming and it might be difficult to know where to start.
So let's start with the Threat Logs. You will find these inside the WebGUI > Monitor > Threat tab. There, you'll see events ranging from informational to critical in severity. See the example below, where I'll use a Critical event as an example.
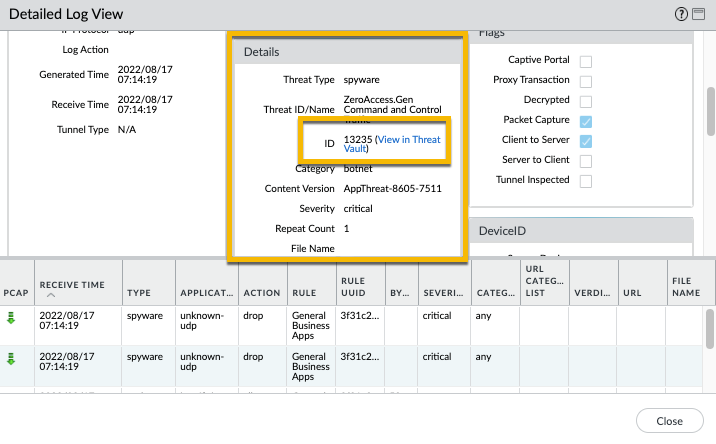
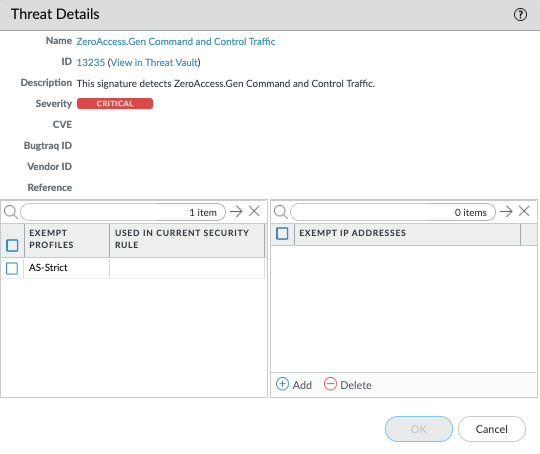
To the right of the name of the threat itself is a small dropdown arrow which will show 'Exception' and 'Autofocus' when you click it. If you click Exception the Threat Details will popup, which shows additional information such as Name, ID, Description, Severity, CVE, Bugtraq ID, Vendor ID, and Reference link to the CVE info. You can also exempt Security Profiles or IP addresses in the lower part of the window. If you click the Autofocus menu you'll get a graphical overview of threat intelligence that AutoFocus compiles to help you assess the pervasiveness and risk of the threat. To view the AutoFocus Intelligence Summary window, you must first have an active AutoFocus subscription and enable AutoFocus threat intelligence (select Device > Setup > Management and edit the AutoFocus settings).
You can also filter out specific entries and leave out informational and low risk threat logs. To filter, first click on the severity, and in the search window at the top of the screen, change the severity level to what you'd like to see. In this example we would like to see all the critical events so we used the filter (severity eq critical). Apply the filter by clicking the arrow at the top right.
Alternatively, you have the ability to see all the same information about a specific threat if you visit our threat vault at https://threatvault.paloaltonetworks.com and search on the Threat ID. Using the example from earlier, you can search on 13235.
Note: You can also go to the threat vault directly from the information in the threat logs using the 'View in Threat Vault' link.
For more information on how to use the threat vault check out the following video:
If you're looking for a more automated threat intelligence platform then I recommend checking out MineMeld or Cortex XSOAR.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 8 Likes | |
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |
| User | Likes Count |
|---|---|
| 16 | |
| 8 | |
| 3 | |
| 2 | |
| 2 |




