
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources

The Palo Alto Networks next-generation firewall supports custom vulnerability signatures using the firewall's threat engine. You can write custom regular expression patterns to identify vulnerability exploits. The resulting vulnerability patterns become available for use in vulnerability security profiles. The firewall looks for the custom-defined patterns in network traffic and takes the specified action for the vulnerability exploit.
You can define signatures for Vulnerability Protection profiles with the following steps.
Add the Custom Vulnerability Object by going to the Objects tab > select Vulnerability > add Custom Objects as shown below.
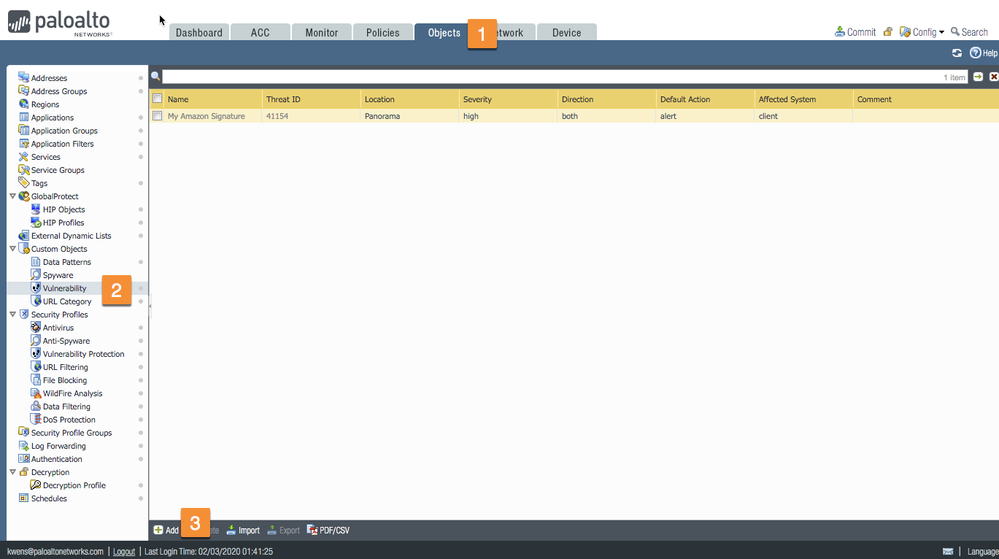
In the customer vulnerability signature popup, fill out the required information on the Configuration tab. In this use case, I'll show you how to match on a specific browser version.
Threat ID: A numeric identifier. For vulnerability signatures, the range is 41000-45000.
Name: Specify the threat name.
Severity: Assign a level that indicates the seriousness of the threat.
Direction: Indicate whether the threat is assessed from the client to server, server to client, or both.
Next, go to the Signatures tab to add a signature (1), then select the Standard radio button and click Add (2).
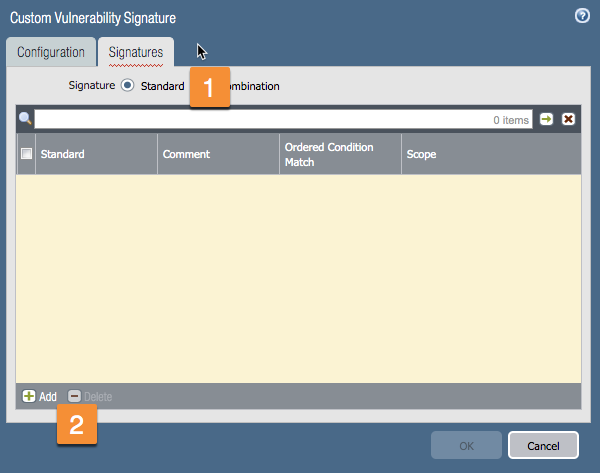
In the Standard window, complete the following steps:
In the next window ,we'll specify your signature match.
Operator: Defines the type of condition that must be true for the custom signature to match to traffic. Choose from Less Than, Equal To, Greater Than, or Pattern Match operators.
When choosing a Pattern Match operator, specify for the following to be true for the signature to match to traffic:
In this example, we'll look for the pattern match "Chrome/" in the Context field 'http-req-headers' as shown in the example below.
If you take a packet capture while browsing with a Google Chrome browser, you will find the following pattern match in the capture.
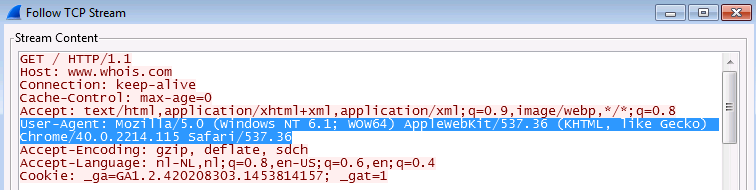
Click OK to create your custom vulnerability.
Enable your signature
NOTE: The custom signature will not be enabled by default.
To enable your custom signature, go to the Vulnerability Protection Security Profile. Edit your profile. On the Exceptions tab, search for the Threat ID and enable it.
Inside the WebUI, start at Objects > select Vulnerability Protection > select the Alert > Exceptions tab > enter Threat ID > check Enable. (Note: If your signature does not show up, please select "Show all signatures" in the lower left of the Profile window.)
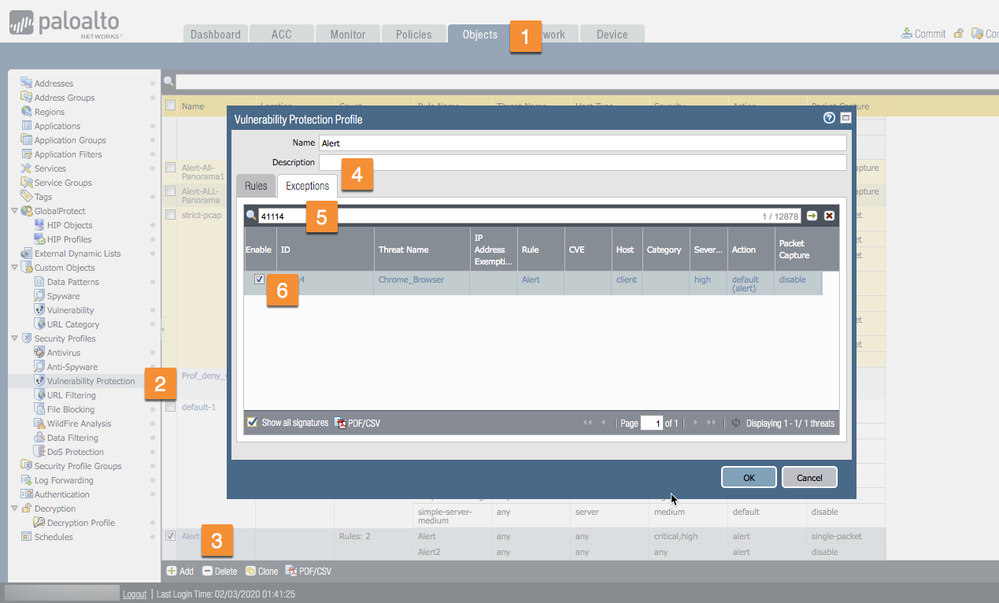
After committing this change, you will get alert messages in your Threat Log when you are browsing with a Google Chrome browser. Of course, you could use this signature to block traffic if you change the Action column to Block.
Here's a video about Custom Vulnerability in our Knowledge Base.
Below are some additional links with other use cases and useful information:
Custom Vulnerability Signature to Detect FTP Active Mode
Custom Vulnerability Signature for Identifying Windows XP
List of Different User-Agent Strings
Thanks for taking time to read the blog.
If you enjoyed this, please hit the Like (thumbs up) button, don't forget to subscribe to the LIVEcommunity Blog.
As always, we welcome all comments and feedback in the comments section below.
Stay Secure,
Kiwi out!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |




