
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
This week's Tips & Tricks column rings in the new year by discussing how to get the most out of your security profiles by enabling "Packet Capture" on Security Profiles.
One security feature that is sometimes overlooked by security professionals is the Packet Capture option inside of the Security Profiles. This option is intended to be available in the event you need to report any False Positive or to troubleshoot any other issue with the behavior of the Security Profiles—more specifically, Antivirus, Anti-Spyware and Vulnerability Protection profiles. Enabling this option captures the data that our inspection engine tags as a threat.
To enable the features, inside of the WebGUI, go to Objects > Security Profiles > Antivirus Profile.
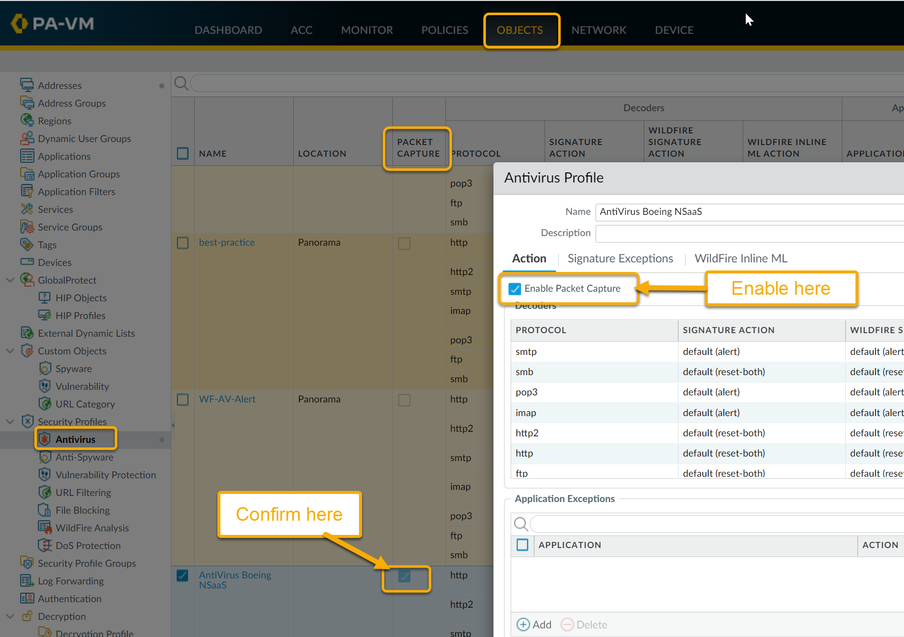
Then select the Antivirus Profile you want to enable captures on.
Select the check box if you want to capture identified packets. After hitting OK, you can confirm that the Profile you just modified has the Packet Capture enabled by looking for the checkmark in the "PACKET CAPTURE" column.
Next is the Anti-Spyware Profile. Which can be found inside of the Objects > Security Profiles > Anti-Spyware.
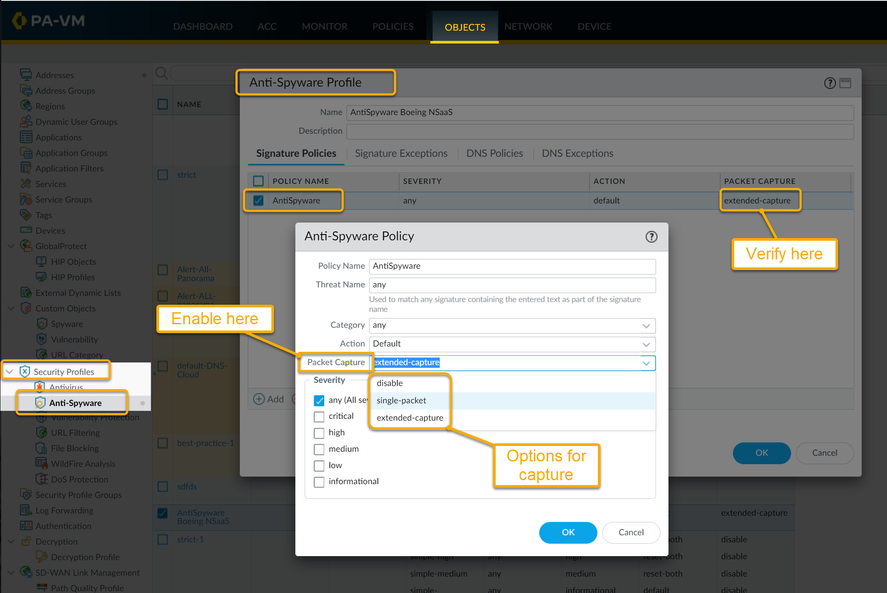
Select the Signature profile – policy name, and inside there you will find the the options for Packet Capture, along with the option to select either a single packet, or an extended capture to gather more data (if needed).*
Next is the Vulnerability Protection Profile, which can be found inside of Objects > Security Profiles > Vulnerability Protection. Select the profile you want to enable captures on.
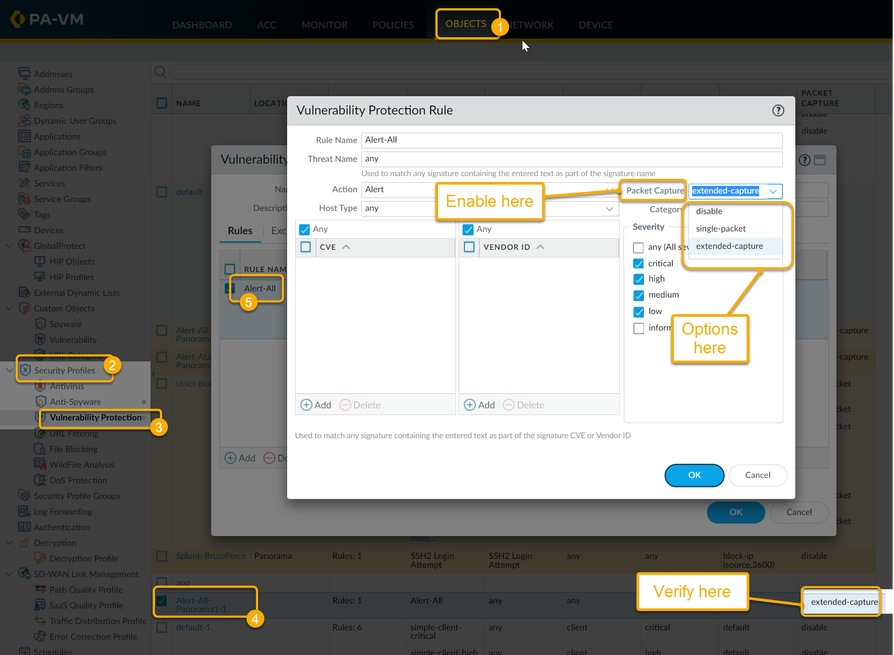
On the profile you are given the option to choose disable, single-packet, or extended packet capture.*
Inside of the Vulnerability Protection Profile under Exceptions, you will see that for any exceptions you also have the ability to define packet captures.
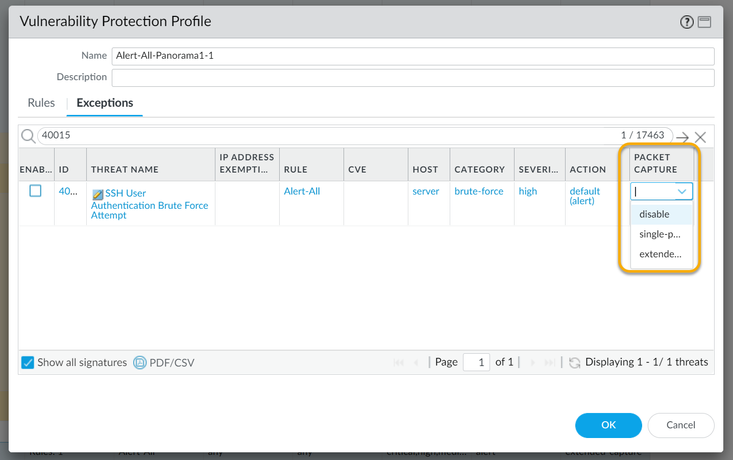
*Notice that Anti-Spyware and Vulnerability Protection have more options:
To define the number of packets that should be captured, navigate to Device > Setup > Content-ID Settings and then click the edit (Sprocket) the Option for number of packets to capture is listed under Extended Packet Capture Length (packets).
Set the number of packets to capture when the extended-capture option is enabled in anti-spyware and vulnerability protection profiles. The range is 1-50 and the default is 5.
To view the packet capture, navigate to Monitor > Logs > Threat and locate the log entry you are interested in and then click the green down arrow in the second column. Packet captures will only occur if the action is allow or alert, and the green arrow is only shown when a packet capture has been obtained.
Note: If the block action is set, the session is ended immediately.
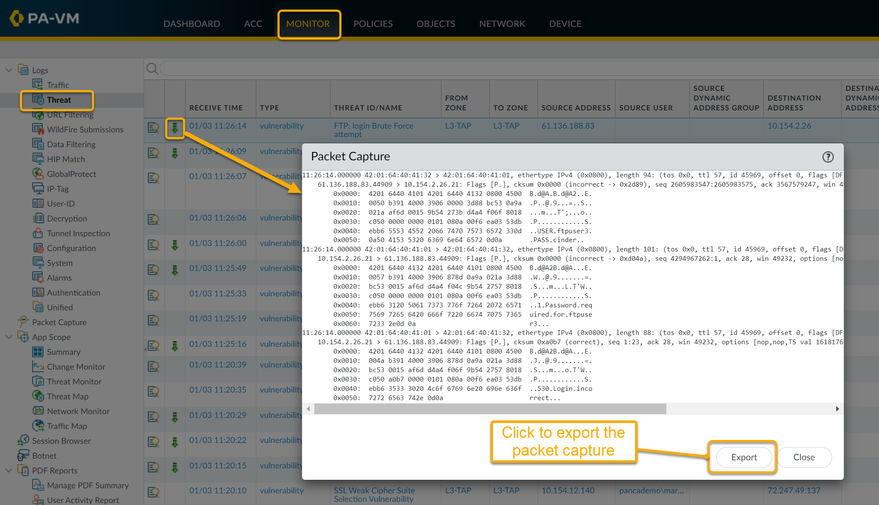
For all packet captures that you see inside of the Threat logs, you have an option to "Export" the captures. This will save the file locally on the client machine used to access the WebGUI.
I hope this helps you understand the packet captures more!
Thanks for taking time to read my blog.
If you enjoyed this, please hit the Like (thumb up) button, don't forget to subscribe to the LIVEcommunity Blog area.
As always, we welcome all comments and feedback in the comments section below.
Stay Secure,
Joe Delio
End of line
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 2 Likes |




