- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tips and Tricks: Filtering the Security Policy
- LIVEcommunity
- Articles
- General Articles
- Tips and Tricks: Filtering the Security Policy
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
The content you are looking for has been archived. View related content below.
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 01-16-2024 12:30 PM
Digging into the depths of policy details can be quite the task, especially after a long and tiring day. But fear not, handy search tools are here to lighten your load!
Here's how it works: Simply pop in a keyword related to what you're hunting for. This could be the name of a policy (just squish it into one word), an IP address or object name, maybe an application, or even a service.
Keep in mind though, wildcards (like *) aren't supported. You'll need a partial or an exact match.
Add a partial IP address and you'll get all the partial and exact matches in the result:
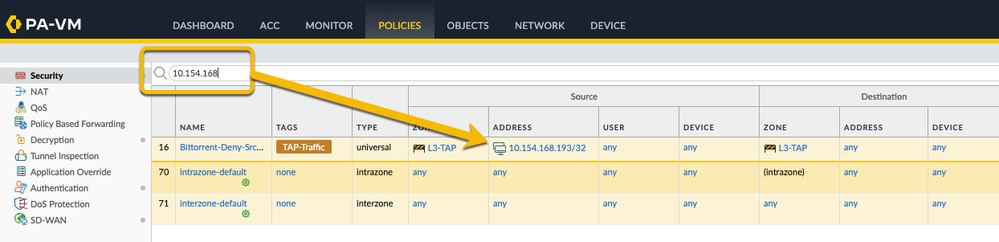
Want to narrow things down even further? You can target your search to specific fields like the source zone or application. And guess what? There’s a super handy drop-down function that sets up your search filter in a snap. Easy-peasy!
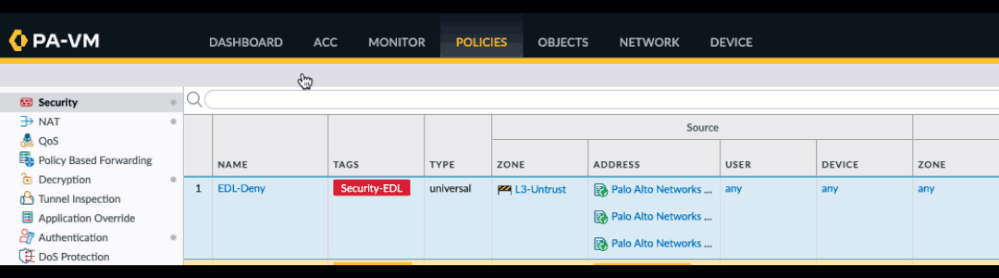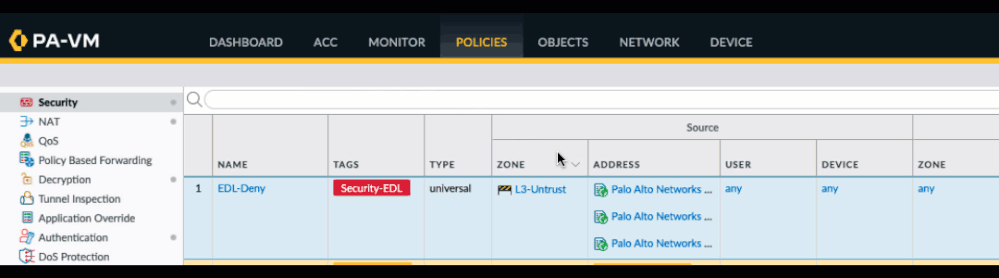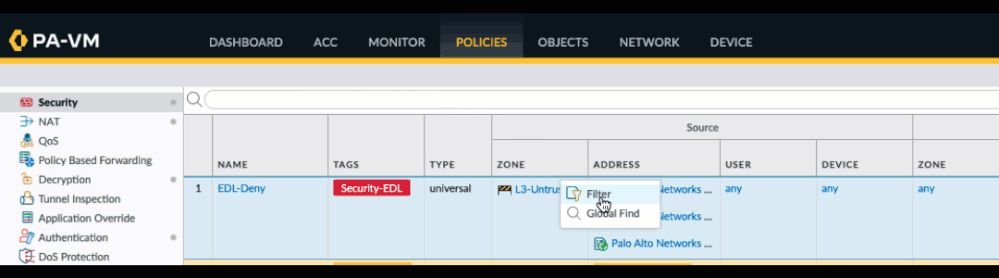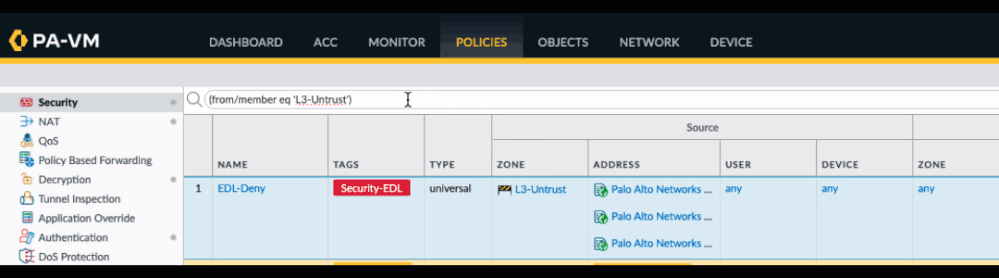
You can also create a search string manually. I've provided a list of all fields below:
Name: (name contains 'unlocate-block')
Tags: (tag/member eq 'tagname')
Type: (rule-type eq 'intrazone|interzone')
Source Zone: (from/member eq 'zonename')
Source Address: (source/member eq 'any|ip|object')
Source User: (source-user/member eq 'any|username|groupname')
Hip profile: (hip-profiles/member eq 'any|profilename')
Destination Zone: (to/member eq 'zonename')
Destination Address: (destination/member eq 'any|ip|object')
Destination User: (destination-user/member eq 'any|username|groupname')
Application: (application/member eq 'any|applicationname|applicationgroup|applicationfilter')
Service: (service/member eq 'any|servicename|application-default')
URL Category: (category/member eq 'any|categoryname')
This is a destination category, not a URL filtering security profile
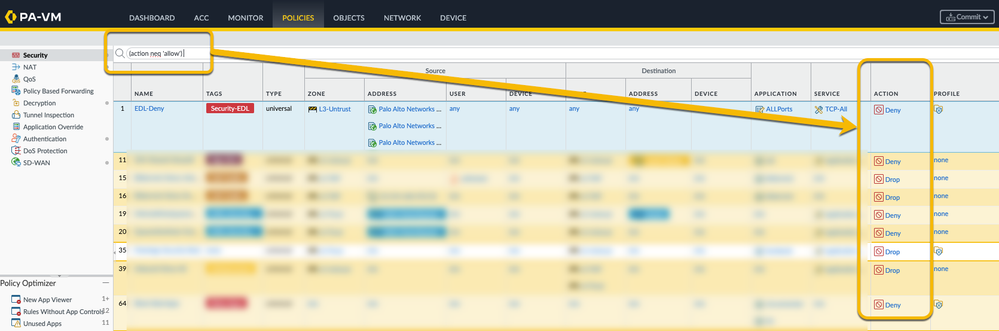
Action: (action eq 'allow|drop|deny|reset-client|reset-server|reset-both')
Action send ICMP unreachable: (icmp-unreachable eq 'yes')
Security Profiles:
(profile-setting/profiles/virus/member eq 'profilename')
(profile-setting/profiles/spyware/member eq 'profilename')
(profile-setting/profiles/vulnerability/member eq 'profilename')
(profile-setting/profiles/url-filtering/member eq 'profilename')
(profile-setting/profiles/file-blocking/member eq 'profilename')
(profile-setting/profiles/wildfire-analysis/member eq 'profilegroupname')
(profile-setting/group/member eq 'profilename')
Disable server response inspection: (option/disable-server-response-inspection eq 'yes')
Log at session start: (log-start eq 'yes|no')
Log at session end: (log-end eq 'yes|no')
Schedule: (schedule eq 'schedulename')
Log Forwarding: (log-setting eq "forwardingprofilename')
Qos Marking: (qos/marking/ip-dscp eq 'codepoint')
(qos/marking/ip-precedence eq 'codepoint')
(qos/marking/follow-c2s-flow eq '')
Description: (description contains '<keyword>')
Disabled policy: (disabled eq yes|no)
policies will only respond to 'no' if they have been disabled before
As you can see in the examples above the operands are 'contains' and 'eq' (=equals).
Note that you can also use the negate option using the operand 'neq' (=not equals).
For example, here's how you can use the negate option to list all the rules that do NOT have a ALLOW action: (action neq 'allow'):
Tag Browser can also come in very handy if you're able to tag all your security policies. It can be used in a similar way as the search function and display only the selected tags.
More information and a tutorial video on the Tag Browser can be found here: Tutorial: Tag Browser
Hope this was helpful, feel free to ask questions or post remarks below.
Thanks for taking time to read this blog.
Don't forget to hit that Like (thumbs up) button and don't forget to subscribe to the LIVEcommunity Blog.
Stay Secure,
Kiwi out!
- 8577 Views
- 1 comments
- 5 Likes
- Hybrid and Multi Cloud Connectivity with PAN-OS SD WAN in General Articles
- Nominated Discussion - Automatically blocking IP's after a certain number of Global Protect pre-login failures? in General Articles
- Using XFF Headers with VM-Series on GCP in General Articles
- Tips & Tricks: Packet Buffer Protection (PBP) in General Articles
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
2 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
Chrome Search Extension
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Commit Process
1 -
Community News
1 -
Configuration
9 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
4 -
COVID-19
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
1 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
Education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
events
1 -
expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
Github
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
2 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
2 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
log forwarding
1 -
Log4Shell
1 -
Logging
1 -
login
1 -
Logs
2 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
microsoft
2 -
Microsoft 365
1 -
minemeld
25 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
Network Security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
next-generation firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
4 -
NGFW
21 -
NGFW Configuration
10 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
17 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
Panorama
7 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
Prisma Access
5 -
Prisma SD-WAN
1 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
2 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
7 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
Tags
2 -
Terraform
2 -
TGW
3 -
threat log
1 -
threat prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
1 -
Troubleshooting
3 -
tunnel
1 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
6 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
3 -
Webinar
1 -
WildFire
2 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next




