
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Palo Alto Networks is pleased to announce the General Availability of integration of VM-Series virtual firewalls with Microsoft Azure Gateway Load Balancer. This integration has been designed to efficiently augment native Microsoft Azure network security capabilities with next-generation threat protection — so customers can more easily attain greater performance and scalability.
Load balancing is critical for evenly distributing loads of incoming network traffic across a group of backend resources or servers. With Azure Load Balancer, you can scale your applications and create highly available services.
But as organizations move more and more workloads into the cloud, setting up security becomes a top-of-mind concern. With this integration, VM-Series virtual Next-Generation firewalls augment native Microsoft Azure network security capabilities with next-generation threat protection. This includes preventing exploits, malware, previously unknown threats, and data exfiltration to keep apps and data in Azure safe.
That’s why Palo Alto Networks is proud to offer the VM-Series software firewall integration with Azure Gateway Load Balancer, which provides simplified connectivity while ensuring secure support for critical zone-based policies for Internet ingress traffic.
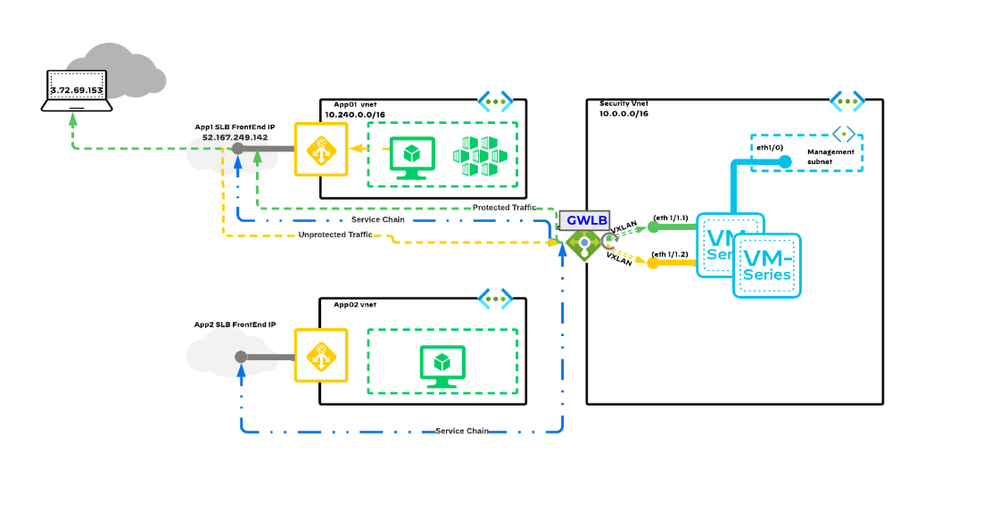
Truly securing traffic ingress requires complete visibility of the traffic source’s identity as it travels to its destination in the cloud. This was previously difficult to achieve with inbound traffic. When VM-Series firewalls are deployed behind a public standard load balancer, the source IP addresses of inbound traffic are replaced with the IP address of the load balancer. As a result, application source identity is obfuscated.
But with the new VM-Series and Azure Gateway Load Balancer integration, traffic packet headers and payload are kept intact, which provides complete visibility of the source’s identity as it travels to its destination.
The integration is designed to be fast and non-disruptive. You can continue to use your Hub VNET for centralizing your security by leveraging the Azure Gateway Load Balancer to scale and load-balance traffic across a stack of VM-Series firewalls. Plus, Gateway Load Balancer helps segment Internet-bound traffic from the VNET-bound traffic.
What this means is that you can now assign a trust zone to the VNET-bound traffic and the untrust-zone for the Internet bound traffic – and enhance security posture by continuing to author next-generation zone-based policies.
In addition, the VM-Series integration with Azure Gateway Load Balancer is also designed to provide the following customer benefits:
We encourage you to try out the integration of the VM-Series/Azure GWLB integration using PAN-OS version 10.1.4 or later in Azure Marketplace or on GitHub. You can download the VM-Series and Azure GWLB Deployment Guide PDF below.
You can also find more information on how VM-Series adds a critical layer of protection to Azure environments on the LIVEcommunity Azure resource page. And to get a personalized demo tailored to your specific needs, sign up here to discover how to secure your Azure investments.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 1 Like | |
| 1 Like |




